by Gary S. Miliefsky, CISSP, fmDHS
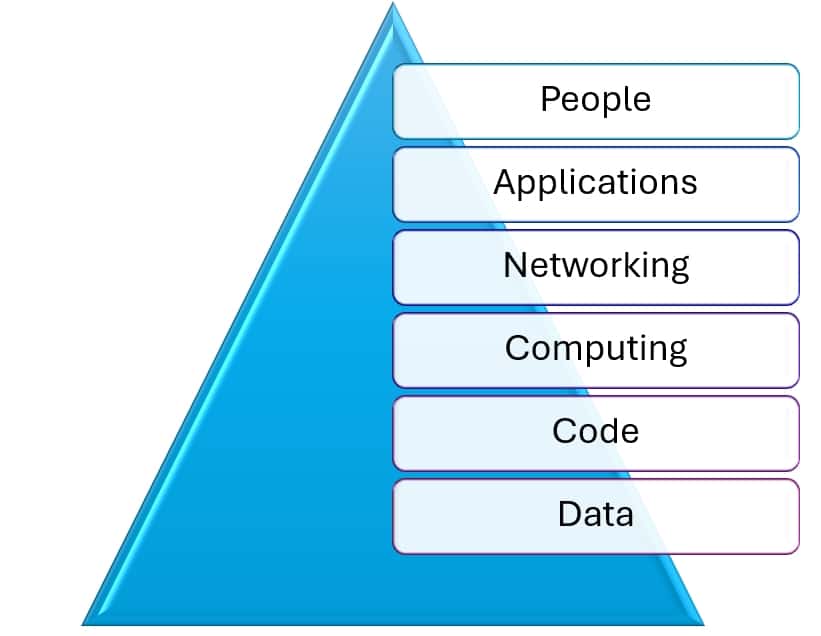
I came up with this model to simplify cybersecurity, resiliency and regulatory compliance for executives who are not cybersecurity experts. The PANCCD™ model (People, Applications, Networking, Computing, Code, and Data) can serve as a structured approach to identifying and managing cybersecurity risks across all essential components of an organization’s digital infrastructure.
| Audience | PANCCD Focus | Key Actions | Goal |
| Employees | Awareness & Essentials | Training on basic practices, simulations, and hands-on experiences | Build foundational knowledge and habits |
| Executives | Strategic Integration | Risk assessment, investment, and delegated ownership for each component | Embed cybersecurity into operations |
| Boards | High-Level Oversight & Metrics | Dashboard reporting, compliance alignment, and key questions to evaluate | Make informed oversight decisions |
By tailoring the PANCCD model to the knowledge and responsibility levels of each group, organizations can ensure that everyone—from beginners to board members—plays an active role in cybersecurity. This approach enhances resilience, strengthens culture, and aligns cybersecurity efforts with the organization’s overall mission.
Here’s how each component contributes to a stronger cybersecurity posture:
- People
- Focus: Security awareness and training for employees, IT staff, and executives.
- Goal: Mitigate human error and insider threats by fostering a security-first culture. This includes regular training on phishing, social engineering, and access controls, as well as ensuring compliance with security policies.
- Applications
- Focus: Securing applications, both internal and customer-facing.
- Goal: Implement secure development practices (like DevSecOps) to identify and address vulnerabilities early in the software lifecycle. This includes regular patching, vulnerability scanning, and security testing to protect against application-layer attacks such as SQL injection, cross-site scripting, and other threats.
- Networking
- Focus: Protecting the flow of data across the organization’s network.
- Goal: Employ network segmentation, firewalls, and intrusion detection/prevention systems to safeguard network access points. Network monitoring tools can detect anomalies, helping to prevent unauthorized access and data breaches.
- Computing
- Focus: Hardening servers, cloud resources, and endpoint devices.
- Goal: Protect all computational resources with strong endpoint protection, secure configurations, and regular system updates. Computing security also includes enforcing device policies for remote work, such as endpoint detection and response (EDR) solutions to protect devices from malware and unauthorized access.
- Code
- Focus: Writing and maintaining secure, resilient code.
