Page 39 - CDM Cyber Warnings February 2014
P. 39
2. Exploits – Exploits are normal files (such as documents) or regular network connections that are crafted in a malicious
way in order to trigger a vulnerability in the target program and then run malicious code.
While malicious executables are very popular as a method of
infection, both known exploits and 0-days are a growing
concern with the increasing availability of exploit kits and
public exploits as well as maturation of exploitation
techniques. Every product you consider buying should be able
to properly handle exploits as well as malicious executables.
Unfortunately, most products that claim to handle exploits
and malicious executables are either treating exploits and
malicious executables the same way, or trying to identify
signatures. Taking into account the rates of exploit and
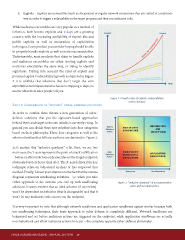
potential exploit (vulnerability) growth as depicted in Figure
2 it is unlikely that solutions that don�t target the core
exploitation techniques stand a chance in stopping 0-days, no
matter what their sales people tell you.
Figure 2: Growth rates of exploits, vulnerabilities
and techniques
PART 2: COMPARISON OF �MODERN� CYBER-DEFENSE SOLUTIONS
In order to combat these threats a new generation of cyber-
defense solutions that put the signature-based approaches
behind them and target unknown attacks is currently rising. In
general you can divide these new solutions into four categories
based on their philosophy. These four categories as well as the
solution families that fall into each one are depicted in Figure 3.
Let�s analyze this �industry quadrant � a bit. First, we see two
main axes: the Y-axis represents the point of attack nullification
– before or after malicious code executes on the target endpoint;
obviously before is better than after. The X-axis defines if the key
technique relies on behavioral analysis or has surpassed that
method. Finally, I direct your attention to the fact that the reverse
diagonal represents sandboxing solutions - i.e. when you take
either approach to the extreme you end up with sandboxing Figure 3: "Industry Quadrant" of next generation
solutions. It seems evident that an ideal solution (if one exists) cyber-defense approaches
won� t be dependent on behavior (that is changeable) and that it
won� t let any malicious code execute on the endpoint.
It is very important to note that although network sandboxes and application sandboxes appear similar because both
use sandboxing techniques, their basic approach to cyber defense is completely different. Network sandboxes are
behavioral and act before malicious actions are triggered on the endpoint, while application sandboxes are actually
non-behavioral and allow malicious actions to occur – the complete opposite cyber-defense philosophy.
CYBER DEFENSE MAGAZINE - ANNUAL EDITION 39