Page 27 - CDM-Cyber-Warnings-March-2014
P. 27
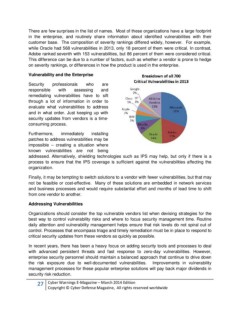
There are few surprises in the list of names. Most of these organizations have a large footprint in the enterprise, and routinely share information about identified vulnerabilities with their customer base. The composition of severity rankings differed widely, however. For example, while Oracle had 568 vulnerabilities in 2013, only 18 percent of them were critical. In contrast, Adobe ranked seventh with 153 vulnerabilities, but 86 percent of them were considered critical. This difference can be due to a number of factors, such as whether a vendor is prone to hedge on severity rankings, or differences in how the product is used in the enterprise. Vulnerability and the Enterprise Security professionals who are responsible with assessing and remediating vulnerabilities have to sift through a lot of information in order to evaluate what vulnerabilities to address and in what order. Just keeping up with security updates from vendors is a time- consuming process. Furthermore, immediately installing patches to address vulnerabilities may be impossible – creating a situation where known vulnerabilities are not being addressed. Alternatively, shielding technologies such as IPS may help, but only if there is a process to ensure that the IPS coverage is sufficient against the vulnerabilities affecting the organization. Finally, it may be tempting to switch solutions to a vendor with fewer vulnerabilities, but that may not be feasible or cost-effective. Many of these solutions are embedded in network services and business processes and would require substantial effort and months of lead time to shift from one vendor to another. Addressing Vulnerabilities Organizations should consider the top vulnerable vendors list when devising strategies for the best way to control vulnerability risks and where to focus security management time. Routine daily attention and vulnerability management helps ensure that risk levels do not spiral out of control. Processes that encompass triage and timely remediation must be in place to respond to critical security updates from these vendors as quickly as possible. In recent years, there has been a heavy focus on adding security tools and processes to deal with advanced persistent threats and fast response to zero-day vulnerabilities. However, enterprise security personnel should maintain a balanced approach that continue to drive down the risk exposure due to well-documented vulnerabilities. Improvements in vulnerability management processes for these popular enterprise solutions will pay back major dividends in security risk reduction. " # % " $ " # ! !