Exploring the Future of Cybersecurity at BlackHat 2023
By Kylie M. Amison, Technical Reporter, Cyber Defense Magazine
In our ever-evolving world, where digital threats loom larger and more diverse than ever, I write these trip reports as an opportunity to delve deeper into both the present and future landscape of cybersecurity. Through conversations with C-suite level executives and directors from both emerging startups and established tech giants, we’ll explore the cutting-edge discussions that unfolded at BlackHat 2023. These topics range from the future of AI’s role in fortifying digital defenses to the perplexing realm of quantum cryptography. We’ll examine the rapid proliferation of xIoT devices throughout all industries and the crucial quest in maintaining their security. Keep reading as I explore and discuss the daunting yet thrilling prospects on the cybersecurity horizon.
“Safeguarding Digital Assets in the Quantum Era” with Qrypt, Interview and Discussion featuring CTO and Co-Founder, Denis Mandich
In a digital landscape where the security of our data remains vital, the emergence of quantum computing poses an unprecedented challenge. I had the pleasure of interviewing Denis Mandich, CTO, and co-founder of Qrypt, a cybersecurity company dedicated to fortifying our digital defenses against the looming quantum threat.
Mandich began our conversation by highlighting a fundamental vulnerability in traditional encryption methods – the “harvest now, decrypt later” vulnerability. Qrypt has devised a revolutionary cryptographic solution that eliminates this vulnerability by shunning key transmission altogether. Instead, it safeguards the process using independently generated keys, making it the only cryptographic solution capable of securing data indefinitely. This groundbreaking approach hinges on the generation of one-time pads and symmetric keys at multiple endpoints, boosting data security to an unprecedented level.
Mandich emphasized that the internet, as it stands today, was not constructed with security in mind. This glaring oversight has left us lagging behind in the race to secure our digital assets against quantum threats. He noted that China, for instance, has made significant strides in quantum technology and cybersecurity, underscoring the urgency for the rest of the world to catch up.
Qrypt’s mission, as outlined on their website, is to address this vulnerability by delivering quantum-secure encryption solutions that empower individuals and organizations to protect their data and privacy relentlessly. Both of the founders, Mandich and Kevin Chalker, have curated an exceptional team of experts in engineering, physics, and cryptography to set a new standard in security. They’ve also forged strategic partnerships with quantum hardware companies and research institutions to create the only cryptographic solution capable of securing data indefinitely.
At the heart of Qrypt’s technology lies true quantum randomness, the bedrock of their innovative approach. Combined with advanced techniques and algorithms, the Qrypt SDK enables the development of quantum-secure applications. Qrypt offers several products tailored to meet the evolving security needs of businesses and developers:
- Entropy: Providing businesses with high-rate quantum random numbers through an easy-to-use REST API, ensuring secure encryption.
- Key Generation: Offering a service that generates identical keys at multiple endpoints, protecting against the future quantum threat and avoiding key interception. See Fig. 2 for a closer look at Qrypt’s key generation process.
- Qrypt SDK: Equipping developers with modern tools for easy integration into applications and infrastructure, making them quantum-secure.
In an era where the quantum revolution is underway, Qrypt stands as a catalyst of innovation and security, offering real cutting-edge solutions to protect the Internet and all digital assets as we know it.
