Identity Detection and Response (IDR) is a new enterprise cybersecurity method that relies on the use of identity-related information to identify that a malicious attack campaign such as ransomware might be on-going on a corporate network.
by Dr. Edward G. Amoroso
Chief Executive Officer, TAG Cyber LLC
Introduction
Cyber defenders categorize security protections as either preventive or reactive. Preventive security, such as strong authentication, focuses on stopping something bad from happening. Reactive security, such as log analysis, deals with bad situations that have already commenced or completed.
The prevention argument is that the cost and effort required to avoid a security problem will always be less than the corresponding cost and effort to respond and recover. The reactive argument is also familiar: Hacking is inevitable, goes the claim, so you’d better be ready to deal with problems as they occur.
Regarding identities, which are central to every modern cybersecurity approach, the preventive aspect is controlled by identity and access management (IAM). Every practitioner will recognize IAM as consisting of the registration, administration, protection, and coordination of identities to support access policies to data and resources.
In contrast, the corresponding reactive component for identities is just emerging. Known as identity detection and response (IDR), the new approach involves using metadata and telemetry from identities to detect, mitigate, and recover from enterprise attacks such as advanced persistent threats (APTs) and ransomware.
Cyber Attack Progression
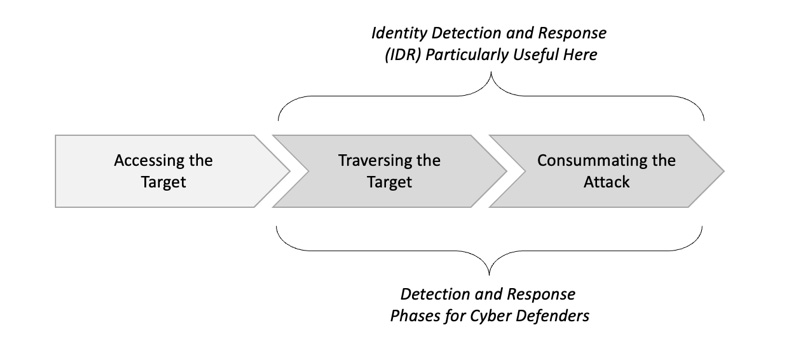
Many attack strategies have been proposed including the MITRE ATT&CK framework1 and the Lockheed Kill Chain2. The three-step process presented below simplifies these more complex models into the three most fundamental phases of every offensive cyber campaign.
Phase 1: Accessing the Target
The initial phase of any cyber breach involves exploiting weaknesses in an attack surface to enter a protected network, domain, system, or other entity. When crossing a perimeter, such access is referred to as a north-south connection, and firewall-based controls are designed to disallow such connection based on policy enforcement. Physical perimeters have recently been replaced with software-defined ones, but the control objective remains.
Phase 2: Traversing the Target
The second phase of a cyber breach involves lateral traversal and privilege escalation, often through theft and misuse of credentials and access to resources such as Microsoft Active Directory (AD). When this occurs slowly, we refer to the process as dwelling, and one of the toughest challenges for defenders involves minimizing attacker dwell time. This report makes the case that IDR offers hope that this challenge might be addressed.
Phase 3: Consummating the Attack
The final phase involves the attacker consummating the attack, either by exiting the targeted domain with stolen data, pushing the button on some integrity or availability attack, or otherwise taking whatever step is required to cause the intended consequence of the attack. Once this has occurred, the best that defenders can do is to respond, and this report also makes the case that IDR assists in this process.
Figure 1. Three-Phase Attack Process Model
What is Identity Detection and Response?
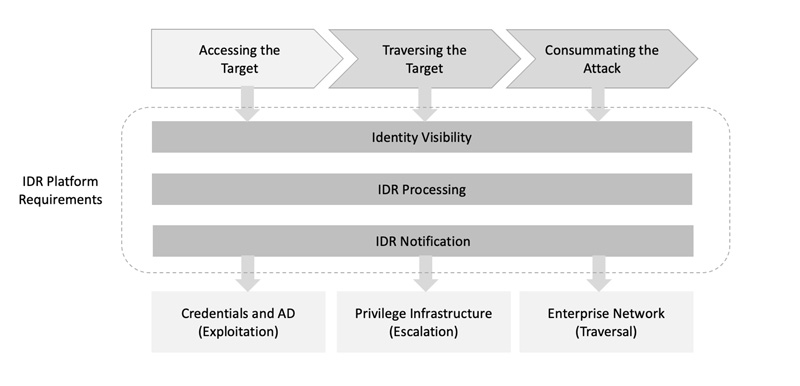
The identity detection and response (IDR) strategy involves focusing on obtaining evidence during the latter two attack phases shown in Figure 1 that an adversary is traversing the targeted entity and preparing to create unwanted consequences. IDR relies on the following strategic protection activities by enterprise defenders:
Establishing Identity Visibility
With the dissolution of the perimeter, identities have become the new basis for access management. As a result, visibility into identity-related attack activity information is now a key source of attack surface risk and an indication that security anomalies might be present. This represents a major shift in how intrusion detection can be accomplished in the enterprise.