- Goal: Adopt secure coding practices, including input validation, error handling, and secure API development. Regular code reviews, static and dynamic analysis, and vulnerability assessments are key to minimizing code-level vulnerabilities.
- Data
- Focus: Ensuring data confidentiality, integrity, and availability.
- Goal: Protect sensitive data with encryption (in transit and at rest), enforce strict access controls, and apply data loss prevention (DLP) solutions. Data security also involves managing data lifecycles, including secure deletion and backups, to reduce risks of unauthorized access and accidental loss.
| Component | Process Decisions | Technology Decisions |
| People | Training programs, incident response roles, role-based access | Security awareness platforms, IAM tools |
| Apps | App vetting, patching schedule, decommissioning | Patch management, AST tools |
| Networking | Network access policies, monitoring, backup, disaster recovery | Firewalls, IPS, network monitoring solutions |
| Computing | Endpoint management, BYOD, NAC, policy, supply chain, incident management | EDR, MDM systems |
| Code | Secure SDLC, code review, change management | SAST/DAST tools, secure version control with CI/CD |
| Data | Data classification, backup and recovery, retention policies | Encryption tools, DLP solutions |
For businesses of any size, the PANCCD model can be effectively applied to guide processes and technology decisions. Larger organizations can scale this framework with more advanced tools and policies, while small and mid-sized businesses can implement simpler, cost-effective versions. Here’s how each PANCCD component can inform processes and technology choices, ensuring security is deeply embedded in operations.
- People: Security Awareness and Role-Based Access
- Process Decisions:
- Training Process: Implement a recurring, organization-wide cybersecurity training program. Ensure it covers essential topics like phishing awareness, secure password practices, and data handling.
- Incident Response Roles: Define clear roles in the incident response process, assigning specific responsibilities to teams or individuals across departments.
- Role-Based Access Control (RBAC): Design an access control process based on roles and responsibilities, limiting data and system access based on the principle of least privilege.
- Technology Decisions:
- Security Awareness Platforms: Choose a scalable platform like KnowBe4 or Proofpoint to automate training and simulate phishing attacks for ongoing awareness.
- Access Management Tools: Use an identity and access management (IAM) system (e.g., Okta, Microsoft Azure AD) to manage and monitor access across the organization securely.
- Apps: Application Security and Lifecycle Management
- Process Decisions:
- Application Vetting Process: Establish an evaluation process for new applications, ensuring that security criteria are met before approval and implementation.
- Patching and Update Process: Create an automated schedule for application updates and patching, minimizing vulnerabilities across the software stack.
- Decommissioning Process: Define procedures for securely removing outdated or unnecessary applications, ensuring sensitive data is erased or transferred safely.
- Technology Decisions:
- Patch Management Tools: For large-scale patching, use systems like ManageEngine or SolarWinds Patch Manager to automate updates and track patch status.
- Application Security Testing (AST): Invest in AST tools like Veracode or Checkmarx to identify vulnerabilities during development and testing stages.
- Networking: Network Security and Segmentation
- Process Decisions:
- Network Access Policies: Set clear policies defining who can access specific parts of the network. Implement network segmentation to isolate sensitive data and systems.
- Continuous Monitoring Process: Establish 24/7 network monitoring to detect anomalies in real-time and trigger alerts for suspicious activity.
- Backup and Disaster Recovery Process: Regularly back up network configurations and document a disaster recovery plan to ensure swift restoration of services.
- Technology Decisions:
- Firewall and Intrusion Prevention Systems (IPS): Deploy enterprise-grade firewalls and IPS systems (e.g., Palo Alto Networks, Cisco ASA) for robust network security.
- Network Monitoring Solutions: Choose scalable network monitoring solutions like SolarWinds or Splunk to detect threats and anomalies across multiple locations and devices.
- Computing: Device Security and Endpoint Management
- Process Decisions:
- Endpoint Management Process: Define a process for onboarding, managing, and securing all company devices, including laptops, mobile devices, and IoT devices.
- Bring Your Own Device (BYOD) Policy: Develop a BYOD and NAC policy that specifies security requirements for personal devices accessing corporate resources.
