Page 86 - Cyber Defense eMagazine Annual RSA Edition for 2024
P. 86
allowing it to detect more complex, multi-vector attacks that might bypass endpoint-only security
measures.
While EDR is fairly resource-demanding, XDR’s comprehensive approach implements an integrated
security strategy. Thereby, XDR reduces the administrative burden on security teams by providing
deeper context and enhanced detection capabilities.
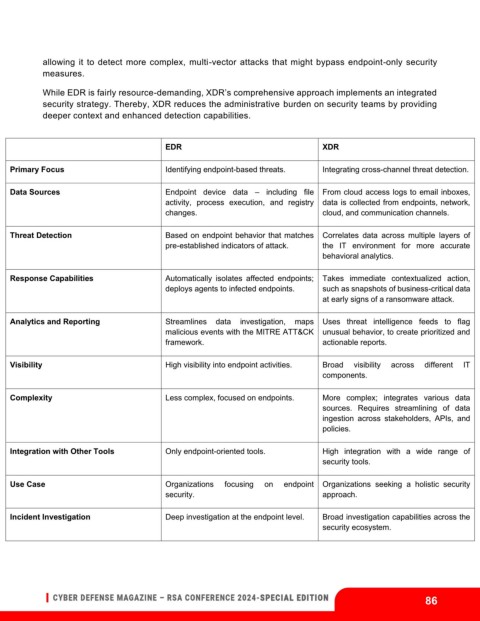
EDR XDR
Primary Focus Identifying endpoint-based threats. Integrating cross-channel threat detection.
Data Sources Endpoint device data – including file From cloud access logs to email inboxes,
activity, process execution, and registry data is collected from endpoints, network,
changes. cloud, and communication channels.
Threat Detection Based on endpoint behavior that matches Correlates data across multiple layers of
pre-established indicators of attack. the IT environment for more accurate
behavioral analytics.
Response Capabilities Automatically isolates affected endpoints; Takes immediate contextualized action,
deploys agents to infected endpoints. such as snapshots of business-critical data
at early signs of a ransomware attack.
Analytics and Reporting Streamlines data investigation, maps Uses threat intelligence feeds to flag
malicious events with the MITRE ATT&CK unusual behavior, to create prioritized and
framework. actionable reports.
Visibility High visibility into endpoint activities. Broad visibility across different IT
components.
Complexity Less complex, focused on endpoints. More complex; integrates various data
sources. Requires streamlining of data
ingestion across stakeholders, APIs, and
policies.
Integration with Other Tools Only endpoint-oriented tools. High integration with a wide range of
security tools.
Use Case Organizations focusing on endpoint Organizations seeking a holistic security
security. approach.
Incident Investigation Deep investigation at the endpoint level. Broad investigation capabilities across the
security ecosystem.
86