One weak or exposed credential can open the door for an attacker. Identity security starts with finding and removing exposed credentials. Policy-based controls can also bind credentials to their credential stores and prevent misuse. Used in conjunction with concealment and deception technology, organizations can also prevent theft and misuse by hiding production credentials and using deception lures and fake artifacts to trick attacker tools and divert the attack to decoys.
For many enterprise teams, their most essential identity resource is Microsoft Active Directory (AD). Through AD, administrators create new users, groups, and domains to set up policy-based enforcement of how PCs, laptops, and other Windows-based services are accessed and managed. Adversaries thus target AD to gain domain control. Given that it is intrinsically insecure, the success rate for exploits it is generally high.
A key activity in the attack strategy for malicious actors involves escalating privileges and entitlements during dwell time and lateral traversal across the targeted enterprise. For this reason, IDR must also focus on this privilege-based aspect of an offensive campaign to detect that an anomaly might be present, and that some security action will be required.
Figure 2. A Platform Model for Identity Detection and Response (IDR)
Commercial implementations of these IDR requirements are beginning to appear – and all seem to tout the benefits of early detection of lateral traversal, directory-based probing, and misuse of privileges. Enterprise security teams now understand that IDR is emerging as a new required area of control for their network.
Action Plan
Security teams should develop a plan to determine how best to leverage IDR solutions to reduce cyber risk. While the context of each enterprise will vary based on its local systems and infrastructure, most teams will benefit by following the steps listed below.
Step 1: Review of Identity-Related Exposures and Data Collection
The enterprise team should begin with an inventory of how identity-related vulnerability and live attack activity information is being handled today to determine exposures, attack status, and posture. In many cases, the answer will be that this is not being done.
Step 2: Vendor Assessment and Review
The enterprise team is next advised to perform a commercial IDR platform review. This usually involves proof-of-concept testing in either a realistic simulated environment or on a live production network.
Step 3: Implementation Planning
Implementation planning involves phased introduction, especially for larger, more complex organizations. The goal, of course, is to deploy IDR quickly to begin detecting identity-based exposures and lateral traversals that might be occurring in the enterprise.
To learn more about IDR and what to pay attention to throughout the IDR selection and implementation process, check out my recent report sponsored by Attivo Networks. This report provides a plan for determining how to use IDR for risk mitigation and highlights the practical use of this technology though the Attivo Networks platform.
About the Author
 Dr. Edward Amoroso, Founder and CEO of TAG Cyber, is an experienced CEO, CSO, CISO, University Professor, Security Consultant, Keynote Speaker, Computer Science Researcher, and Prolific Author (six published books). Dr Amoroso is skilled in Cybersecurity, Network Architecture, Wide Area Network (WAN), Managed Services, and Network Design. He has a PhD in Computer Science from the Stevens Institute of Technology and is a graduate of Columbia Business School. He Directly served four Presidential Administrations in Cybersecurity, and now serves as a Member of the M&T Bank Board of Directors, Senior Advisor for the Applied Physics Lab at Johns Hopkins University, Adjunct CS Professor at the Stevens Institute of Technology, CS Department Instructor at New York University, and Member of the NSA Advisory Board (NSAAB). Dr. Amoroso can be reached at [email protected].
Dr. Edward Amoroso, Founder and CEO of TAG Cyber, is an experienced CEO, CSO, CISO, University Professor, Security Consultant, Keynote Speaker, Computer Science Researcher, and Prolific Author (six published books). Dr Amoroso is skilled in Cybersecurity, Network Architecture, Wide Area Network (WAN), Managed Services, and Network Design. He has a PhD in Computer Science from the Stevens Institute of Technology and is a graduate of Columbia Business School. He Directly served four Presidential Administrations in Cybersecurity, and now serves as a Member of the M&T Bank Board of Directors, Senior Advisor for the Applied Physics Lab at Johns Hopkins University, Adjunct CS Professor at the Stevens Institute of Technology, CS Department Instructor at New York University, and Member of the NSA Advisory Board (NSAAB). Dr. Amoroso can be reached at [email protected].