Page 12 - index
P. 12
+2 * $$-"..&1" %&*"." &$%(&$%/. //-& 0/&+* ..0".
- " / & # & ($& )& (- & ( #( !! # & $! ' $&' $&%$& ( $#
Recently, the Norse DarkWolf Labs noted that the IP address 218.77.79.43 had jumped into the
top quadrant for malicious activity. Investigation into the activity and the IP itself highlights the
many challenges in accurately attributing such events to known actors, as illustrated in this
article.
The IP - assigned to the CHINANET-HN-HY CHINANET-HN Hengyang node network, Hunan
Telecom on ASN 4134 for China Telecom - had been seen targeting multiple ports and
protocols over several months, and had been increasing activity in the last week of August.
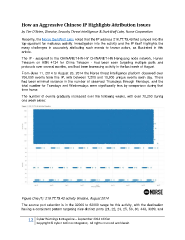
From June 11, 2014 to August 26, 2014 the Norse threat intelligence platform observed over
706,000 events from this IP, with between 7,200 and 10,600 unique events each day. There
had been minimal variance in the number of observed Thursdays through Mondays, and the
total number for Tuesdays and Wednesdays were significantly less by comparison during that
time frame.
The number of events gradually increased over the following weeks, with over 70,200 during
one week alone:
Figure One (1): 218.77.79.43 activity timeline, August 2014
The source port selection is in the 32000 to 62000 range for this activity, with the destination
having a consistent pattern targeting nine distinct ports (21, 22, 23, 25, 53, 80, 443, 3389, and
I25B /1B>9>7C &171J9>5 M +5@D5=25B 49D9?>
?@IB978D K I25B 565>C5 &171J9>5 << B978DC B5C5BF54 G?B<4G945