Page 56 - Cyber Defense eMagazine April 2023
P. 56
Weaponizing AI
Previously, the typical level of intelligence that malware had was to watch the system clock and activate
the payload on a certain date and time. Next came detecting if the malware was running in a virtual
sandbox. The AI could detect if specific hardware was available, and the malware would shut down if it
was not. Threat actors have since developed AI modules that evaluate specific environmental conditions
to determine if malware should activate. Environmental factors include the domain the system belongs
to, user accounts on the system, determining if it is being run in a virtual sandbox, what security software
is running, and if it is possible to disable it.
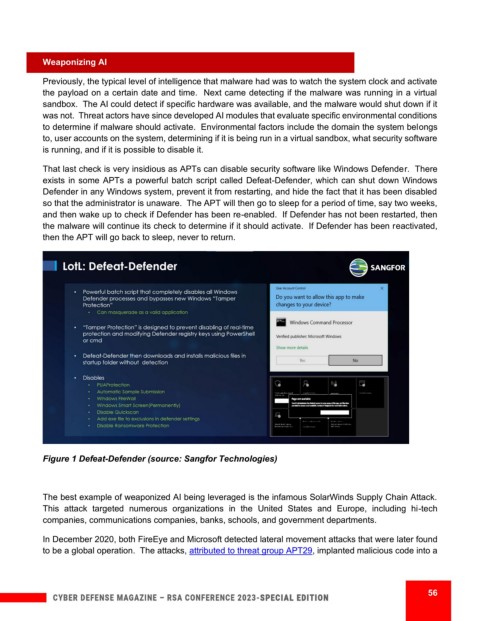
That last check is very insidious as APTs can disable security software like Windows Defender. There
exists in some APTs a powerful batch script called Defeat-Defender, which can shut down Windows
Defender in any Windows system, prevent it from restarting, and hide the fact that it has been disabled
so that the administrator is unaware. The APT will then go to sleep for a period of time, say two weeks,
and then wake up to check if Defender has been re-enabled. If Defender has not been restarted, then
the malware will continue its check to determine if it should activate. If Defender has been reactivated,
then the APT will go back to sleep, never to return.
Figure 1 Defeat-Defender (source: Sangfor Technologies)
The best example of weaponized AI being leveraged is the infamous SolarWinds Supply Chain Attack.
This attack targeted numerous organizations in the United States and Europe, including hi-tech
companies, communications companies, banks, schools, and government departments.
In December 2020, both FireEye and Microsoft detected lateral movement attacks that were later found
to be a global operation. The attacks, attributed to threat group APT29, implanted malicious code into a
56