Page 40 - CDM Cyber Warnings February 2014
P. 40
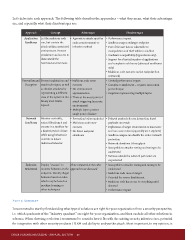
Let�s delve into each approach. The following table describes the approaches – what they mean, what their advantages
are, and especially what their disadvantages are:
Approach Concept Advantages Disadvantages
Application Let the malicious code • Agnostic to attack specifics • Performance impact
Sandboxes run, but contain the such as environment or • Sandbox escapes endanger endpoint
roach Concept Advantages Disadvantages
attack within a restricted infection method • Part of the user data is vulnerable to
environment. Prevent manipulation and theft while in sandbox
persistence and access to • Hardware compatibility (hypervisors only)
data outside the • Support for a limited number of applications
restricted environment. and complex to add more (advanced sandboxes
only)
• Malicious code executes on the endpoint (but
contained)
Prevention and Prevent exploitation and • Malicious code never • Limited performance impact
Deception attack techniques, as well executes • Complex to implement – requires innovation
as deceive attackers by • No environment per technique
representing a different approximation • Requires implementing multiple layers
view of the system at the • There at the exact point of
binary level. Multi- attack triggering (accurate
layered. environment)
• Multiple layers prevent
single point of failure
Network Monitor net traffic, • Prevention before endpoint • Delayed payloads & user interaction based
Sandboxes extract files from it and • Malicious code never payloads can evade
execute in a sandbox for executes • Replication of target environment is inaccurate
a limited period of time • No direct endpoint and can cause misses (especially w.r.t. exploits)
while using behavioral slowdown • Sandbox escapes can disable the entire network
controls to detect protection
malicious behavior. • Network slowdown / throughput
• Susceptible to attacker testing and tuning to be
undetected
• Devices outside the network perimeter are
unprotected
Endpoint Deploy �sensors � to None compared to the other • Susceptible to attacker testing and tuning to be
Behavioral monitor behavior on the approaches we discussed undetected
endpoint. Identify illegal • Malicious code runs on target
behavior based on rules • Potential for sensor disablement
which may be based on • Malicious code has access to everything until
machine learning or detected
other techniques • Performance impact
PART 3: SUMMARY
I recommend to start by first deciding what type of solutions are right for your organization from a security perspective,
i.e. which quadrants of the �industry quadrant � are right for your organization, and then exclude all other solutions in
advance. When choosing a solution I recommend to consider how it fits with the existing security infrastructure, potential
for integration with other security products / SIEM and ability to analyze the attack. Most important, in my opinion, is
CYBER DEFENSE MAGAZINE - ANNUAL EDITION 40