Why You Need to Take A Hard Look At Your Corporate Recovery Plan
By Mickey Bresman, CEO, Semperis
What we as IT and security professionals worry about when planning for disaster recovery has evolved over time.
At first, the major concerns were natural (e.g. hurricanes) or man-made (power failure) physical disasters. After 9/11, we included other physical disasters such as airplanes or explosives to the risk list. Today we have COVID-19, which has emptied not datacenters but offices as entire economies have struggled to suddenly work remotely. Along the way, insider-triggered logical disasters – whether deliberately through an angry employee or an “oops” admin mistake – were also added to the list.
In the last couple of years, however, one cyber threat has eclipsed all the others: denial of availability (DoA) malware, including wiperware and ransomware. If you don’t update your business continuity/disaster recovery (BC/DR) strategy to be “cyber first” to account for this threat, you’re needlessly exposing your organization to potentially catastrophic risk.
Let’s look at how the ransomware threat, enterprise vulnerability to this threat, and the threat’s impact combine to move it to the top of your BC/DR risk matrix. Finally, we’ll recommend action you must take to minimize ransomware’s impact to your organization.
The shape of historic disaster recovery plans
Most historic disaster threats share one characteristic: they can be mitigated with physical or logical distribution or redundancy. East coast data center threatened with a hurricane? Ensure you have a redundant data center in the central US. Worried about power loss? Install a backup UPS for fault tolerance.
Insider logical disasters can be more difficult to recover from than physical disasters, as corruption can spread via the same mechanisms that provide your systems with their fault tolerance. But the history of such incidents has shown that these occurrences are relatively rare, companies have mitigating controls in place, and the incident’s damage is usually limited.
The DoA threat
In contrast, the threat of cyber disaster has come to dominate all other threats due to its frequency and massive impact. Wipers like NotPetya, Shamoon, Destover and ransomware such as Petya, WannaCry, and LockerGoga have crippled organizations large and small around the world, encrypting some or all of their IT infrastructure within minutes or hours of a single computer’s infection and sending them back to manual operations until (or if) they can recover their systems.
Originating as broadly distributed campaigns, ransomware attacks have evolved into highly targeted and extremely damaging network-wide infections[i]. Cybersecurity Ventures predicts that ransomware damages will cost the world $20 billion by 2021[ii]. In addition to large enterprises, state and local governments have also become targets: 53 were reported in 2018, and at least 70 in 2019 including Baltimore and Atlanta[iii].
The enterprise vulnerability
Organizations of all sizes are highly vulnerable to ransomware attacks. Phishing, especially targeted (spear) phishing, remains an extremely effective infection vector because it plays on human nature. Microsoft has stated[iv] that phishing maintains an approximately 15% success rate regardless of education programs – even among its own employees.
There’s also critical vulnerability well understood by IT professionals that have less awareness of the management chain. Microsoft’s Active Directory – the distributed security system that controls user authentication and systems authorization in well over 90% of the world’s medium and large organizations – is devilishly hard to restore. Because of this, only a small percentage of companies have a comprehensive, regularly tested AD recovery plan. (Look your AD admin in the eye and ask.)
Why, after a product lifetime of almost 20 years, do IT departments not have the same level of a recovery plan for AD as they would for a critical file server? Mainly because AD is very robust to both physical domain controller failures and logical failures. But it was designed in the late ’90s when no one could conceive of malware that encrypts every single domain controller within minutes.
Under the very best circumstances, it takes days to restore AD in medium to large organizations. All applications that depend upon AD – most of the enterprise, from file servers to physical security systems – cannot be returned to availability until it’s restored. And a ransomware attack that has encrypted most of your network is not the best of circumstances.
The devastating impact
Unlike a natural disaster, every computer system within the network reach of a malware attack is at risk regardless of its location in the world. But for one African server, Maersk’s AD would have been entirely destroyed by NotPetya. That server just happened to be offline due to power failure. Its hard drives were hand-flown from Ghana to IT headquarters in England to begin the AD recovery process, which ultimately took nine days. And most applications couldn’t be restored until AD was restored. NotPetya is conservatively estimated to have cost the company $300M and its suppliers much more. In total, NotPetya was estimated to have caused $10 billion of damage to organizations worldwide.
A month after they were hit with LockerGoga, 100-year-old Norsk Hydro was still operating most of its 160 manufacturing facilities manually using pre-printed order lists. When all of the computers of Houston County, Alabama were encrypted, the high school principal said, “People are going to learn what it was like 50 years ago, 30 years ago.”
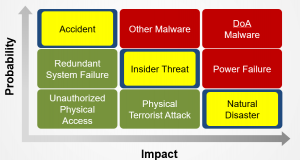
Updated Risk Matrix
Given this new reality, BC/DR professionals must adopt a cyber first mindset for their inherent risk analysis:
Cyber First BC/DR Risk Matrix
This updated matrix considers the threat frequency, enterprise vulnerability, and impact of ransomware and other malware.
Remediating the ransomware risk
How do you lower the risk associated with a ransomware attack? Historically, prevention and detection have been the main defenses against malware, but for ransomware, we’ve already shown these approaches are only moderately effective. Recreating lost data is usually impossible or impractical. Some victims have paid to recover their data, but this is a chancy (and morally ambiguous) approach. Further, data encrypted by worms like NotPetya are unrecoverable.
This leaves recovery as a keystone strategy to minimize the impact of ransomware to your organization. An automated, tested recovery plan for all your critical systems is the best way to minimize the damage inflicted by a ransomware attack. Infrastructure such as Active Directory, DNS, and DHCP must be your top priority because they are foundational to recovering everything else on your network.
Ransomware attacks are the leading cause of organizational IT disruption today. Business continuity and disaster recovery planning need to take this new reality into account and update their risk analysis accordingly. Recovery has traditionally taken a back seat to prevention and detection for malware protection, but today rapid, automated restoration of your systems and data may be the only shield your organization has against corporate Armageddon.
i Multiple sources – Microsoft SIR, Verizon, etc.
iii https://www.recordedfuture.com/state-local-government-ransomware-attacks/
iv “Shut the door to cybercrime…” Ignite 2017, BRK3016, 35:45
About the Author
 Mickey Bresman, CEO, Semperis.Mickey is a co-founder of Semperis and leads the company’s overall strategic vision and implementation. A long-time enterprise software expert, Mickey began his technical career in the Navy computing technical unit over a decade ago. Prior to co-founding Semperis, Mickey was the CTO of a Microsoft gold partner integration company, YouCC Technologies, successfully growing the company’s overall performance year over year. Mickey holds a BA in Technical Management and a Minor in Electronic Engineering.
Mickey Bresman, CEO, Semperis.Mickey is a co-founder of Semperis and leads the company’s overall strategic vision and implementation. A long-time enterprise software expert, Mickey began his technical career in the Navy computing technical unit over a decade ago. Prior to co-founding Semperis, Mickey was the CTO of a Microsoft gold partner integration company, YouCC Technologies, successfully growing the company’s overall performance year over year. Mickey holds a BA in Technical Management and a Minor in Electronic Engineering.
Mickey can be reached on Twitter at @ber_mic and at our company website http://www.semperis.com/
[i]
Multiple sources – Microsoft SIR, Verizon, etc.
https://www.recordedfuture.com/state-local-government-ransomware-attacks/
“Shut the door to cybercrime…” Ignite 2017, BRK3016, 35:45