Page 100 - Cyber Defense eMagazine October 2023
P. 100
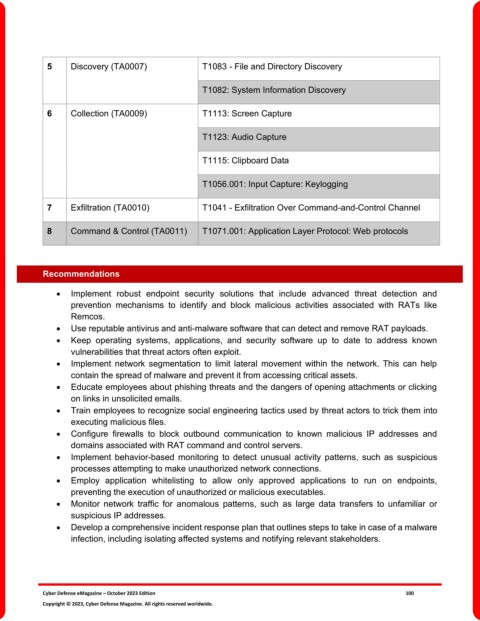
5 Discovery (TA0007) T1083 - File and Directory Discovery
T1082: System Information Discovery
6 Collection (TA0009) T1113: Screen Capture
T1123: Audio Capture
T1115: Clipboard Data
T1056.001: Input Capture: Keylogging
7 Exfiltration (TA0010) T1041 - Exfiltration Over Command-and-Control Channel
8 Command & Control (TA0011) T1071.001: Application Layer Protocol: Web protocols
Recommendations
• Implement robust endpoint security solutions that include advanced threat detection and
prevention mechanisms to identify and block malicious activities associated with RATs like
Remcos.
• Use reputable antivirus and anti-malware software that can detect and remove RAT payloads.
• Keep operating systems, applications, and security software up to date to address known
vulnerabilities that threat actors often exploit.
• Implement network segmentation to limit lateral movement within the network. This can help
contain the spread of malware and prevent it from accessing critical assets.
• Educate employees about phishing threats and the dangers of opening attachments or clicking
on links in unsolicited emails.
• Train employees to recognize social engineering tactics used by threat actors to trick them into
executing malicious files.
• Configure firewalls to block outbound communication to known malicious IP addresses and
domains associated with RAT command and control servers.
• Implement behavior-based monitoring to detect unusual activity patterns, such as suspicious
processes attempting to make unauthorized network connections.
• Employ application whitelisting to allow only approved applications to run on endpoints,
preventing the execution of unauthorized or malicious executables.
• Monitor network traffic for anomalous patterns, such as large data transfers to unfamiliar or
suspicious IP addresses.
• Develop a comprehensive incident response plan that outlines steps to take in case of a malware
infection, including isolating affected systems and notifying relevant stakeholders.
Cyber Defense eMagazine – October 2023 Edition 100
Copyright © 2023, Cyber Defense Magazine. All rights reserved worldwide.