Page 13 - index
P. 13
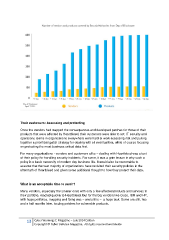
Their customers: Assessing and protecting
Once the vendors had mapped the consequences and developed patches for those of their
products that were affected by Heartbleed, their customers were able to act: IT security and
operations teams in organizations everywhere were hard at work assessing risk and putting
together a prioritized patch strategy for dealing with all eventualities, while of course focusing
on protecting the most business critical data first.
For many organizations - vendors and customers alike – dealing with Heartbleed was a test
of their policy for handling security incidents. For some, it was a grim lesson in why such a
policy is a basic necessity of modern day business life. It would also be reasonable to
assume that the vast majority of organizations have revisited their security policies in the
aftermath of Heartbleed and given some additional thought to how they protect their data.
What is an acceptable time to patch?
Many vendors, especially the smaller ones with only a few affected products and services in
their portfolio, reacted quickly to Heartbleed. But for the big vendors like Cisco, IBM and HP,
with huge portfolios, mapping and fixing was – and still is – a huge task. Some are still, two
and a half months later, issuing patches for vulnerable products.
13 Cyber Warnings E-Magazine – July 2014 Edition
Copyright © Cyber Defense Magazine, All rights reserved worldwide