By Sagie Dulce, VP Research, Zero Networks
A Brief History of Identity Management
For as long as there have been identities, there have been solutions trying to manage them so that privileges won’t be accidentally or maliciously leaked.
It started with passwords, or in other words: a secret. Unsurprisingly, these secrets tend to get leaked, shared, abused, stolen or simply turn out to be not so secret to begin with (Password123 and others, you know who you are).
As mainframes gave way to client-server architecture, IT admins stopped managing accounts locally and started using various centralized directory solutions. LDAP technology – mainly Microsoft’s Active Directory – became the dominant technology for managing identities. While Active Directory remains the main technology for managing identities, cloud solutions like Microsoft Azure are increasingly gaining traction, especially in managing identities within a complex landscape. This landscape encompasses everything from user authentication to global resources (beyond the organization’s internal network), application authentication, and even external 3rd party access from vendors.
As the identity landscape continues to evolve and grow more complex, attackers continue to evolve their identity targeting methods. This is not surprising, as once an attacker controls a privileged identity/ies, they have almost unlimited access to an organizations’ resources. Due to the complex nature of managing identities, these are far easier to compromise than, let’s say, developing a zero-day exploit, which have limited shelf-life and reach.
In response, security vendors and directory vendors offer some solutions to help organizations better protect their identities. These include the use of MFA in cloud environments, introduction of PAM security solutions, Identity and Access Management solutions, credential vaults and more.
The Achilles Heel of Identity Management: Complexity
While these solutions do offer some improvements in security, they disregard the reality of identity security in organizations – identity access infrastructure and practices have been evolving for (sometimes) decades, creating an impossible knot to untie. Doing identity access the “right way” is hard, very hard. If you are an IT admin, going “by the book” using Microsoft’s guide for privileged access model, you will need a very professional and dedicated team of experts that can build the entire network and identity plane from scratch, making sure tier0 (the control plane) doesn’t overlap with tier1 (the data plane), which doesn’t overlap with tier2 (users and applications plane):
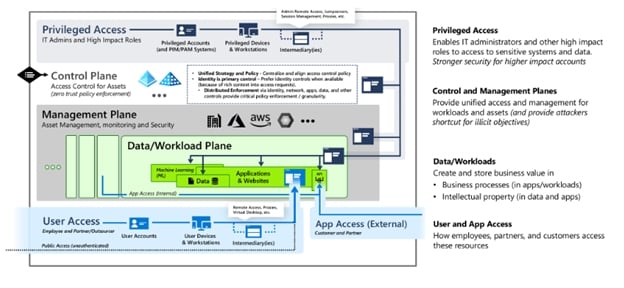
Building such an architecture from the ground up – not to mention in an existing organization – is no small feat. How can you convince the board of a company to invest or even put some of the business continuity at risk, because an app in tier2 has too much access on tier1, and now this needs to be revoked, reprogrammed, retested etc.?
If building it yourself is too hard, you may think existing security solutions can solve this for you, but you would be wrong. Unfortunately, security solutions today mostly focus on two things:
- Visibility: showing customers issues in their directory configuration, and
maybe highlight several paths to solutions.
- Access Management: Protecting privileged identities from leaking by using credential vaults and privileged access gateways.
Even when combined, neither of these approaches solve the problem. Even with enough visibility, the solution can be too complex or painful. And even with enough access management you can’t deploy this solution to the entire organization, only a small subset of identities. The reality is that there are a lot of overlaps between tiers, which leaves a gap that can be exploited.
Segmenting Identities
The task of managing identities can be overwhelming for anyone. Instead of trying to manage access and privileges, we propose a novel approach: identity segmentation. Put simply, it means that identities are first classified into their respective tiers, and then segmented so that they don’t leak to lower-level tiers.
Classification is definitely not trivial. This post by SpecterOps does a great job of showing some methods (using open-source tools) of identifying tier0 accounts and assets. In this phase, we can identify the privileged accounts that are tier0, which assets they log onto (which are also tier0 assets), identify services accounts and their servers as tier1, and the rest of the accounts which are tier2.
Next phase is segmentation, this is the ability to deny logon operations of an account based on a set of rules. Normally, we want to prevent accounts from one tier to perform logons to other tiers as this exposes these accounts to potential leak. These preventions go both ways, as we don’t want a privileged account logging onto a lower privileged asset or a regular user logging onto a higher tiered asset where they could compromise a more privileged account.
We can even segment identities further in the same tier. For example, by limiting service accounts from performing abnormal types of logons, as this may be used for lateral movement in the same tier.
IT admins move between tiers on a regular basis, as this is part of their job. So how do we ensure that such actions are legitimate and not part of a compromise? The answer is to enforce MFA on such privileged accounts. This ensures that these account credentials have not been leaked and misused during an attack.
Summary
Addressing the risks posed by the complex reality of identities is not a trivial task. All the more reason for why it should be done in the simplest and most effective way possible. Identity segmentation, as opposed to identity access management, visibility or privileged access management, is a radically simpler approach that adds resilience across any organization.
About the Author
 Sagie is a defensive security researcher, leading the Zero-Labs team as VP of Research @ Zero Networks.
Sagie is a defensive security researcher, leading the Zero-Labs team as VP of Research @ Zero Networks.
With a bachelor’s in Electrical-Engineer, Sagie started out designing and breaking-up communication schemas in the Intelligence unit of the military. After his service, Sagie went on to perform research on diverse topics, introducing new attacks techniques such as the “man-in-the-cloud” attacks and supply chain compromises against container developers. In recent years, Sagie is focused on research that delivers practical solutions to security teams, mainly in the form of open-source security tools.
Sagie can be reached via email at [email protected] and on Twitter: @SagieDulce


