By Milica D. Djekic
The Internet of Things (IoT) represents a collection of devices being capable to talk to each other using the internet as a communication channel. As it’s obvious – the IoT is a cyber as anything else today. That means such a technology could get vulnerable to hacker’s attacks and for such a reason it’s important to apply the good procedures and practices in order to prevent your IoT assets from cyber incidents. Through this chapter – we intend to discuss how hacking of the IoT infrastructure works in practice as well as provide some empirical examples how such a campaign could get conducted in a reality.
How we could obtain login details
Before anyone makes a decision to begin the hacker’s operation, he should try to think which information he got available as well as which tools he has. In many cases, it’s so important to adjust your hacking tool’s needs with the information being necessary for conducting a cyber campaign. The role of this learning material’s chapter is provide a closer look at some of the hacking techniques as well as a usage of cyber technologies in threatening the IoT resources. For the purpose of a good explanation of this strategy – we would use the Shodan tool that got provided some Default Passwords which could assist you in breaking into someone’s system. It’s well known that crawlers like Shodan and Censys could offer an opportunity to get anyone’s IP address and if there is no or poor authentication – anyone could make a breach or take advantage over weaknesses of that IT infrastructure. In Figure 1, we would want to show step-by-step how a Shodan could serve in obtaining so valuable login information. The illustration is given as follows.
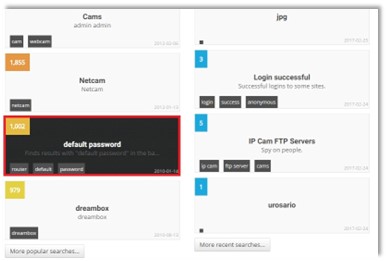
Figure 1. The Shodan’s default passwords
As it’s illustrated in the previous Figure – the Shodan would deal with many different IoT resources and one of the options would be – so called – Default Password. As it’s obvious – there would be around 1,000 devices getting its login details available to the rest of a web population. We would always highlight that a primary role of the Shodan is to serve to research’s community, but – unluckily – many malicious actors would find their interest to exploit such an asset. Indeed, the Shodan is a powerful tool offering a chance to everyone to test its capacities. Through the Figure 2 – we would illustrate how such a Default Password section could get used for getting the IP details as well as the authentication data. That step is illustrated as follows.
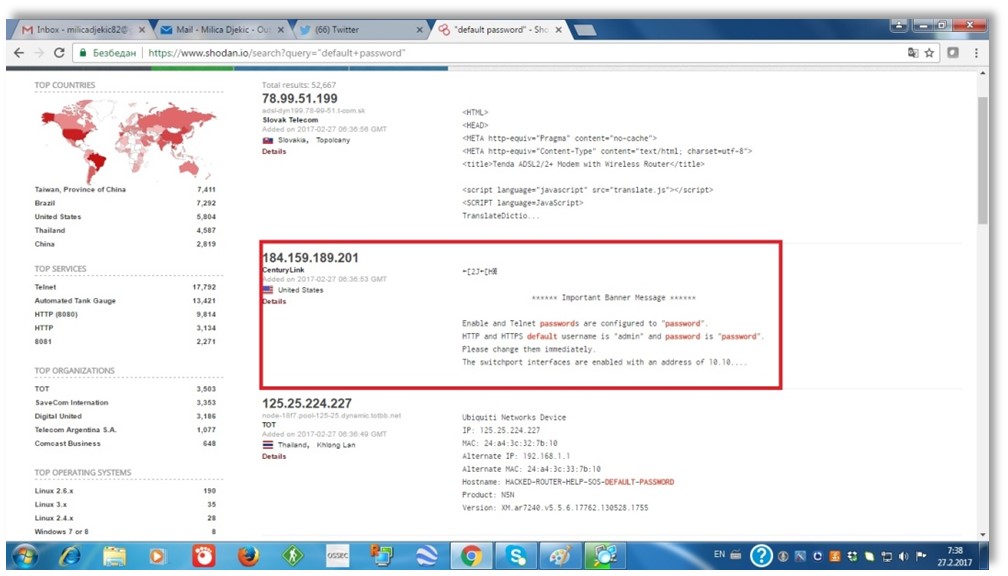
Figure 2. The Shodan’s login details
As it’s given through the Figure 2 – we would select some US IP address offering the login details such as username and password to that IoT configuration. The username here would be ‘admin’ and the password would get ‘password’. In addition, through this book’s chapter – we would like to deal with some of the widely used hacker’s tools that would get analyzed further through this chapter. At this stage – it’s significant to know that for a successful hacking – it’s necessary to get familiar with someone’s IP address as well as his login details. Through the Figure 3, we would illustrate some of this Shodan’s results being covered with more details on.
