By Viktoria Sokurenko, CMO of Ukrainian start-up X-ray
OPSEC (Operational Security) is a term used by US intelligence to describe the analytical process of preventing enemy access to information threatening the secrecy and security of the mission.
The private sector also uses OPSEC as a safeguard against collecting confidential information by competitors and attackers.
In this article, we will talk about the basic measures for personal data protection:
- How to find and delete compromising information about yourself.
- Whether you can remove yourself from the Internet.
- How to prevent credential hack and data theft.
Identification of sensitive data
The first step is to identify sensitive information, precisely how and where it is stored. Put yourself in the place of a competitor or attacker and, using OSINT methods, look for information about yourself or your company.
Types of private personal data:
- full name
- date of birth
- personal and corporate phone numbers
- address
- profiles on social networks
- passwords
Types of private company data:
- intellectual property
- business research
- financial information
- information about employees (family, habits, lifestyle, working environment)
- customer information
- passwords to access resources
- IP, MAC addresses of workstations
Search engines
Start checking for a person or company on the web by using Google, Bing, Yahoo, or DuckDuckGo. Use advanced search operators for advanced keyword search:
inurl:
- username – searches all pages with the username URL.
- [your name] intext: [personal information, such as phone number, ID card, or address] – shows pages that contain personal information about a person.
- site: docs.google.com “companyname” – finds publicly available Google Docs documents that include a company name.
- “companyname.com” – provides resources that link to the company’s page, such as sites with reviews of employers, job search sites, and media portals.
- password filetype: docx site: companyname.com – shows docx files on the company’s website that contain the word “password”. In some cases, such a set of operators will find a file with users’ passwords due to the administrator’s negligence.
Image search
Reverse image search services use a face recognition system and determine which sites have photos of the searcher. Among them are:
Search for email accounts and passwods in leaks databases
In the case of hacking online services, users’ data gets to “leaks databases”. Attackers use databases to understand the logic of password creation and determine if they recur. The goal is to steal identity or gain unauthorized access to computer systems and online services. The following services can be used to verify accounts and passwords in leaks databases:
- Haveibeenpwned
- Google Passwords (check for password leaks stored in your Google Account)
- Spy Cloud
- Ghost Project
- pwndb2am4tzkvold.onion (log in with Tor-browser).
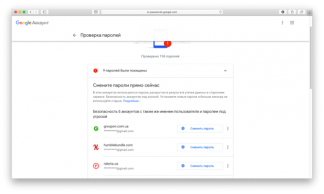
Google Passwords Check checks not only the password for the e-mail account but also the passwords for other services stored in Google
Vulnerability analysis and risk assessment
Make a spreadsheet or chart with known accounts, usernames, and names. Write down telephone numbers and e-mail addresses provided during registration or as contact information.
Identify the vulnerabilities used to gain access to private data and assess the risk level associated with each of them. Factors to evaluate the level of risk include:
- probability of an attack
- degree of damage
- the amount of work and time required for recovery
The more likely and dangerous the attack, the higher the priority of eliminating the vulnerability. The analysis determines which information to keep public and which to hide or delete. Remember that once you enter mail or mobile phone in the contacts section, they are compromised forever.
Application of measures
Depending on the degree of risk, data protection methods include creating strong passwords or passphrases, hiding geolocation, filling the account with false information and fictional stories, or deleting data completely. However, control is an illusion. Everything that got on the Internet stays there forever. Even if you follow the main rule of safety and silence, the result is not guaranteed. The following rules will protect against basic information gathering, but if someone is seriously interested in you, they find everything.
Basic rules of operational security
- Divide accounts. Come up with random e-mail account names for personal use. Create separate accounts for financial transactions, social media registrations, and general purposes.
- Don’t repeat passwords. Use the password manager to generate different passwords for each online service. For additional protection, set up two-factor authentication.
- Delete metadata and hide geolocation. In 2012, programmer and businessman John McAfee was wanted on suspicion of murder. Hiding from Belize police, McAfee ran an escape blog with Vice Magazine, a journalist of Vice Magazine. McAfee’s location in Guatemala revealed a photo in the post as it had been taken on an iPhone and contained EXIF metadata, including geolocation.
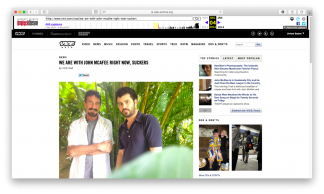
EXIF metadata includes camera model, shooting date and time, and geographic coordinates. Just delete metadata before publishing content to protect your privacy. Better yet, disable geolocation and use VPNs in depersonalized browsers like Tor.
