It’s not enough for companies to just discover and monitor sensitive data. They need tools that can proactively fix any security issues to prevent data loss and meet compliance standards. With staff turnover, protecting data becomes even more crucial. Employees can have access to vast amounts of sensitive information like customer details, strategic plans, software designs, contracts, and trade secrets. Keeping this information secure, even as people leave the organization, is vital.
A strong data security posture management (DSPM) system is key for identifying and securing intellectual property (IP) and other sensitive company information that should stay within the business.
Concentric AI helps organizations tackle their data security challenges by locating and safeguarding critical business content. It offers protection for things like intellectual property, financial data, customer details, and more—across both on-premises and cloud systems, as well as messaging platforms. Concentric AI’s Semantic Intelligence™ DSPM solution uses advanced deep learning and its unique Risk Distance™ technology to categorize data, assess risks, and address security issues, all without needing complicated rules or configurations upfront.
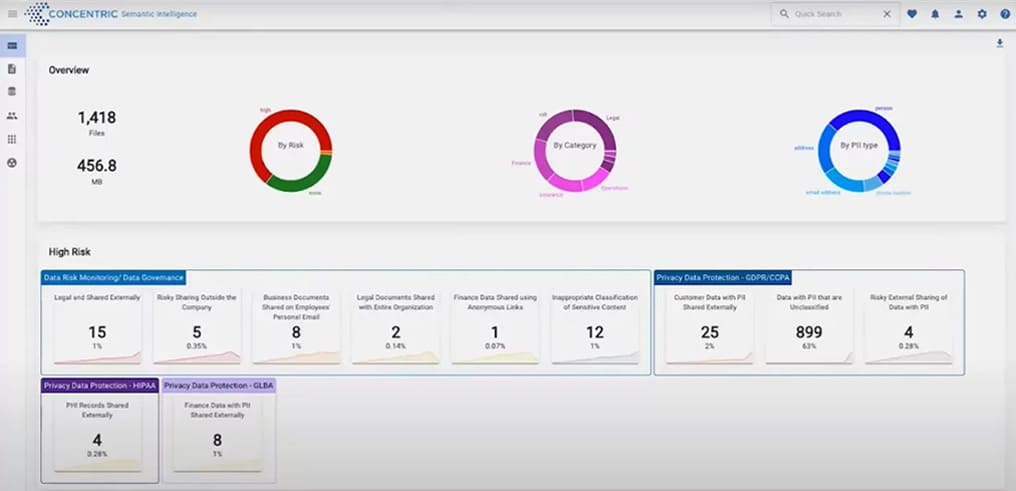
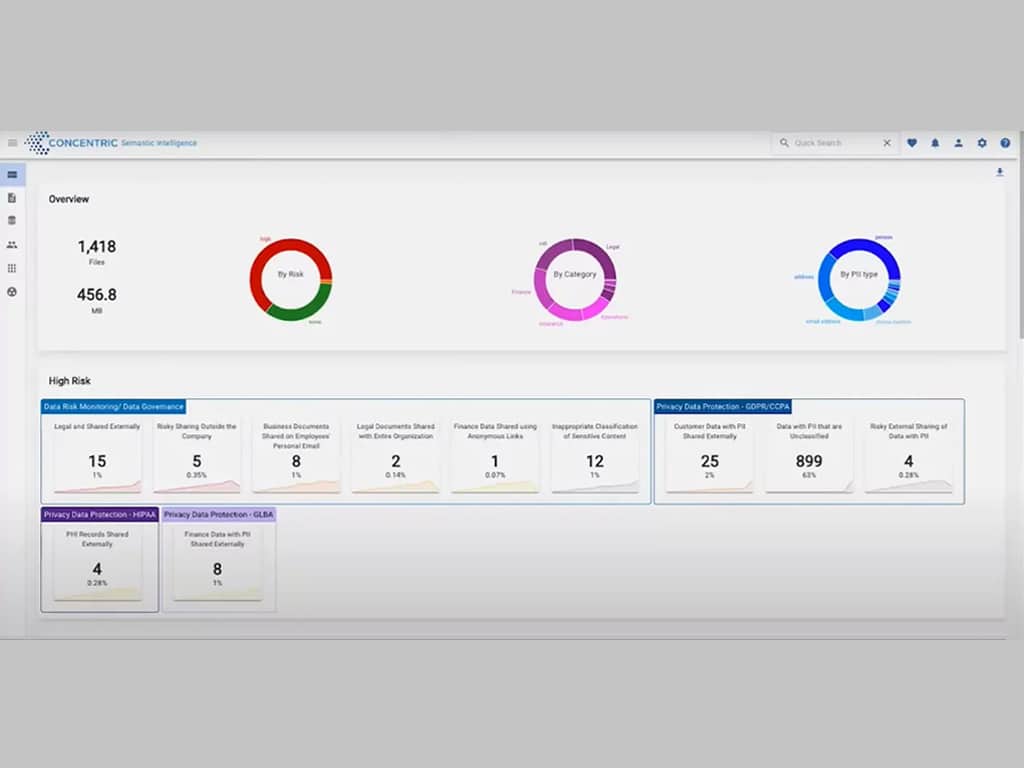
The Concentric AI Semantic Intelligence™ Dashboard
“Enterprises today need their data security posture management solutions to help with their data security and governance requirements,” said Karthik Krishnan, Concentric AI Founder and CEO. “With Concentric AI, they also get proactive discovery, monitoring and remediation capabilities to satisfy their data security and compliance requirements. With our new compliance functionality, organizations gain a detailed understanding of their compliance status and can take proactive measures to address any gaps and satisfy their compliance needs.”