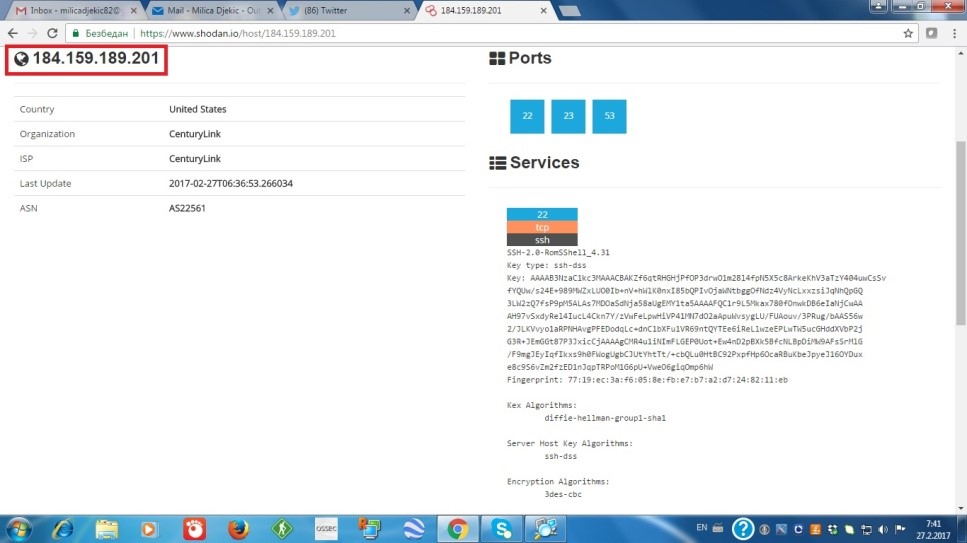
Figure 3. The Shodan’s result details
As it’s clear – any researcher could analyze some of the Shodan’s results trying to figure out how those results could cope with the real-case scenarios. So, what it’s important at this stage are the facts that we got a desired IP address being 184.159.189.201 and some login details being ‘admin’ for a username and ‘password’ for password. It’s important to mention that unbelievably many IoT assets would use a weak authentication and the hackers would through simple guessing obtain an access to someone’s computer or another device being online. Through the coming section of this learning material – we would talk a bit more about some standard hacking tools and try to explain the way of their usage for the system’s exploitation. At this stage, we would end up this part of the book’s chapter with well-known sentence that following of the best practice could save us greatly from unwanted events.
How hacking works in practice
Some of the best known hacking tools are Advanced IP Scanner and Radmin being used to search the network and take a remote control over the targeted devices. These two applications could get in combination or separately, but we would always advise the users to try to combine the both of them. These tools are free of charge and could get downloaded from the internet. The role of the Advanced IP Scanner is to offer some results about a required IP address as well as attempt to do deeper into a network trying to do some penetration of that infrastructure. On the other hands, the Radmin could get considered as a gadget to the Advanced IP Scanner that could offer us an opportunity to take control over any available device. In Figure 4, we would try to deal with such a tool using the well-known IP address of US IoT asset that we found using the Shodan crawler. This illustration is given as follows.
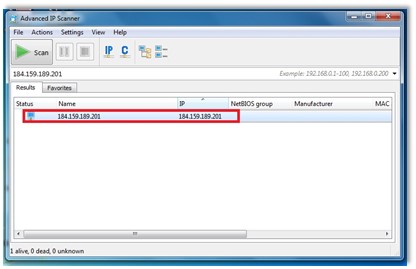
Figure 4. The Advanced IP Scanner with the crawled IP address
As it’s obvious – the Advanced IP Scanner would get the required IP address and make a search trying to identify such a device. We would get an IT asset being visible through this scanning tool. As we suggested – this tool would deal with the remote administration options using the Radmin software. The Figure 5 would illustrate how it works in practice and how it’s possible to hack someone’s IoT asset. Through such an illustration – we would notice that many of scenarios are feasible and also see that making a cyber breach or stealing the confidential information could get a piece of cake to any hacker. In this case, it’s not about the skill because the children would know how to use those tools – it’s more about money which would make someone commit a cybercrime and gets exposed to a risk for a reason that he would leave a trace in a cyberspace anyhow. Such a finding could make an investigation being much easier and increase the chance that such a case would lead to an arrest.
