Page 29 - Cyber Defense eMagazine - September 2017
P. 29
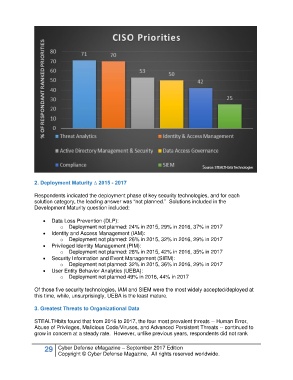
2. Deployment Maturity ∆ 2015 - 2017
Respondents indicated the deployment phase of key security technologies, and for each
solution category, the leading answer was “not planned.” Solutions included in the
Development Maturity question included:
• Data Loss Prevention (DLP):
o Deployment not planned: 24% in 2015, 29% in 2016, 37% in 2017
• Identity and Access Management (IAM):
o Deployment not planned: 26% in 2015, 32% in 2016, 29% in 2017
• Privileged Identity Management (PIM):
o Deployment not planned: 28% in 2015, 42% in 2016, 35% in 2017
• Security Information and Event Management (SIEM):
o Deployment not planned: 32% in 2015, 36% in 2016, 29% in 2017
• User Entity Behavior Analytics (UEBA):
o Deployment not planned 49% in 2016, 44% in 2017
Of those five security technologies, IAM and SIEM were the most widely accepted/deployed at
this time, while, unsurprisingly, UEBA is the least mature.
3. Greatest Threats to Organizational Data
STEALTHbits found that from 2016 to 2017, the four most prevalent threats -- Human Error,
Abuse of Privileges, Malicious Code/Viruses, and Advanced Persistent Threats -- continued to
grow in concern at a steady rate. However, unlike previous years, respondents did not rank
29 Cyber Defense eMagazine – September 2017 Edition
Copyright © Cyber Defense Magazine, All rights reserved worldwide.