Page 89 - Cyber Defense eMagazine October 2023
P. 89
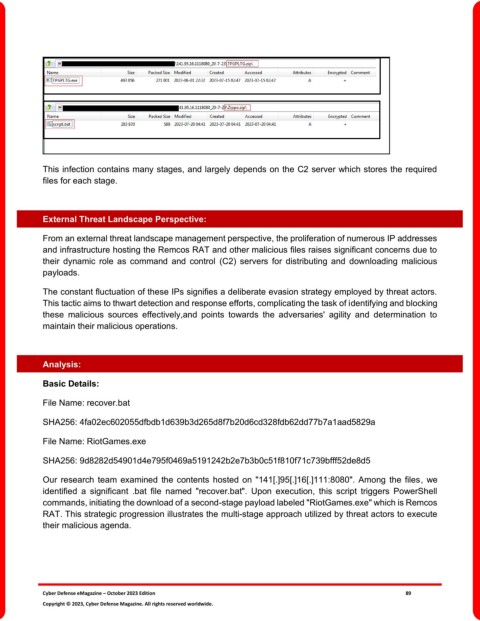
This infection contains many stages, and largely depends on the C2 server which stores the required
files for each stage.
External Threat Landscape Perspective:
From an external threat landscape management perspective, the proliferation of numerous IP addresses
and infrastructure hosting the Remcos RAT and other malicious files raises significant concerns due to
their dynamic role as command and control (C2) servers for distributing and downloading malicious
payloads.
The constant fluctuation of these IPs signifies a deliberate evasion strategy employed by threat actors.
This tactic aims to thwart detection and response efforts, complicating the task of identifying and blocking
these malicious sources effectively,and points towards the adversaries' agility and determination to
maintain their malicious operations.
Analysis:
Basic Details:
File Name: recover.bat
SHA256: 4fa02ec602055dfbdb1d639b3d265d8f7b20d6cd328fdb62dd77b7a1aad5829a
File Name: RiotGames.exe
SHA256: 9d8282d54901d4e795f0469a5191242b2e7b3b0c51f810f71c739bfff52de8d5
Our research team examined the contents hosted on "141[.]95[.]16[.]111:8080". Among the files, we
identified a significant .bat file named "recover.bat". Upon execution, this script triggers PowerShell
commands, initiating the download of a second-stage payload labeled "RiotGames.exe" which is Remcos
RAT. This strategic progression illustrates the multi-stage approach utilized by threat actors to execute
their malicious agenda.
Cyber Defense eMagazine – October 2023 Edition 89
Copyright © 2023, Cyber Defense Magazine. All rights reserved worldwide.