Security vulnerabilities in the vBulletin platform have exposed more than 27 million accounts, many of them belonging to gamers on mail.ru.
The Data breach monitoring service LeakedSource has disclosed 11 new data breaches. Security vulnerabilities in the vBulletin platform have exposed more than 27 million accounts, the majority of which belongs to three games on mail.ru.
At the time of notification, the researchers from LeakedSource had managed to crack 12,463,300 passwords.
Another data breach suffered by expertlaw.com exposed more than 190,000 accounts, meanwhile, a similar incident on gamesforum.com compromised more than 100,000 accounts.
Giving a close look to the compromised mail.ru accounts they belong from CFire, parapa.mail.ru (ParaPa Dance City game), and tanks.mail.ru (Ground War: Tank game).
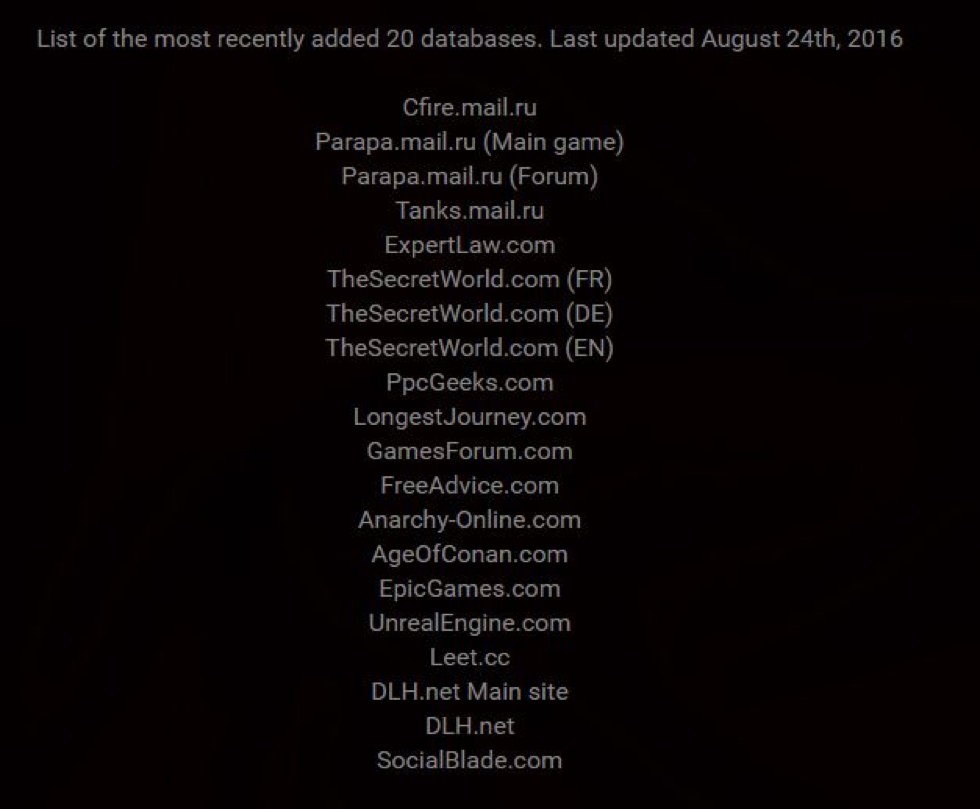
The Subdomains belonging to mail.ru that were hacked in August of 2016 are:
- cfire.mail.ru – 12,881,787 users, 6,226,196 passwords cracked at the time of this post.
- parapa.mail.ru (main game) – 5,029,530 users, 3,329,532 passwords cracked at the time of this post.
- parapa.mail.ru (forums) – 3,986,234 users, 2,907,572 passwords cracked at the time of this post.
- tanks.mail.ru – 3,236,254 users, 0 passwords cracked at the time of this post.

mail.ru records include usernames, email addresses, IP addresses, and phone numbers. The other accounts compromised include usernames, passwords, email addresses, birthdays, and IP address.
“Not a single website used proper password storage, they all used some variation of MD5 with or without unique salts,” LeakedSource said.
What have in common all the compromised websites?
All of the hacked domains were running unpatched versions of the vBulletin CMS. Hackers exploited SQL Injection vulnerabilities in the Forumrunner add-on on vBulletin installations older than 4.2.2 or 4.2.3 to access their database.
Once again the wrong security posture is the root cause of these data breaches, million of users’ records exposed due to security issues fixed by vBulletin months ago.
“A security issue has been reported to us that affects vBulletin 4. We have released security patches for vBulletin 4.2.2 & 4.2.3 to account for this vulnerability. The issue could potentially allow attackers to perform SQL Injection attacks via the included Forumrunner add-on.” states the security advisory issued by vBulletin in June. “It is recommended that all users update as soon as possible. If you’re using a version of vBulletin 4 older than 4.2.2, it is recommended that you upgrade to the latest version as soon as possible. Please note that you need to update regardless of whether you have Forumrunner enabled. You can download the patch for your version here: http://members.vbulletin.com/patches.php“
In August, a new security update was issued to fix multiple vulnerabilities exploited by hackers in the wild.