Concentric AI’s Semantic Intelligence DSPM solution is designed to scan an organization’s data, find sensitive or critical business content, and automatically classify and tag it. By using artificial intelligence (AI), Concentric AI improves the accuracy and efficiency of data discovery and classification, so teams don’t have to rely on endless regex rules or inconsistent user labeling.
This SaaS-based platform focuses on data security posture management and access governance. With the help of deep learning, it can automatically identify sensitive data, assess risks, and fix issues.
“Concentric AI has helped us manage our sensitive data across diverse environments. We have now moved on from manual, error-prone processes to a robust, AI-driven data governance system. With Concentric AI, we’ve strengthened our security and have aligned operations with the compliance standards required for our government and aerospace contracts.”
Jason Frame, CIO, Southern Nevada Health District
Concentric AI stands out for its ability to detect data risks within an organization, mapping them to various compliance frameworks. It helps fix these problems and ensures that organizations meet compliance regulations in ways that other products don’t. The new compliance features break down each rule and standard into specific controls, mapping them to the organization’s current data security needs. Concentric AI then keeps track of compliance progress, giving real-time reports and insights, fixing issues, and monitoring the organization’s overall compliance status.
On top of that, Concentric AI can continuously watch for and automatically address risks to financial data and other sensitive information. It can catch inappropriate permissions, risky sharing, unauthorized access, and similar issues. If needed, it can either fix these problems directly or integrate with other security tools to protect exposed data quickly and effectively.
What makes Concentric AI stand out is its context-aware approach to data discovery, classification, and risk monitoring. This means it can understand the sensitivity of data, even when files are stored in unexpected places. Security teams can easily figure out which information is personal data and which is sensitive corporate data, allowing them to make smart decisions about what data should or shouldn’t leave the organization.
Conclusion
With the rapid growth of data, widespread cloud migration, and an ever-increasing variety of complex data types, companies today face significant challenges in data security. Safeguarding intellectual property, financial information, business secrets, and regulated data like PII/PCI/PHI has become increasingly tricky in such complex environments.
Traditional data protection methods, like writing rules to figure out what’s worth protecting, just don’t cut it in today’s cloud-driven world. Plus, in the cloud, it’s easy for employees to create, modify, and share sensitive information with just about anyone.
This puts valuable data at risk of being lost or shared with the wrong people. Relying on employees to manage this isn’t enough.
To keep your sensitive data secure, you need better visibility into who’s accessing it, where it’s going, and how it’s being used. Concentric AI can help by automatically fixing issues and reducing data risks.
Want to see how it works? Take the test: https://concentric.ai/assessment/
About the Author
 Pete Green, vCISO, Cybersecurity Consultant and Reporter for CDM. Pete Green has over 20 years of experience in Information Technology related fields and is an accomplished practitioner of Information Security. He has held a variety of security operations positions including LAN / WLAN Engineer, Threat Analyst / Engineer, Security Project Manager, Security Architect, Cloud Security Architect, Principal Security Consultant, Manager / Director of IT, CTO, CEO, and Virtual CISO. Pete has worked with clients in a wide variety of industries including federal, state and local government, financial services, healthcare, food services, manufacturing, technology, transportation, and hospitality.
Pete Green, vCISO, Cybersecurity Consultant and Reporter for CDM. Pete Green has over 20 years of experience in Information Technology related fields and is an accomplished practitioner of Information Security. He has held a variety of security operations positions including LAN / WLAN Engineer, Threat Analyst / Engineer, Security Project Manager, Security Architect, Cloud Security Architect, Principal Security Consultant, Manager / Director of IT, CTO, CEO, and Virtual CISO. Pete has worked with clients in a wide variety of industries including federal, state and local government, financial services, healthcare, food services, manufacturing, technology, transportation, and hospitality.
Pete holds a Master of Computer Information Systems in Information Security from Boston University, an NSA / DHS National Center of Academic Excellence in Information Assurance / Cyber Defense (CAE IA / CD), and a Master of Business Administration in Informatics.
Pete can be reached online at ([email protected], @petegreen, https://linkedin.com/in/petegreen)