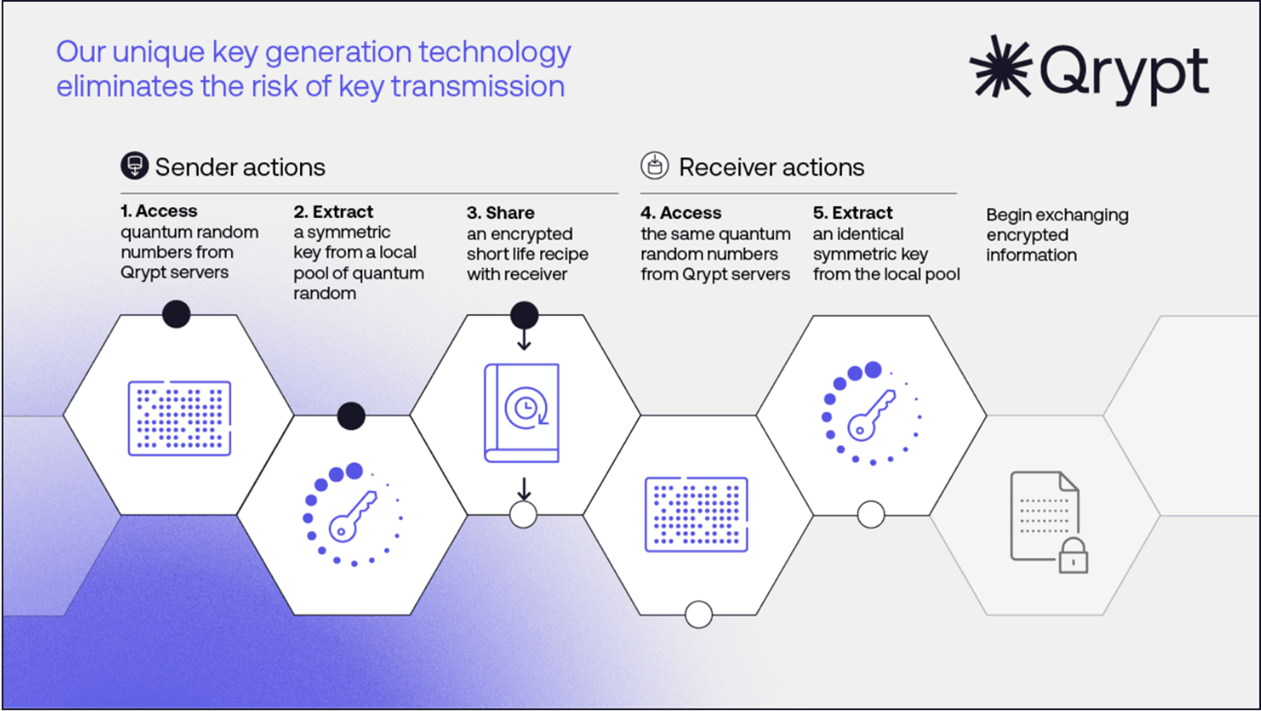
Fig. 2 Screenshot of Qrypt’s Key Generation Process
“Transforming xIoT Cybersecurity” with Phosphorus, Interview and Discussion featuring CMO, John Vecchi
The explosive growth of connected devices, both IoT and xIoT (Extended Internet of Things), across various industries has opened up new realms of possibility while posing substantial security risks. It has created a vast and largely uncharted attack surface that adversaries are actively capitalizing on. In an article by former Phosphorus CSO, Brain Contos, he writes that xIoT devices are an ideal hiding place for sophisticated adversaries, stating that, “these devices are poorly monitored, lack anti-malware and intrusion detection coverage, and are not easy to analyze during incident response.” In my recent conversation with Phosphorus CMO, John Vecchi, we explored their pioneering efforts in reshaping xIoT cybersecurity, with a particular focus on healthcare, where the stakes are undeniably high.
Vecchi emphasized the universal nature of xIoT vulnerabilities, citing a striking statistic: approximately 90% of xIoT devices, regardless of industry, still operate with default credentials. This alarming fact underscores the urgency of addressing vulnerabilities across sectors.
The healthcare industry, in particular, has become a primary target due to the sensitivity of patient data and the life-critical nature of medical devices. Hospitals continually integrate new devices, demanding effective management and security. Vecchi stressed the vital need for visibility to swiftly identify and rectify vulnerabilities within these dynamic environments.
Phosphorus’ Unified xIoT Security Management Platform is a transformative force in this landscape, offering Intelligent Active Discovery for rapid, pinpoint detection of all xIoT devices, be it in healthcare, manufacturing, or beyond. What sets Phosphorus apart is its capacity to provide near real-time risk assessments and automate resolution of critical cyber-physical system vulnerabilities, without necessitating additional hardware or agents.
