Security experts at Sucuri have discovered a SQL Injection vulnerability in WP Statistics, one of the most popular WordPress plugins.
Security experts at Sucuri have discovered a SQL Injection vulnerability in WP Statistics, one of the most popular WordPress plugins, that is currently installed on over 300,000 websites. The SQL Injection vulnerability in WP Statistics could be exploited by attackers, with at least a subscriber account, to access the content of the database and potentially take over the vulnerable websites remotely.
The flaw has been discovered in the highly popular WP Statistics plugin, which allows site administrators to get detailed information related to the number of users online on their sites, the number of visits and visitors, and page statistics.
“This vulnerability is caused by the lack of sanitization in user provided data. An attacker with at least a subscriber account could leak sensitive data and under the right circumstances/configurations compromise your WordPress installation.” reads the analysis published by Sucuri.
“If you have a vulnerable version installed and your site allows user registration, you are definitely at risk.”
According to Sucuri, the SQL injection vulnerability in WP Statistics plugin affects multiple functions, including wp_statistics_searchengine_query().
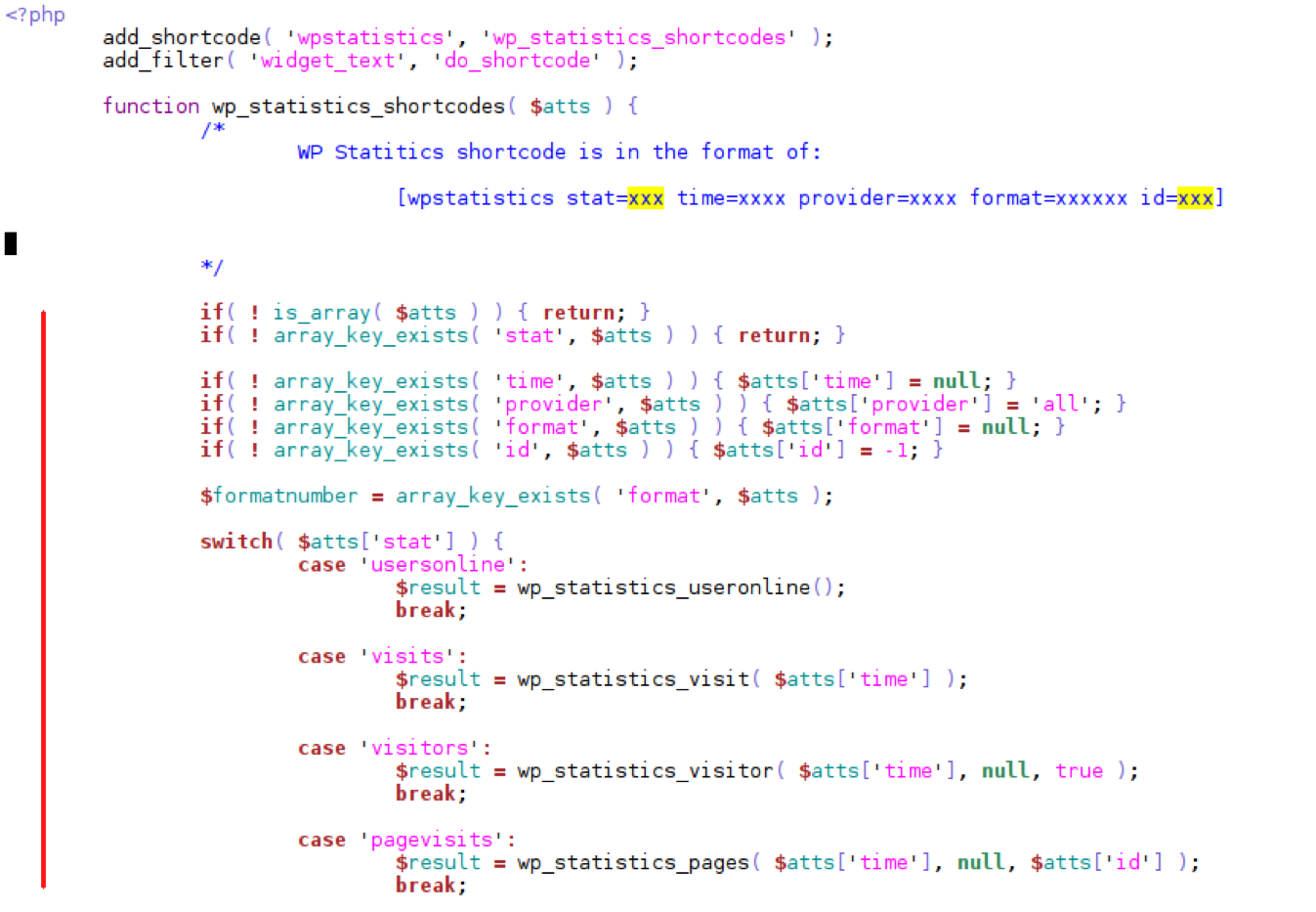
WordPress provides an API that allows developers to create content that users can place directly in their pages by using a simple shortcode:
[shortcode atts_1=”test” atts_2=”test”]
The WP Statistics plugin allows admin users to get detailed information related to the number of visits by just calling the shortcode below:

The function does not check for additional privileges, which allows website subscribers to execute this shortcode and inject malicious code to its attributes.
“Some attributes of the shortcode wpstatistics are being passed as parameters for important functions and this should not be a problem if those parameters were sanitized.” states the analysis.
“One of the vulnerable functions wp_statistics_searchengine_query() in the file ‘includes/functions/functions’ is accessible through WordPress’ AJAX functionality thanks to the core function wp_ajax_parse_media_shortcode().”
The researchers at Sucuri privately reported the vulnerability to the WP Statistics team that promptly fixed it with version 12.0.8.
So, if you have a vulnerable version of the plugin installed and your website, you have to update it to the latest version as soon as possible.
[adrotate group=”7″]