On January 19th, the United States Department of Justice (DOJ) charged four Chinese nationals—Cheng Qingmin (程庆民), Wu Shurong (吴淑荣), Ding Xiaoyang (丁晓阳), and Zhu Yunmin (朱允敏)—with computer fraud and economic espionage.
According to the DOJ, these men are linked to APT40, a hacking group associated with the Chinese Ministry of State Security. Under a front company, Hainan Xiandun Technology Development Co., APT40 disguised the Chinese government’s role in stealing confidential information from foreign governments and private entities. APT40’s attacks occurred from 2011 through 2018; their attacks include the infamous 2021 Microsoft Exchange Hack, which affected over 30,000 companies and uncovered four zero-day exploits.
Although APT40’s attacks affected entities in the United States, it is unlikely the four men will be extradited and face trial in the United States. Luckily, there are measures companies can take to mitigate the risks and damages caused by APTs, like APT40.
It is unrealistic for many companies, even large technology companies like Microsoft, to prevent and detect all of the techniques used by APTs. In general, APTs are one of the most dangerous cyber-threats because they are well-financed and organized. However, there are ways to mitigate the risks, especially when APTs techniques are publicly analyzed and tracked. According to FireEye, APT40 often used prominent titles (i.e., journalists, military officials, publishers, and NGOs) to target individuals through spear-phishing. APT40 primarily used malicious attachments and google drive links during its spear-phishing attacks. Furthermore, APT40 has used over twenty different open-source malware families to move laterally within networks.
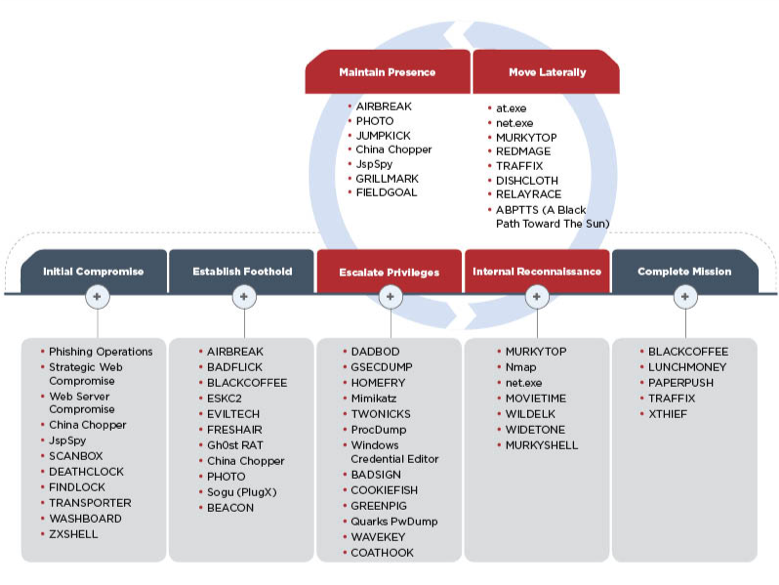
Security is an ongoing battle, which means that learning from past incidents is crucial to protecting information and assets in the future. Furthermore, companies can prevent the initial compromise used by APT40, using advanced network monitoring, security training, and penetration testing. These measures help companies prevent phishing, increase knowledge of custom open-source malware tools, and detect lateral movement within networks (i.e., investigating high traffic rates and unusual activity). These measures often tie to internal governance, so the practices and degree of sophistication may vary depending on company size, risk, and preference.
However, there are other measures companies can take to ensure that their data remains secure after the initial compromise: end-to-end encryption and two-factor authentication (TFA). End-to-end encryption ensures that hackers cannot read the data because they cannot decrypt it. In APT40’s case, APT40 would have access to confidential data, but it would be in an indecipherable state. On the other hand, TFA can help mitigate some login risks by requiring users to verify their identity in multiple ways. Although TFA is not fool-proof, it is significantly more secure than single-factor logins. In other words, TFA would make company networks more secure.
The mitigations above are not an exhaustive list, and there will always be flaws in even the best security systems and practices. However, that does not mean that cybersecurity practices are in vain. Every protective measure prevents attacks exposing sensitive data, protecting employees, assets, and clients
About the Author
 Olivia Gallucci is a Cybersecurity Reporter for Cyber Defense Magazine, on the heels of her winning a Women in Cybersecurity scholarship from CDM.
Olivia Gallucci is a Cybersecurity Reporter for Cyber Defense Magazine, on the heels of her winning a Women in Cybersecurity scholarship from CDM.
She continues her Computing Security and Computer Science student at Rochester Institute of Technology.
She is a Free and Open Source Software advocate and Linux enthusiast. Olivia can be reached online here at CDM and at https://oliviagallucci.com/ and https://www.linkedin.com/in/olivia-gallucci/