The impact of Phosphorus’ approach is represented by the following statistics:
- Accurate detection of 90% of xIoT devices.
- Automatic remediation of 80% of xIoT vulnerabilities.
- A cost reduction of over 90% in securing and managing xIoT devices compared to legacy IoT/OT security approaches.
Phosphorus’ methodology, applicable across industries, encompasses:
- Discovery and Identification: Safely and accurately identify IoT, OT, IoMT, and IIoT devices without operational disruptions.
- Risk Assessment: Evaluate the risk profile of xIoT devices, detecting weak credentials, outdated firmware, end-of-life assets, and expired certificates.
- Proactive Hardening: Implement proactive measures to enhance credentials and device security, such as modifying default passwords and managing risky configurations.
- Vulnerability Remediation: Scale up vulnerability resolution efforts while maintaining control, even in sensitive settings.
- Continuous Monitoring: Continuously oversee all xIoT devices, ensuring compliance and adapting to environmental changes and new device additions.
In our world of increasingly connected devices, Phosphorus is at the forefront, driving change that spans industries and safeguards against emerging cyber threats. With their emphasis on precision, speed, and automation, they are poised to fortify xIoT devices in an era where connectivity knows no bounds.
“Pioneering Innovation in Cybersecurity Solutions” with Qwiet AI, Interview and Discussion featuring Director of Product and Tech Marketing, Bruce Snell
As cybersecurity continues its evolution, Qwiet AI is making waves as contemporary protectors dedicated to safeguarding their customers’ digital landscapes. With a unique blend of artificial intelligence, machine learning, and the expertise of top-tier cyber-defenders, Qwiet AI is on a mission to redefine the DevOps and AppSec space with an emphasis on the ability to empower organizations to create code that’s not only secure but also meets their time-to-market demands.
Qwiet AI’s PreZero platform (pictured below in Fig. 1) is at the center of their innovation, as it revolutionizes the way vulnerabilities are identified and mitigated within software code. Traditionally, scrutinizing in-house or third-party libraries required tedious manual inspections, posing the risk of overlooking true vulnerabilities or generating false positives and false negatives. However, the PreZero platform, fueled by Qwiet AI’s cutting-edge engine, introduces an innovative approach. It quickly scans previously unknown libraries and conducts a meticulous comparison against open-source and previously scrutinized counterparts, unveiling new vulnerabilities almost instantaneously. In essence, it transcends the realm of merely detecting zero-day vulnerabilities, extending its capabilities to discover previously undisclosed or unreleased vulnerabilities. Central to PreZero’s capabilities is the revolutionary use of the Code Property Graph (CPG), which deconstructs code into its elemental components, unraveling functional elements and data flow paths into a singular property graph. The ultimate goal of PreZero is to harness a collaboration of known vulnerabilities, heuristic detections, and guided AI, delivering both rapid and pinpoint accuracy. This empowers Qwiet’s customers to address reachable and exploitable vulnerabilities efficiently, eliminating the need for unproductive hunts for false positives or postponed upgrades. Remarkably, by prioritizing these critical vulnerabilities, Qwiet customers achieve an impressive track record, resolving 70% of new vulnerabilities in a mere 14 days or less.
Bruce Snell, Qwiet AI’s Director of Product and Technology Marketing, emphasized the transformative role of AI in the cybersecurity landscape. “At Qwiet AI, we’re looking to change the AppSec space the way EDR changed the anti-virus space,” Snell stated. “In five years, if you’re not using AI to find vulnerabilities in code, you’re going to quickly find yourself out of business. Our ultimate goal is to reduce the noise around software vulnerabilities and help our customers to focus on what’s important: producing secure code.”
