Page 128 - Cyber Defense eMagazine Annual RSA Edition for 2024
P. 128
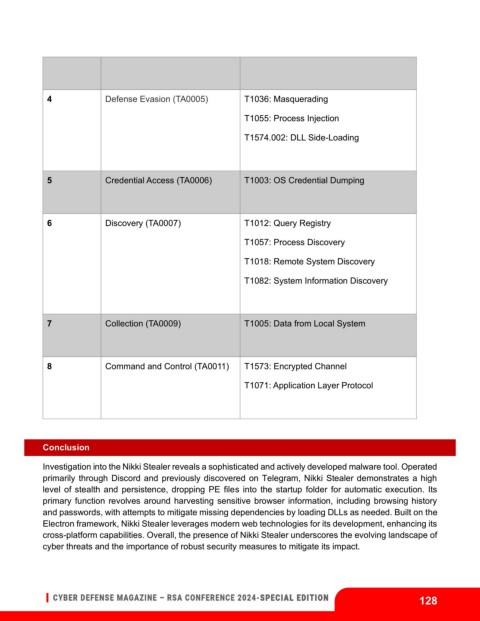
4 Defense Evasion (TA0005) T1036: Masquerading
T1055: Process Injection
T1574.002: DLL Side-Loading
5 Credential Access (TA0006) T1003: OS Credential Dumping
6 Discovery (TA0007) T1012: Query Registry
T1057: Process Discovery
T1018: Remote System Discovery
T1082: System Information Discovery
7 Collection (TA0009) T1005: Data from Local System
8 Command and Control (TA0011) T1573: Encrypted Channel
T1071: Application Layer Protocol
Conclusion
Investigation into the Nikki Stealer reveals a sophisticated and actively developed malware tool. Operated
primarily through Discord and previously discovered on Telegram, Nikki Stealer demonstrates a high
level of stealth and persistence, dropping PE files into the startup folder for automatic execution. Its
primary function revolves around harvesting sensitive browser information, including browsing history
and passwords, with attempts to mitigate missing dependencies by loading DLLs as needed. Built on the
Electron framework, Nikki Stealer leverages modern web technologies for its development, enhancing its
cross-platform capabilities. Overall, the presence of Nikki Stealer underscores the evolving landscape of
cyber threats and the importance of robust security measures to mitigate its impact.
128