Page 90 - Cyber Defense eMagazine August 2023
P. 90
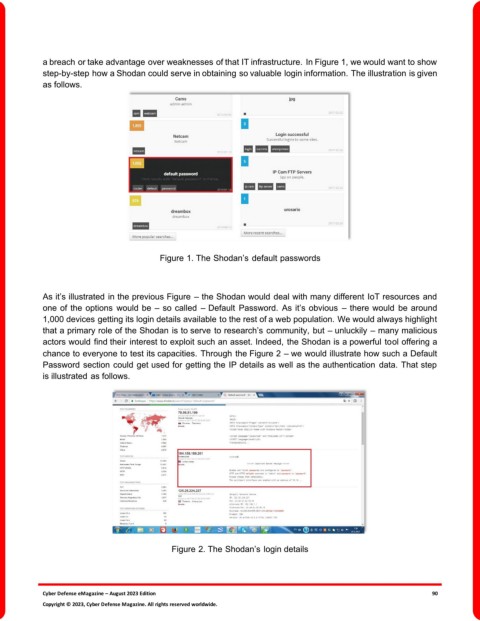
a breach or take advantage over weaknesses of that IT infrastructure. In Figure 1, we would want to show
step-by-step how a Shodan could serve in obtaining so valuable login information. The illustration is given
as follows.
Figure 1. The Shodan’s default passwords
As it’s illustrated in the previous Figure – the Shodan would deal with many different IoT resources and
one of the options would be – so called – Default Password. As it’s obvious – there would be around
1,000 devices getting its login details available to the rest of a web population. We would always highlight
that a primary role of the Shodan is to serve to research’s community, but – unluckily – many malicious
actors would find their interest to exploit such an asset. Indeed, the Shodan is a powerful tool offering a
chance to everyone to test its capacities. Through the Figure 2 – we would illustrate how such a Default
Password section could get used for getting the IP details as well as the authentication data. That step
is illustrated as follows.
Figure 2. The Shodan’s login details
Cyber Defense eMagazine – August 2023 Edition 90
Copyright © 2023, Cyber Defense Magazine. All rights reserved worldwide.