Page 93 - Cyber Defense eMagazine June 2024
P. 93
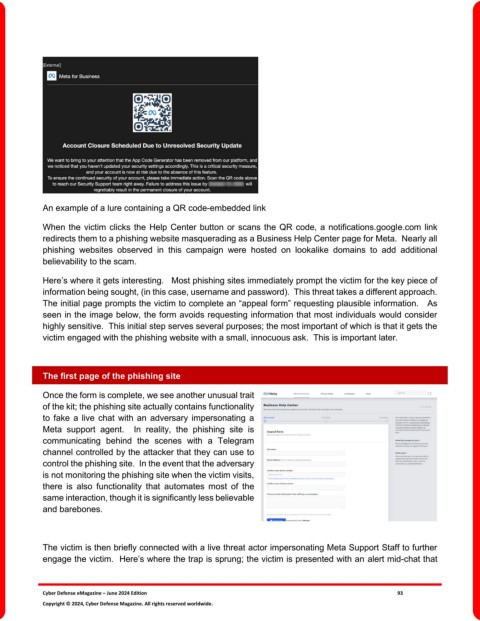
An example of a lure containing a QR code-embedded link
When the victim clicks the Help Center button or scans the QR code, a notifications.google.com link
redirects them to a phishing website masquerading as a Business Help Center page for Meta. Nearly all
phishing websites observed in this campaign were hosted on lookalike domains to add additional
believability to the scam.
Here’s where it gets interesting. Most phishing sites immediately prompt the victim for the key piece of
information being sought, (in this case, username and password). This threat takes a different approach.
The initial page prompts the victim to complete an “appeal form” requesting plausible information. As
seen in the image below, the form avoids requesting information that most individuals would consider
highly sensitive. This initial step serves several purposes; the most important of which is that it gets the
victim engaged with the phishing website with a small, innocuous ask. This is important later.
The first page of the phishing site
Once the form is complete, we see another unusual trait
of the kit; the phishing site actually contains functionality
to fake a live chat with an adversary impersonating a
Meta support agent. In reality, the phishing site is
communicating behind the scenes with a Telegram
channel controlled by the attacker that they can use to
control the phishing site. In the event that the adversary
is not monitoring the phishing site when the victim visits,
there is also functionality that automates most of the
same interaction, though it is significantly less believable
and barebones.
The victim is then briefly connected with a live threat actor impersonating Meta Support Staff to further
engage the victim. Here’s where the trap is sprung; the victim is presented with an alert mid-chat that
Cyber Defense eMagazine – June 2024 Edition 93
Copyright © 2024, Cyber Defense Magazine. All rights reserved worldwide.