Page 181 - Cyber Defense eMagazine December 2023
P. 181
an asset. For such a purpose, it’s necessary to get the adequate hacker’s tools. We have talked a bit
more about such an operation through the previous chapter. Using that chapter – we have deeply
explained how software such as the Advanced IP Scanner and Radmin could get used in looking for the
vulnerabilities of those IoT solutions. Finally, even that chapter has served to us in a better understanding
of all Shodan’s capacities being used either – for good or bad. Right here, we would illustrate through a
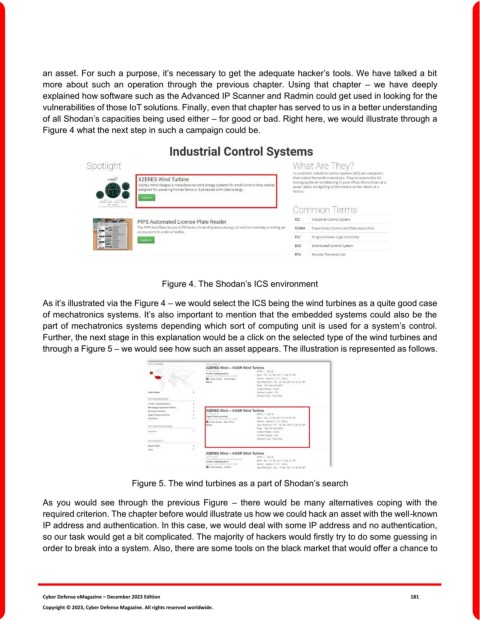
Figure 4 what the next step in such a campaign could be.
Figure 4. The Shodan’s ICS environment
As it’s illustrated via the Figure 4 – we would select the ICS being the wind turbines as a quite good case
of mechatronics systems. It’s also important to mention that the embedded systems could also be the
part of mechatronics systems depending which sort of computing unit is used for a system’s control.
Further, the next stage in this explanation would be a click on the selected type of the wind turbines and
through a Figure 5 – we would see how such an asset appears. The illustration is represented as follows.
Figure 5. The wind turbines as a part of Shodan’s search
As you would see through the previous Figure – there would be many alternatives coping with the
required criterion. The chapter before would illustrate us how we could hack an asset with the well-known
IP address and authentication. In this case, we would deal with some IP address and no authentication,
so our task would get a bit complicated. The majority of hackers would firstly try to do some guessing in
order to break into a system. Also, there are some tools on the black market that would offer a chance to
Cyber Defense eMagazine – December 2023 Edition 181
Copyright © 2023, Cyber Defense Magazine. All rights reserved worldwide.