- Incident Management Process: Create a process for handling incidents involving lost, stolen, or compromised devices, including steps for remote wiping and account lockdown.
- Technology Decisions:
- Endpoint Detection and Response (EDR): For comprehensive endpoint security, implement EDR solutions like CrowdStrike, SentinelOne, or Microsoft Defender for Endpoint.
- Mobile Device Management (MDM): Deploy an MDM system (e.g., Intune, AirWatch) to enforce security policies, track devices, and remotely manage mobile endpoints.
- Code: Secure Development Practices and Continuous Testing
- Process Decisions:
- Secure Development Lifecycle (SDL): Integrate security throughout the software development lifecycle, from design to deployment, using secure coding standards.
- Code Review and Testing Process: Establish code review and automated testing processes to identify and resolve vulnerabilities before deployment.
- Change Management Process: Implement a change management process that tracks code changes, requiring approvals and testing before production updates.
- Technology Decisions:
- Static and Dynamic Application Security Testing (SAST/DAST): Use SAST/DAST tools (e.g., Fortify, Acunetix) to automatically analyze code for vulnerabilities in both pre-production and production environments.
- Version Control and CI/CD Security: Use secure version control platforms (e.g., GitHub, GitLab) integrated with continuous integration/continuous deployment (CI/CD) security tools to automate testing and enforce security policies.
- Data: Data Protection and Compliance
- Process Decisions:
- Data Classification and Access Control: Develop a data classification system that defines access restrictions based on data sensitivity, implementing least-privilege access policies.
- Data Backup and Disaster Recovery Process: Regularly back up data, storing it in secure, encrypted locations, and implement a disaster recovery plan.
- Data Retention and Disposal Policies: Establish clear guidelines on data retention, deletion, and secure disposal to reduce the volume of sensitive data retained unnecessarily.
- Technology Decisions:
- Encryption Tools: Use robust encryption solutions (e.g., BitLocker, AWS KMS) to protect data both in transit and at rest.
- Data Loss Prevention (DLP): Implement DLP solutions (e.g., Symantec DLP, Microsoft 365 DLP) to monitor and control the flow of sensitive information, preventing unauthorized access and leaks.
By following the PANCCD model, businesses can ensure that cybersecurity is at the core of their operational decisions, achieving a balance between protection, efficiency, and scalability. This structured, layered approach supports continuous improvement and adaptation to evolving threats, making it suitable for organizations of any size.
PANCCD™ is a Trademark and Copyright © 2024, Gary S. Miliefsky. All rights reserved worldwide.
About the Author
 Gary Miliefsky is the Publisher of Cyber Defense Magazine and a renowned cybersecurity expert, entrepreneur, and keynote speaker. As the founder and CEO of Cyber Defense Media Group, he has significantly influenced the cybersecurity landscape. With decades of experience, Gary is a founding member of the U.S. Department of Homeland Security, a National Information Security Group member, and an active adviser to government and private sector organizations. His insights have been featured in Forbes, CNBC, and The Wall Street Journal, as well as on CNN, Fox News, ABC, NBC, and international media outlets, making him a trusted authority on advanced cyber threats and innovative defense strategies. Gary’s dedication to cybersecurity extends to educating the public, operating a scholarship program for young women in cybersecurity, and investing in and developing cutting-edge technologies to protect against evolving cyber risks.
Gary Miliefsky is the Publisher of Cyber Defense Magazine and a renowned cybersecurity expert, entrepreneur, and keynote speaker. As the founder and CEO of Cyber Defense Media Group, he has significantly influenced the cybersecurity landscape. With decades of experience, Gary is a founding member of the U.S. Department of Homeland Security, a National Information Security Group member, and an active adviser to government and private sector organizations. His insights have been featured in Forbes, CNBC, and The Wall Street Journal, as well as on CNN, Fox News, ABC, NBC, and international media outlets, making him a trusted authority on advanced cyber threats and innovative defense strategies. Gary’s dedication to cybersecurity extends to educating the public, operating a scholarship program for young women in cybersecurity, and investing in and developing cutting-edge technologies to protect against evolving cyber risks.

