Page 151 - CDM-CYBER-DEFENSE-eMAGAZINE-December-2018
P. 151
31
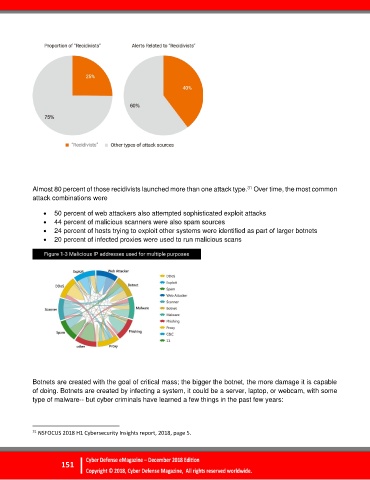
Almost 80 percent of those recidivists launched more than one attack type. Over time, the most common
attack combinations were
50 percent of web attackers also attempted sophisticated exploit attacks
44 percent of malicious scanners were also spam sources
24 percent of hosts trying to exploit other systems were identified as part of larger botnets
20 percent of infected proxies were used to run malicious scans
Botnets are created with the goal of critical mass; the bigger the botnet, the more damage it is capable
of doing. Botnets are created by infecting a system, it could be a server, laptop, or webcam, with some
type of malware-- but cyber criminals have learned a few things in the past few years:
31 NSFOCUS 2018 H1 Cybersecurity Insights report, 2018, page 5.
151