- Hide hints. Do you like to take selfies on Instagram or photo reports about corporate events on Facebook? Social networks have taken care of privacy and automatically removed EXIF before publication. However, there are tips in the photo: silhouettes of buildings, advertising signs, reflections in the mirror, the type of outlet, and documents on the desktop. Such details make it easier to identify a person, find the location of the office or home address, as well as give an idea of the target’s lifestyle.
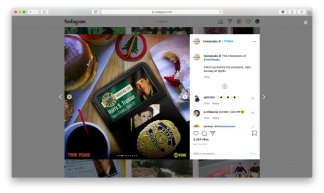
Photos with badges will be useful to attackers during social engineering attacks
- Learn to be silent. Posting content online is a threat to privacy. Social networks feed on emotions, encouraging to share feelings. Before posting comments or photos, think if it gives the attacker information to create a dossier on a person or company. Additionally, teach your loved ones not to post pictures on Facebook, or in the case of Russia, in “Classmates”. In this way, the employer or partner cannot find details of family gatherings, children’s illnesses, and travel.
Russian mothers happily leak photos of their children in “Classmates” after family events.
Filling an account with false info
If you want to protect the information, make sure that the digital trail does not retaliate for clues. Distortion of data will confuse the enemy and will not allow them to make a connection between accounts. In this way, three goals can be achieved simultaneously: you preserve your friendly and credible image, veil your actual goals, and send competitors in the wrong direction.
- Don’t use the actual date of birth, but enter it randomly when registering accounts.
- Don’t enter a full name or use different names for each account.
- Use random profile images for non-public accounts. For example, portraits generated by AI. Make sure photos are unique to each site to prevent finding connections between them by reverse image search.
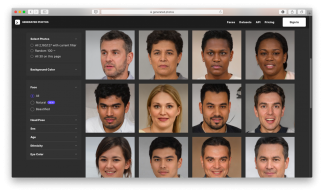
Image caption: Generated Photos uses AI to create portraits of non-existent people
- Create trap files that contain fake credentials or financial statements. Use the Canary Tokens service to receive notifications when opening files and track the IP address of an attacker’s DNS server. IP Logger generates links to place traps or discredited communication channels inside files and tracks the hacker’s IP address and location.
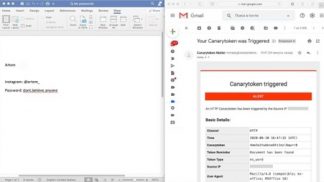
It looks like a regular document (left), but the metadata contains code. The Canary Tokens service sends a message (right) each time you open a Microsoft Word file.
Data deletion
It is impossible to remove yourself from the Internet altogether. Open state registers contain information about vehicles, real estate, and lawsuits, and this data cannot be deleted. Web archives store historical photos of sites. Realistically, you can only delete unused accounts, exclude yourself from brokers’ databases, and send a request to delete publications on social networks and other sites.
- Delete unused accounts. Go to the directory of direct links to delete unused accounts. Remember that it is better to delete an account than to block or deactivate it. When deactivated, the account technically remains online and searchable.
- Exception from brokers’ databases. People search sites or “data brokers” (Pipl, Acxiom, WhitePages) collect and sell personal information from open registries and social networks. To exclude a profile from databases, email owners, or administrators. If there are no contacts on the site, go to the WHOIS catalog and find out the owner’s contacts. In some services, deleting a profile is available through an online form. For a list of links and instructions, see Vice.
- Delete publications in search results, social networks, and other sites. If you do not want personal data to appear in search results, contact the site owner where it is published. Once the information is deleted, Google will not be able to find and add search results. If the site owner refuses to comply with the request, Google will block certain types of personal information. Such requests remain public because if you withdraw a compromising article by contacting Google, the request for removal and the article itself will appear in the Lumen Database.
The same scheme works on social networks: ask a person to delete a post or uncheck a photo. If they refuse, report the violation to the administration and disable the option to tag people on a photo in the settings. There are complaint instructions for:
Analyzing activities from a competitor or attacker’s perspective is the first step in protecting private data. Use OPSEC methods to neutralize intruders’ attempts to steal identity, prevent competitors from gathering information, hide mistakes of your past from a prospective employer, or avoid law enforcement issues. If you do not have time to study OPSEC techniques, contact specialized agencies that perform a full vulnerability test for you.
About the Author
 Viktoria Sokurenko, CMO of Ukrainian start-up X-ray, a platform for finding interconnected information about a person.
Viktoria Sokurenko, CMO of Ukrainian start-up X-ray, a platform for finding interconnected information about a person.
Any human interactions with each other can lead to large-scale search results. Victoria started her career in business communications. She works closely with field intelligence teams specializing in OSINT and HUMINT in various niches in the markets of Europe and US. After 2+ years in marketing and PR of competitive intelligence, she led the marketing and PR department.
Viktoria can be reached online at http://www.linkedin.com/in/viktoria-sokurenko or [email protected] and at company’s website https://x-ray.to/