Qwiet AI’s innovation has earned them praise from clients across various industries. A testimonial from a security engineer in the retail sector highlights their impact: “As a security engineer working with the Dev teams to implement SDLC and Code security standards and compliance, deploying Qwiet AI for static code testing was a great experience. I enjoyed working with the experts from the Qwiet AI team.”
As digital threats are constantly evolving, Qwiet AI’s commitment to pushing the boundaries of cybersecurity through AI-driven solutions like PreZero Platform ensures that their customers stay ahead in terms of protection and innovation.
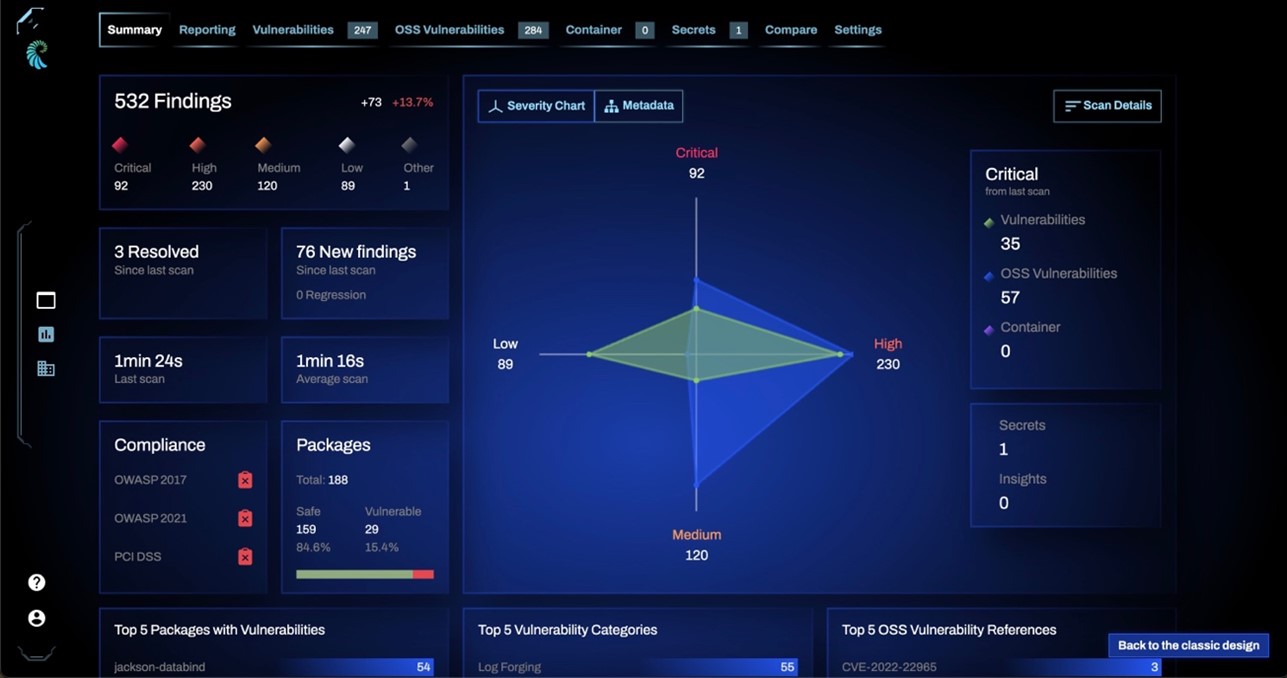
Fig. 1 Screenshot of Qwiet AI’s PreZero Platform
“Elevating Insider Risk Protection” with Code42, Interview and Discussion with SVP of Product Management, Dave Capuano
Code42 stood out to me as they have a unique and fresh perspective on safeguarding valuable company data. I had the privilege of speaking with Dave Capuano, the SVP of Product Management at Code42, where we delved into their innovative approach to Insider Risk protection and their exciting partnership with Tines.
Code42 is no newcomer to the cybersecurity arena, boasting nearly two decades of experience in protecting the intellectual property of the world’s most innovative organizations, including 18 of the globe’s most valuable brands. However, their approach to Insider Risk protection is what truly sets them apart.
