Page 35 - Cyber Defense eMagazine June 2024
P. 35
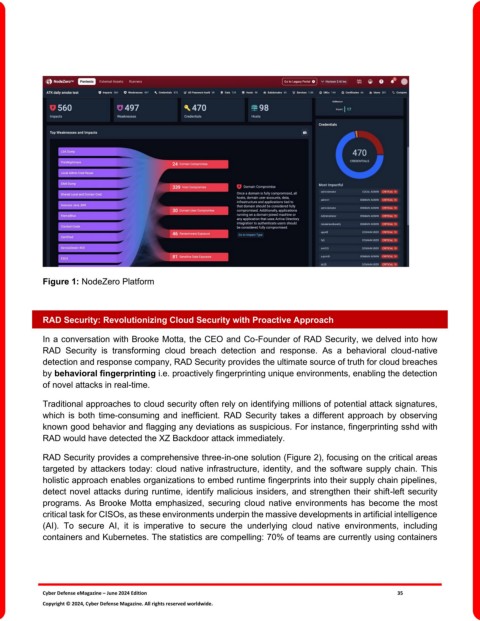
Figure 1: NodeZero Platform
RAD Security: Revolutionizing Cloud Security with Proactive Approach
In a conversation with Brooke Motta, the CEO and Co-Founder of RAD Security, we delved into how
RAD Security is transforming cloud breach detection and response. As a behavioral cloud-native
detection and response company, RAD Security provides the ultimate source of truth for cloud breaches
by behavioral fingerprinting i.e. proactively fingerprinting unique environments, enabling the detection
of novel attacks in real-time.
Traditional approaches to cloud security often rely on identifying millions of potential attack signatures,
which is both time-consuming and inefficient. RAD Security takes a different approach by observing
known good behavior and flagging any deviations as suspicious. For instance, fingerprinting sshd with
RAD would have detected the XZ Backdoor attack immediately.
RAD Security provides a comprehensive three-in-one solution (Figure 2), focusing on the critical areas
targeted by attackers today: cloud native infrastructure, identity, and the software supply chain. This
holistic approach enables organizations to embed runtime fingerprints into their supply chain pipelines,
detect novel attacks during runtime, identify malicious insiders, and strengthen their shift-left security
programs. As Brooke Motta emphasized, securing cloud native environments has become the most
critical task for CISOs, as these environments underpin the massive developments in artificial intelligence
(AI). To secure AI, it is imperative to secure the underlying cloud native environments, including
containers and Kubernetes. The statistics are compelling: 70% of teams are currently using containers
Cyber Defense eMagazine – June 2024 Edition 35
Copyright © 2024, Cyber Defense Magazine. All rights reserved worldwide.