Researchers at Amnesty International collected evidence that a Moroccan journalist was targeted with network injection attacks using NSO Group ‘s spyware.
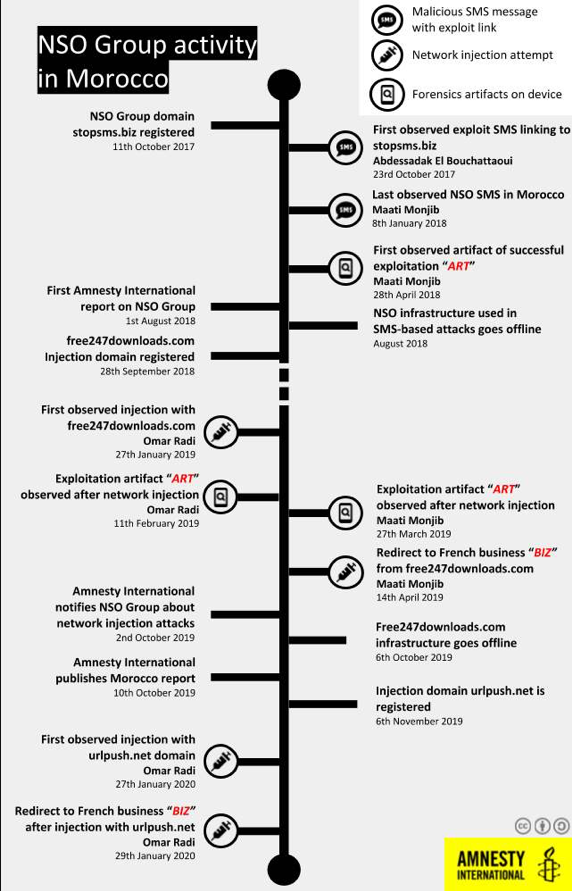
In October 2019, security experts at Amnesty International’s Security Lab have uncovered targeted attacks against Moroccan human rights defenders Maati Monjib and Abdessadak El Bouchattaoui that employed NSO Group surveillance tools.
The researchers are still investigating the attacks and found similar evidence of the attacks on Omar Radi, a prominent activist, and journalist from Morocco.
“After checking his devices for evidence of targeting, Amnesty International was able to confirm that Abdessadak El Bouchattaoui was indeed targeted repeatedly with malicious SMS messages that carried links to websites connected to NSO Group’s Pegasus spyware.” reads the analysis published by Amnesty International in October.
The organization also discovered that the spyware was also used to spy on Maati Monjib, the right group believes the operation is part of state-sponsored repression of human rights defenders.
The victims were targeted with messages related to the Hirak El-Rif movement and the subsequent repression by the Moroccan security forces. The messages included links that once clicked by the victims will start the attack chain that would allow the attacker to remotely control the device.
The links used in these attacks are similar to the ones detected by in June 2018 by Amnesty International in operations against an Amnesty staff member and a Saudi HRD.
On 26 December 2019, Moroccan authorities arrested Radi for a tweet he posted in April, that criticized the judicial system for upholding the verdict against protesters from the 2017 protest movement in Hirak el-Rif.
Omar Radi is a Moroccan award-winning investigative journalist and activist who worked for several national and international media outlets.
“Amnesty International’s Security Lab performed a forensic analysis of Omar Radi’s phone and found traces suggesting he was subjected to the same network injection attacks we first observed against Maati Monjib and described in our earlier report.” reads the report published by Amnesty International. “Through our investigation we were able to confirm that his phone was targeted and put under surveillance during the same period he was prosecuted.”
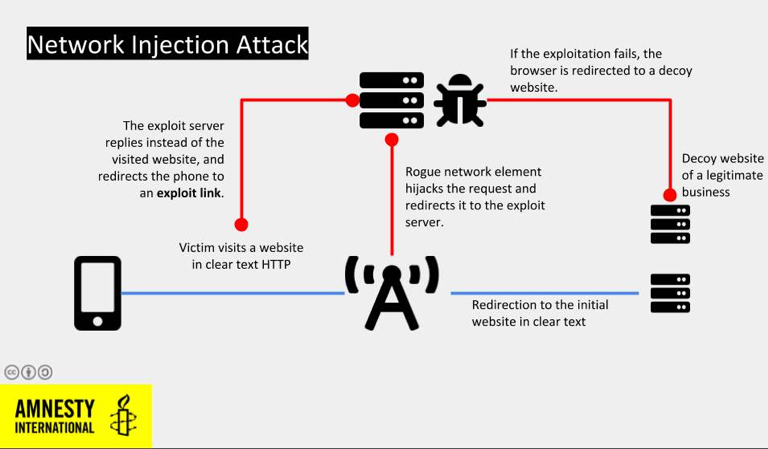
Since October 2019, Amnesty International observed threat actors adopting new stealth techniques to deliver the malware, dubbed “network injections”, that allow them to install the spyware without requiring any target’s interaction.
This attack scenario sees attackers monitoring and manipulating the Internet traffic of the target. In both Omar and Maati’s attacks all injections happened while using their LTE/4G mobile connection.
“This type of attack is possible using two techniques: deploying a device commonly referred to as a “rogue cell tower”, “IMSI Catcher” or “stingray”, or by leveraging access to the mobile operator’s internal infrastructure. It is currently unclear which of these two options have been used against Omar and Maati.” states the report.“However, NSO Group’s network injection capabilities were briefly described in a document named “Pegasus – Product Description” – apparently written by NSO Group – that was found in the 2015 leak of the competing Italian spyware vendor, Hacking Team. Specifically, in January 2020, Business Insider reported about mobile interception technology NSO Group exhibited during Milipol, an event and trade show on homeland security held in Paris in November 2019.”
The analysis of Omar Radi’s iPhone suggests network injection attacks took place on 27th January, 11th February, and 13th of September 2019.
Researchers also discovered that the spyware used to target Radi was also employed in the Maati Monjib’s attack and attack infrastructure overlaps with the one used by the NSO Group’s Pegasus.
The report published by the expert is very important, the researchers pointed out that Omar Radi was targeted just three days after NSO Group released its human rights policy.
This means that the attacks continued after the company became aware of Amnesty International’s first report that provided evidence of the targeted attacks in Morocco. The researchers speculate NSO Group’s continued failure to conduct adequate human rights due diligence and the inefficacy of its own human rights policy.
Technical details about the attacks are included in the report published by Amnesty.