The core of Code42’s philosophy is enabling businesses to protect their data without stifling access to it. In a world where collaboration and productivity are paramount, Code42’s SaaS-based Insider Risk Management solutions offers a new approach. By tracking activity across computers, email, and the cloud, their solutions detect and prioritize file exposure and exfiltration events that pose genuine business threats. This means faster detection and response for security practitioners and a collaborative, secure environment for companies.
In my conversation with Capuano, he highlighted the importance of Code42’s mission to evolve with the needs of modern businesses.
One of the most significant recent developments in Code42’s portfolio is their partnership with Tines, a leading provider of security no-code automation. This collaboration enhances security analyst efficiency and productivity in managing Code42’s insider risk data protection platform, Incydr. By harnessing Tines’ powerful automation capabilities, security teams can streamline manual, error-prone, and cross-functional workflows. This automation extends beyond Code42’s Incydr solution, integrating seamlessly with other corporate systems such as IAM, PAM, EDR, HCM, and ITSM.
With Code42 Incydr, customers have achieved remarkable results:
- $5M Worth of Source Code Protected: Incydr detected and prevented the exfiltration of source code by a departing employee, potentially saving the company millions.
- 49,000 Public Links Uncovered: Code42 Incydr unveiled 49,000 public links in Microsoft OneDrive, highlighting the significance of securing shared files.
- 90GB of Sales Data Safeguarded: Incydr prevented 90GB of critical sales data from being moved to an external drive, safeguarding vital business information.
Code42’s innovative approach to Insider Risk protection, coupled with their strategic partnership with Tines, positions them as a formidable force in protecting businesses from the rapidly evolving threat landscape. Although it might sound too good to be true, I witnessed firsthand their commitment to both security practitioners and collaborative workforces by focusing on data protection without impeding productivity. A picture of the Insider Risk Trends dashboard UI can be seen below in Fig. 3.
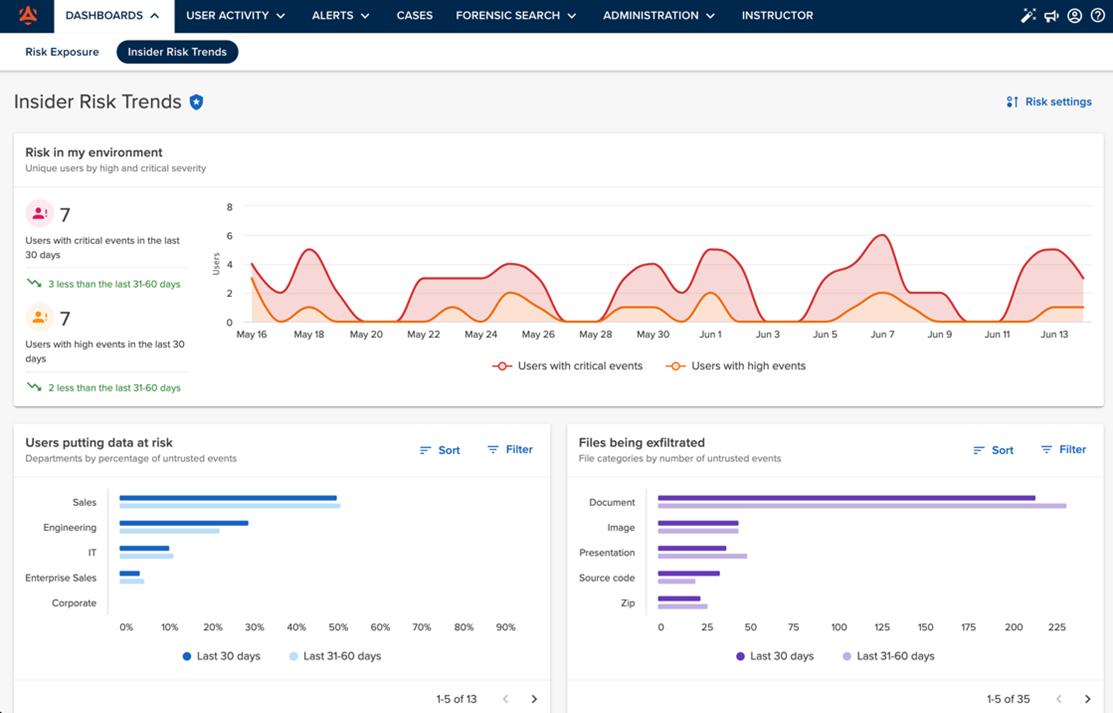
Fig 3. Code42 Insider Risk Trends Dashboard
“Securing Communication in the Hybrid Workplace” with Mimecast, Interview and Discussion featuring Chief Technology & Product Officer, David Raissipour
Mimecast is a beacon of innovation, protecting organizations against a wide array of threats. We recently had the privilege of speaking with David Raissipour, CTPO at Mimecast, where we discussed their forward-thinking approach to cybersecurity, focusing on the crucial importance of email security.
