We’ve gone ahead and compiled this article to shed some light on the top ten web application security risks according to OWASP and how you can use this as a guiding light while penetration testing.
By Ankit Pahuja, Marketing Lead & Evangelist at Astra Security

Image Source: Appknox.com
We now live in a world where the internet has altered our daily lives for good. Working and interacting with one another no longer requires the physical presence of both parties within the same room. The number of people on the Internet is rapidly increasing, with around 3 billion individuals now having access. This has led to an exponential growth of web applications in recent years. Web applications, though convenient, also come with vulnerabilities. When it comes to web application security, organisations turn to penetration testing in order to identify potential vulnerabilities and weaknesses in their applications. We’ve gone ahead and compiled this article to shed some light on the top ten web application security risks according to OWASP and how you can use this as a guiding light while penetration testing. Let’s get started.
What is penetration testing?
Penetration testing specifically in the web application domain is the process of testing for vulnerabilities by simulating attacks on it. Penetration testers use a variety of methods to attempt to exploit vulnerabilities in order to gain access to sensitive data or systems. The main goal of penetration testing is to identify and report on any security weaknesses that may exist in an organization’s web applications and have them fixed as soon as possible.
Why do you need to perform penetration tests on web applications?

Image Source: foregenix.com
Web application pen testing is carried out for a number of reasons. The most important include:
- To ensure that online applications are safer and have little to no vulnerabilities
- To prevent unauthorized access
- To comply with external regulations, policies and standards
- To meet internal security requirements
- To verify the effectiveness of security controls
- To resolve issues uncovered during previous online penetration tests
- To remain competitive among other top businesses
What is the OWASP Top Ten?
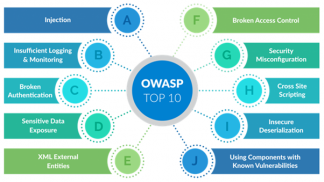
Image Source: cybervaultsec.com
OWASP stands for Open Web Application Security Project. The OWASP Foundation is a global non-profit organization striving to improve the security of web applications and related technology. OWASP publishes an annual list pertaining to the top ten web application vulnerabilities. The list was originally published in 2007 and has been updated since then. It covers all areas from common coding to cyber attacks. Although these are not the only threats out there, they are the most common ones that web developers should address before releasing an app into production for use by customers, clients, and employees.
OWASP Top 10 Web Application Security Risks for 2022
- Broken Access Control – An adversary is able to obtain access to resources or data that they should not have access to when normal security measures, such as permissions and access controls have been poorly implemented.
- Cryptographic Failures – Cryptographic failures are when a web application’s underlying cryptographic algorithms or protocols are compromised and can be exploited.
- Injection and Cross-Site Scripting – Injection occurs when an attacker is able to inject malicious code into input fields on a web page, such as in a search bar or comment box. Cross-Site Scripting is when the attacker inserts malicious code into a web page while or before it is viewed by other users.
- Insecure Design – A web application that is designed in an insecure way leaves room for attackers to exploit. This is often the case since web application developers are not well versed with secure coding practices.
- Security Misconfiguration – Security settings that are incorrectly configured are quite prevalent, making it simple for attackers to capitalize.
- Vulnerable and Outdated Components – When an attacker is able to take benefit of known vulnerabilities in the application or underlying platform, it’s possible that vulnerable and obsolete components will be involved.
- Identification and Authentication Failures – This is when an attacker is able to impersonate another user or gain access to restricted sections of the application without having proper authentication.
- Software and Data Integrity Failures – This happens when an attacker is able to gain access to sensitive information within the application, such as user credentials or credit card numbers.
- Security Logging and Monitoring Failures – Security logging and monitoring failures occur when an attacker is able to disable or circumvent the logging mechanisms in place, making it difficult to track activity within the application.
- Server-Side Request Forgery – This occurs when an attacker is able to inject illegitimate requests from the server-side, such as forgery of login credentials.
These are errors developers often make when creating websites that, if exploited, can lead to serious consequences for your business – including data theft or financial loss!
What is OWASP penetration testing?

Image Source: kirkpatrickprice.com
OWASP penetration testing is pen testing specifically to eradicate the vulnerabilities mentioned in the OWASP top ten list. This is a good starting point but your penetration tests should not be limited to these.
OWASP Penetration Testing Checklist
Keeping in mind the OWASP top ten web app vulnerabilities, we have compiled a checklist to help you with your penetration testing process:
- Review the application’s architecture and design
- Identify and attempt to exploit all input fields, including hidden fields
- Tamper with data entered into the application
- Use a variety of automated tools to find vulnerabilities
- Scan the network for exposed systems and services
- Attack authentication mechanisms – try logging in as different users with known credentials, or using brute force techniques
- Try to gain access to restricted parts of the web application that should otherwise be only reachable by authorized individuals
- Intercept and modify communications between the client-side and the server-side
- Exploit known vulnerabilities in the web application platform or frameworks it is built on
Once you have completed your penetration test, document your findings in a concise report and begin patching your web application immediately.
Conclusion
Penetration testing is a very important step in securing your web application and should not be overlooked. The OWASP Top Ten list is a great starting point, but it should not be the end of your penetration testing journey. In order for penetration tests to be effective, you need an experienced security team who can perform these types of audits and also provide actionable results in a timely manner.
About the Author
 Ankit Pahuja is the Marketing Lead & Evangelist at Astra Security. Ever since his adulthood (literally, he was 20 years old), he began finding vulnerabilities in websites & network infrastructures. Starting his professional career as a software engineer at one of the unicorns enables him in bringing “engineering in marketing” to reality. Working actively in the cybersecurity space for more than 2 years makes him the perfect T-shaped marketing professional. Ankit is an avid speaker in the security space and has delivered various talks in top companies, early-age startups, and online events.
Ankit Pahuja is the Marketing Lead & Evangelist at Astra Security. Ever since his adulthood (literally, he was 20 years old), he began finding vulnerabilities in websites & network infrastructures. Starting his professional career as a software engineer at one of the unicorns enables him in bringing “engineering in marketing” to reality. Working actively in the cybersecurity space for more than 2 years makes him the perfect T-shaped marketing professional. Ankit is an avid speaker in the security space and has delivered various talks in top companies, early-age startups, and online events.
Ankit can be reached online at Email, LinkedIn and at his company website http://www.getastra.com/

