Page 85 - Cyber Defense eMagazine October 2023
P. 85
ETLM Attribution
Identified IPs Hosting Remcos RAT:
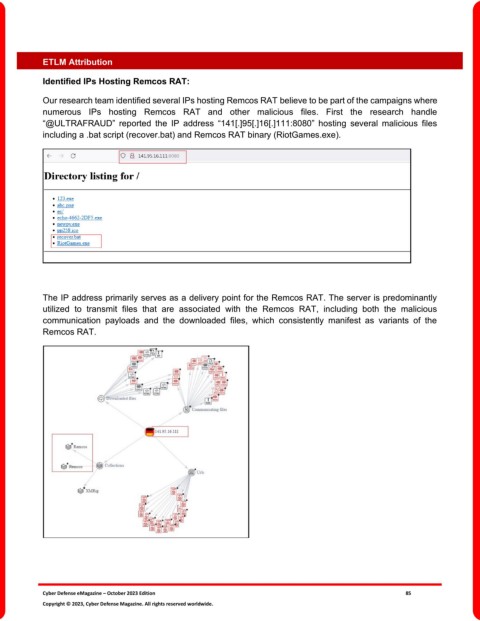
Our research team identified several IPs hosting Remcos RAT believe to be part of the campaigns where
numerous IPs hosting Remcos RAT and other malicious files. First the research handle
“@ULTRAFRAUD” reported the IP address “141[.]95[.]16[.]111:8080” hosting several malicious files
including a .bat script (recover.bat) and Remcos RAT binary (RiotGames.exe).
The IP address primarily serves as a delivery point for the Remcos RAT. The server is predominantly
utilized to transmit files that are associated with the Remcos RAT, including both the malicious
communication payloads and the downloaded files, which consistently manifest as variants of the
Remcos RAT.
Cyber Defense eMagazine – October 2023 Edition 85
Copyright © 2023, Cyber Defense Magazine. All rights reserved worldwide.