Raissipour emphasized the significance of collaboration tools, such as Microsoft Teams, in the hybrid workplace, where productivity hinges on seamless digital interaction. However, these very tools are often overlooked, under-protected, and prime targets for cybercriminals. To address this vulnerability, Mimecast offers “Protection for Microsoft Teams,” a solution designed to better screen and prevent attacks on these platforms.
We also discussed the importance of training programs as an integral part of a layered cybersecurity approach. While people are often viewed as the weakest link in organizations, they can also be the strongest line of defense when properly educated and enabled. Increasing awareness, improving staff behavior, and leveraging holistic cybersecurity solutions are key to ensuring that collaboration software remains a productivity tool rather than a cyber risk.
One of Mimecast’s standout features is its AI-trained solution, capable of analyzing massive datasets and detecting even minor deviations it hasn’t encountered before. This approach emphasizes the value of data and how more data leads to greater accuracy. Mimecast ensures that its product is approachable and accessible to companies of all sizes, making robust cybersecurity accessible to all.
In an era marked by the pervasive use of digital communication, email has emerged as the central conduit for vital business interactions. It serves as the open door through which critical information flows, making it both a cornerstone of modern commerce and a prime target for cyber adversaries. Mimecast’s email security solutions recognize the paramount importance of safeguarding this digital gateway. Today, email security must defend organizations against a multitude of sophisticated threats, ranging from pervasive phishing attacks and disruptive spam to insidious malware, ransomware, and deceptive brand impersonation. This challenge is further accentuated by the prevalence of large-scale cloud service providers like Microsoft 365 and Google Workspace, which, due to their sheer size and prominence, become prime targets themselves. In this digital landscape, robust email security isn’t merely a choice; it’s an imperative for businesses to thrive securely. Mimecast’s offerings are comprehensive and adaptable, providing best-in-class email security with total deployment flexibility. We discussed two different deployment options tailored to organizational needs.
- Email Security, Cloud Gateway: Ideal for organizations with complex email environments, this solution offers customizable policies and granular controls. It can also be paired with Mimecast’s larger solution suite, including award-winning awareness training and products that proactively safeguard your brand and supply chain.
- Email Security, Cloud Integrated: This solution deploys in minutes and is optimized for organizations seeking to enhance protection for their Microsoft 365 environments. It simplifies email security administration with out-of-the-box settings, an intuitive interface, and one-click threat remediation.
Mimecast’s impact is undeniable, with a track record of delivering results:
- Over 40,000 customers empowered to mitigate risk and manage complexities across evolving threat landscapes.
- 16 Mimecast data centers in 7 countries ensuring data protection and availability.
- 17 million end users protected.
- million queries of email archive searches per week.
- 3 billion emails inspected daily.
- 227 million+ attacks prevented since January 2019.
- 100+ available API capabilities.
