Page 35 - Cyber Warnings
P. 35
What most organizations don’t realize is that most employees have no malicious intent – they
just aren’t properly trained to handle Spear Phishing, Remote Access Trojans and
Ransomware, among other cyber threats. In addition, highly vulnerable systems as well as
infected (including mobile, through spyware and creepware apps) systems are wide open doors.
Most antivirus software misses at least 50% of the latest malware while firewalls have no
intelligence to block the cleaning company from plugging in a rogue laptop at midnight, for
example.
In addition, the detection of a breach which usually begins BEHIND the firewall is much more
difficult to discover than the traditional breach attempt coming from the outside-in. The main
reason is that most organizations have not deployed agentless, non-inline Network Access
Control (NAC), have not documented their internally exploitable
Vulnerabilities known as Common Vulnerabilities and Exposures (CVEs) as defined by
http://NVD.nist.gov in the National Vulnerability Database, updated very frequently, and have no
way of quarantining, nearly instantly, infected, soon to be infected or rogue network assets,
behind the corporate firewall. Also, the Bring Your Own Device (BYOD) dilemma has left the
corporate ‘backdoor’ wide open to data leakage through mobile devices loaded with creepware,
spyware and very powerful data leakage ports – webcam, Bluetooth, nfc, microphone,
keyboard, wifi, 3g/4g, gps, etc.
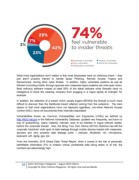
From the Vormetric 2016 Global Data Threat Report, when it comes to the risk of personally
identifiable information (PII) or mission critical confidential data being stolen or at risk, the
numbers are astoundingly high:
35 Cyber Warnings E-Magazine – August 2016 Edition
Copyright © Cyber Defense Magazine, All rights reserved worldwide