Turla APT group’s espionage campaigns now employs Adobe Flash Installer and an ingenious social engineering technique, the backdoor is downloaded from what appears to be legitimate Adobe URLs and IP addresses.
Security researchers from ESET who have analyzed recent cyber espionage campaigns conducted by the dreaded Turla APT group reported that hackers leverage on malware downloaded from what appears to be legitimate Adobe URLs and IP addresses.
Turla is the name of a Russian cyber espionage APT group (also known as Waterbug, Venomous Bear and KRYPTON) that has been active since at least 2007 targeting government organizations and private businesses.
The list of victims is long and includes also the Swiss defense firm RUAG, US Department of State, and the US Central Command.
The Turla’s arsenal is composed of sophisticated hacking tools and malware tracked as Turla (Snake and Uroburos rootkit), Epic Turla (Wipbot and Tavdig) and Gloog Turla. In June 2016, researchers from Kaspersky reported that the Turla APT had started using rootkit), Epic Turla (Wipbot and Tavdig) and Gloog Turla.
In the most recent attacks, the group is packaging its macOS backdoor with a real Adobe Flash installer and downloading the malware on victim systems from endpoint systems that use a remote IP belonging to Akamai, the Content Delivery Network that is also used by Adobe for its supply chain. Legitimate Flash installer, in fact, are also distributed through the Akamai network.
“In recent months, we have observed a strange, new behavior, leading to compromise by one of Turla’s backdoors. Not only is it packaged with the real Flash installer, but it also appears to be downloaded from adobe.com.” reads the report published by ESET.
“From the endpoint’s perspective, the remote IP address belongs to Akamai, the official Content Delivery Network (CDN) used by Adobe to distribute their legitimate Flash
installer. “
Researchers noted that Turla installers were exfiltrating information to get.adobe.com URLs since at least July 2016, data were sent back to legitimate URLs at Adobe.com. The download attempts observed by ESET observed were made through HTTP and not via HTTPS, the researchers state with confidence that Adobe was not compromised.
The social engineering technique adopted by Turla group to trick victims into believing they are downloading a legitimate software from Adobe server is very ingenious.
Data collected by the experts revealed that most of the victims belong to the former USSR, targeted entities include embassies and consulates located in East Europe.
At the time of the report is still unclear how the Turla APT group distributed the backdoor through Adobe.com.
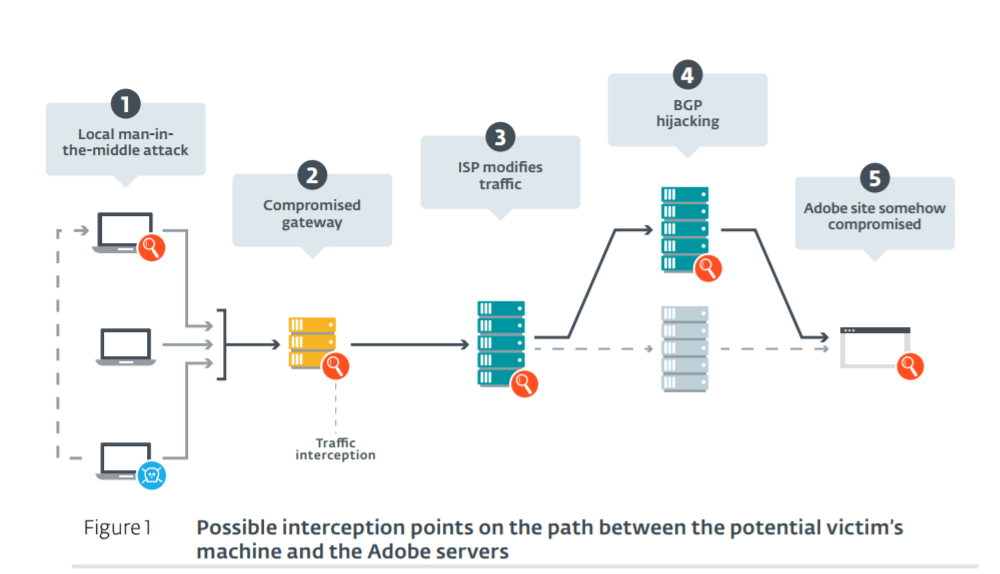
Experts speculate that this is possible by compromising a machine on the victim’s network to perform a local man-in-the-middle attack. In this attack scenario, the threat actors redirect traffic from a target system through the compromised server and modifying it on the fly. Another possibility is to leverage on a compromised local gateway that could allow the attackers to potentially intercept and modify traffic for the whole organization.
Other attacks scenarios see Turla executing a man-in-the-middle attack at the ISP level, or BGP hijacking.
“We quickly discarded the hypothesis of a rogue DNS server, since the IP address corresponds to the servers used by Adobe to distribute Flash.” continues the report. “Thus, these are the hypotheses that remain: ➊ a Man-in-theMiddle
(MitM) attack from an already-compromised machine in the local network, ➋ a compromised gateway or proxy of the organization, ➌ a MitM attack at the Internet Service Provider (ISP) level or ➍ a Border Gateway Protocol (BGP) hijack to redirect the traffic to Turla-controlled servers a MitM attack at the Internet Service Provider (ISP) level or ➍ a Border Gateway Protocol (BGP) hijack to redirect the traffic to Turla-controlled servers.”
Researchers believe the most likely scenario sees attackers controlling the router for the traffic hijacking.
Such kind of attack is any way possible because the files are downloaded via HTTP, for this reason, it is important to avoid installing any update or software that was downloaded through unsecured connections.
Administrators must also check that Flash Player installers downloaded are properly signed with a valid Adobe certificate.
Further information, including the IOCs are included in the report published by ESET.