Mimecast’s solutions don’t just enhance security; they also have a tangible impact on organizations’ bottom lines. By leveraging Mimecast, businesses can reduce cyber insurance premiums significantly, potentially saving them substantial amounts. Collaboration is key to productivity. Mimecast’s commitment to cybersecurity ensures that organizations can work together safely and effectively, without exposing themselves to undue cyber risks. Mimecast’s focus on protection, training, and innovation makes it a vital partner in today’s digital landscape.
As a recent college graduate who just transitioned into the professional working realm of cybersecurity, my interviews with industry leaders at BlackHat were nothing short of inspiring and exciting. The innovative solutions presented by the mentioned tech companies showcased the remarkable evolution of the field. Yet, in this exciting journey, it becomes obvious that innovation also ushers in unprecedented threats and challenges. It’s a reminder that as cyber professionals, we must remain ever vigilant in our quest to secure the digital frontier. The dynamic interplay of innovation and security serves as a testament to the ongoing adventure that is the cybersecurity landscape—a thrilling journey that beckons us to embrace the future while safeguarding it with relentless dedication.
About the Author
 Born and raised in Hamilton, New Jersey, I am now residing in the DC metropolitan area after recently becoming a George Mason University alum. While at GMU, I obtained my Bachelor of Science degree in Cybersecurity Engineering with a minor in Intelligence Analysis. Along with writing technical pieces for CDM, I am working full time at leading mobile security company, NowSecure, as an Application Security Analyst where I do all types of fun things like exploit vulnerable apps, secure mobile application development, and contribute to exciting projects and important initiatives that are consistently highlighted thought the security industry. In addition, I also work part time with startup company, Auspex Labs, as a Cybersecurity Software Developer, where I am the main developer on DiplomacyTM, a geopolitical threat intelligence engine that combines a broad assortment of metrics and NLP sentiment analysis to calculate nuanced and real-time threat scores per nation state. Working at Auspex has been pivotal in my knowledge in creating secure software and has given me the opportunity to not only develop my first product, but to also start my own startup company, productizing the software and capabilities created in DiplomacyTM. Which brings me to my final endeavor, I am presently co-founder and CTO of Xenophon Analytics, a company that grew from shared interests in international political affairs and my project of building the geopolitical risk engine. When I’m not researching or coding, you can find me watching anime, reading Sci Fi, painting, or playing with my dogs! My ultimate goal in life is to learn every single day, and I’m proud to be doing just that. I love to chat about all thing’s tech and security, so feel free to shoot me a message anytime.
Born and raised in Hamilton, New Jersey, I am now residing in the DC metropolitan area after recently becoming a George Mason University alum. While at GMU, I obtained my Bachelor of Science degree in Cybersecurity Engineering with a minor in Intelligence Analysis. Along with writing technical pieces for CDM, I am working full time at leading mobile security company, NowSecure, as an Application Security Analyst where I do all types of fun things like exploit vulnerable apps, secure mobile application development, and contribute to exciting projects and important initiatives that are consistently highlighted thought the security industry. In addition, I also work part time with startup company, Auspex Labs, as a Cybersecurity Software Developer, where I am the main developer on DiplomacyTM, a geopolitical threat intelligence engine that combines a broad assortment of metrics and NLP sentiment analysis to calculate nuanced and real-time threat scores per nation state. Working at Auspex has been pivotal in my knowledge in creating secure software and has given me the opportunity to not only develop my first product, but to also start my own startup company, productizing the software and capabilities created in DiplomacyTM. Which brings me to my final endeavor, I am presently co-founder and CTO of Xenophon Analytics, a company that grew from shared interests in international political affairs and my project of building the geopolitical risk engine. When I’m not researching or coding, you can find me watching anime, reading Sci Fi, painting, or playing with my dogs! My ultimate goal in life is to learn every single day, and I’m proud to be doing just that. I love to chat about all thing’s tech and security, so feel free to shoot me a message anytime.
Kylie can be reached online at [1] or on LinkedIn https://www.linkedin.com/in/kylie-m-amison-8665a7194/

