Page 208 - Cyber Defense eMagazine August 2024
P. 208
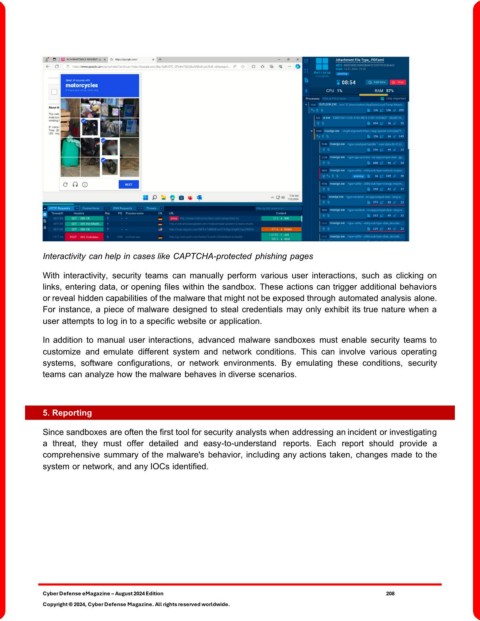
Interactivity can help in cases like CAPTCHA-protected phishing pages
With interactivity, security teams can manually perform various user interactions, such as clicking on
links, entering data, or opening files within the sandbox. These actions can trigger additional behaviors
or reveal hidden capabilities of the malware that might not be exposed through automated analysis alone.
For instance, a piece of malware designed to steal credentials may only exhibit its true nature when a
user attempts to log in to a specific website or application.
In addition to manual user interactions, advanced malware sandboxes must enable security teams to
customize and emulate different system and network conditions. This can involve various operating
systems, software configurations, or network environments. By emulating these conditions, security
teams can analyze how the malware behaves in diverse scenarios.
5. Reporting
Since sandboxes are often the first tool for security analysts when addressing an incident or investigating
a threat, they must offer detailed and easy-to-understand reports. Each report should provide a
comprehensive summary of the malware's behavior, including any actions taken, changes made to the
system or network, and any IOCs identified.
Cyber Defense eMagazine – August 2024 Edition 208
Copyright © 2024, Cyber Defense Magazine. All rights reserved worldwide.