Page 75 - Cyber Defense Magazine for August 2020
P. 75
Under the very best circumstances, it takes days to restore AD in medium to large organizations. All
applications that depend upon AD – most of the enterprise, from file servers to physical security systems
- cannot be returned to availability until it’s restored. And a ransomware attack that has encrypted most
of your network is not the best of circumstances.
The devastating impact
Unlike a natural disaster, every computer system within network reach of a malware attack is at risk
regardless of its location in the world. But for one African server, Maersk’s AD would have been entirely
destroyed by NotPetya. That server just happened to be offline due to power failure. Its hard drives were
hand-flown from Ghana to IT headquarters in England to begin the AD recovery process, which ultimately
took nine days. And most applications couldn’t be restored until AD was restored. NotPetya is
conservatively estimated to have cost the company $300M and its suppliers much more. In total,
NotPetya was estimated to have caused $10 billion damage to organizations worldwide.
A month after they were hit with LockerGoga, 100-year-old Norsk Hydro was still operating most of its
160 manufacturing facilities manually using pre-printed order lists. When all of the computers of Houston
County, Alabama were encrypted, the high school principal said, “People are going to learn what it was
like 50 years ago, 30 years ago.”
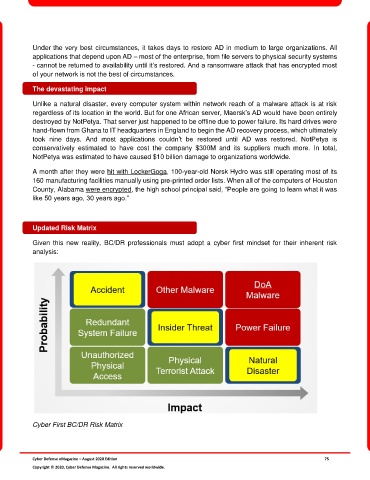
Updated Risk Matrix
Given this new reality, BC/DR professionals must adopt a cyber first mindset for their inherent risk
analysis:
Cyber First BC/DR Risk Matrix
Cyber Defense eMagazine – August 2020 Edition 75
Copyright © 2020, Cyber Defense Magazine. All rights reserved worldwide.