Researchers have discovered a botnet dubbed PgMiner that targets PostgreSQL databases running on Linux servers to install a cryptocurrency miner.
Security researchers from Palo Alto Networks have discovered a new botnet, tracked as PgMiner, that targets PostgreSQL databases running on Linux servers to install a cryptocurrency miner.
PostgreSQL, also known as Postgres, is one of the most-used open-source relational database management systems (RDBMS) for production environments. It ranks fourth among all database management systems (DBMS) as of November 2020.
The bot performs brute-force attacks against PostgreSQL databases exposed online, it exploits a disputed PostgreSQL remote code execution (RCE) flaw to compromises database servers. It is interesting to note that threat actors have started to weaponize disputed CVEs, not only confirmed ones.
“The feature in PostgreSQL under exploitation is “copy from program,” which was introduced in version 9.3 on Sept. 9, 2013. In 2018, CVE-2019-9193 was linked to this feature, naming it as a “vulnerability.” However, the PostgreSQL community challenged this assignment, and the CVE has been labeled as “disputed.” reads the analysis published by Palo Alto Networks Unit42.
“We believe PGMiner is the first cryptocurrency mining botnet that is delivered via PostgreSQL.”
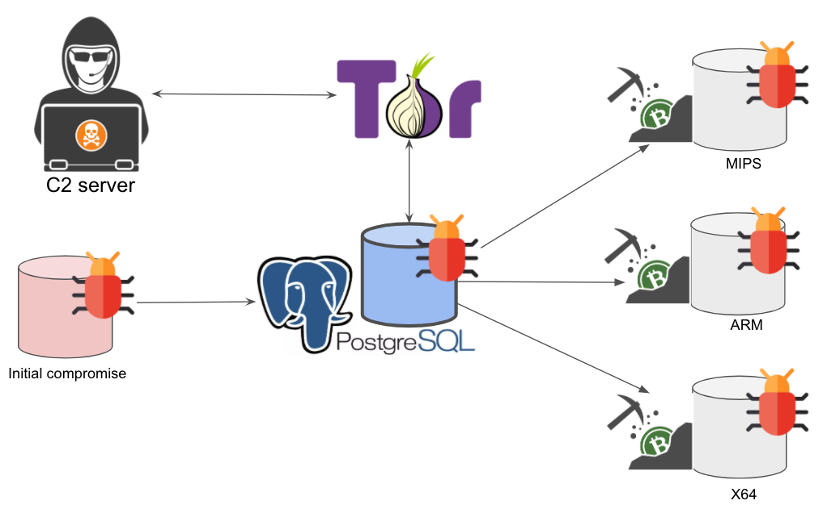
The attack chain starts by randomly picking a public network range (e.g., 190.0.0.0, 66.0.0.0) in an attempt to compromise the PostgreSQL servers having port 5432 exposed online.
The PGminer botnet targets Postgress that have default user “postgres”, and performs a brute-force attack iterating over a built-in list of popular passwords such as “112233“ and “1q2w3e4r“ to bypass authentication.
Once the bot accessed to the database, it uses the PostgreSQL “COPY from PROGRAM” feature to download and launch the coin mining scripts directly from the underlying server.
“The “copy from program” feature has been controversial since its debut in PostgreSQL 9.3. The feature allows the local or remote superuser to run shell script directly on the server, which has raised wide security concerns. In 2019, a CVE-2019-9193 was assigned to this feature, naming it as a “vulnerability.” However, the PostgreSQL community challenged this assignment, and the CVE has been labeled as “disputed.” The main argument against defining the feature as a vulnerability is that the feature itself does not impose a risk as long as the superuser privilege is not granted to remote or untrusted users and the access control and authentication system works well. ” continues the analysis. “On the other side, security researchers worry that this feature indeed makes PostgreSQL a stepping stone for remote exploit and code execution directly on the server’s OS beyond the PostgreSQL software, if the attacker manages to own the superuser privilege by brute-forcing password or SQL injection.”
Then the PgMiner bot deploys a cryptocurrency Monero miner, at the time of the report, the botnet only targets Linux MIPS, ARM, and x64 platforms.
The operators use a command and control (C2) server hosted on the Tor network, experts pointed out that the codebase of this threat borrows code from the SystemdMiner botnet.
Palo Alto Networks Unit42 researchers believe that PGMiner can potentially be disruptive due to the popularity of the PostgreSQL, they warn that with additional effort, the malware could target all major operating systems.
Experts also observed new techniques, such as embedding victim identification in the request, downloading curl binary via multiple approaches, and impersonating a trusted process name.
“PostgreSQL is available for all major platforms, including macOS, Windows and Linux. Theoretically, the malware actors could implement another version of PGMiner by targeting a new platform, such as Windows, and deliver it using PostgreSQL.” concludes the analysis.