Page 117 - Cyber Defense eMagazine Annual RSA Edition for 2024
P. 117
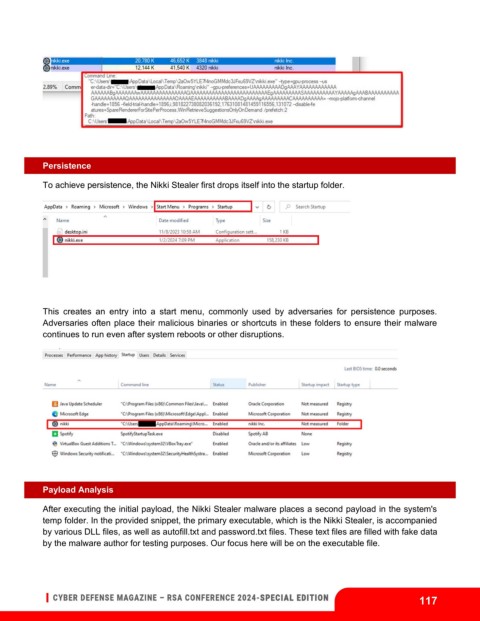
Persistence
To achieve persistence, the Nikki Stealer first drops itself into the startup folder.
This creates an entry into a start menu, commonly used by adversaries for persistence purposes.
Adversaries often place their malicious binaries or shortcuts in these folders to ensure their malware
continues to run even after system reboots or other disruptions.
Payload Analysis
After executing the initial payload, the Nikki Stealer malware places a second payload in the system's
temp folder. In the provided snippet, the primary executable, which is the Nikki Stealer, is accompanied
by various DLL files, as well as autofill.txt and password.txt files. These text files are filled with fake data
by the malware author for testing purposes. Our focus here will be on the executable file.
117