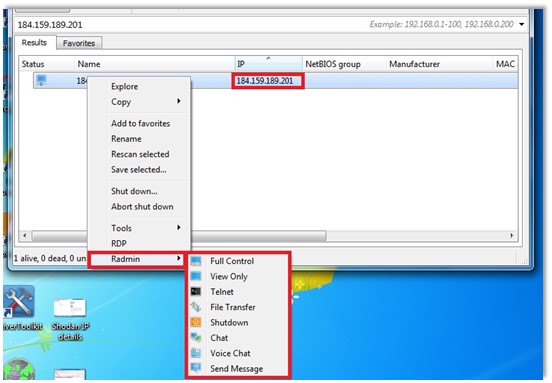
Figure 5. The remote options of an Advanced IP Scanner
As it’s illustrated in Figure 5, the Radmin alternative would offer us many possibilities such as full control, view only, shutdown, chat and so on. Choosing one of these options – you would get an opportunity to login to someone’s computer. In this case, such a device would be an IoT asset being found through the Shodan’s crawler. Finally, all you need is to connect to such a device and apply some of the command being given above. The rest of a job is just a piece of cake!
The ways of cyber prevention
Through this learning material, we would talk a bit more about how these sorts of scenarios could get prevented in a practice. As we would suggest many times – it’s so useful to follow the best practice. In case of preventing the device to get accessible through some of the scariest searching tools – it’s so helpful to try to block your inbound ports as well as use the strong authentication which would offer you much better protection. Also, it could get convenient if you would change the passwords to your system periodically as well as apply more firewall’s options and regularly update your network’s devices such as modems and routers. Finally, this chapter would illustrate us how it’s possible and we must say – easy – to hack someone’s computer, so that’s a reason more to invest into your cyber defense either in private life or at the work.
The final talk
Through this chapter – we would see how our IoT asset would get vulnerable to some of the hacker’s operations. Unluckily to all of us – many critical infrastructures would belong to IoT capacities and those assets could get attacked so easily. In conclusion, we would want to say that the entire expert’s community should work so hard in order to prevent some of these incidents even happen as well as aware people how to help themselves in such a sort of dealing with the threats, risks and challenges.
References:
[1] Djekic, M. D., 2017. The Internet of Things: Concept, Application and Security. LAP LAMBERT Academic Publishing.
[2] Djekic, M. D., 2021. The Digital Technology Insight. Cyber Security Magazine
[3] Djekic, M. D., 2021. Smart Technological Landscape. Cyber Security Magazine
[4] Djekic, M. D., 2021. Biometrics Cyber Security. Cyber Security Magazine
[5] Djekic, M. D., 2020. Detecting an Insider Threat. Cyber Security Magazine
[6] Djekic, M. D., 2021. Communication Streaming Challenges. Cyber Defense Magazine
[7] Djekic, M. D., 2021. Channelling as a Challenge. Cyber Defense Magazine
[8] Djekic, M. D., 2021. Offense Sharing Activities in Criminal Justice Case. Cyber Defense Magazine
[9] Djekic, M. 2019. The Informant Task. Asia-Pacific Security Magazine
[10] Djekic, M. D., 2020. The Importance of Communication in Investigations. International Security Journal
[11] Djekic, M. D. 2019. The Purpose of Neural Networks in Cryptography, Cyber Defense Magazine
[12] Djekic, M. D. 2020. Artificial Intelligence-driven Situational Awareness, Cyber Defense Magazine
[13] Djekic, M. D. 2019. The Perspectives of the 5th Industrial Revolution, Cyber Defense Magazine
[14] Djekic, M. D. 2019. The Email Security Challenges, Cyber Defense Magazine
[15] Djekic, M. D. 2016. The ESIS Encryption Law, Cyber Defense Magazine
[16] Đekić, M. D., 2021. The Insider’s Threats: Operational, Tactical and Strategic Perspective. LAP LAMBERT Academic Publishing.
About The Author
 Milica D. Djekic is an Independent Researcher from Subotica, the Republic of Serbia. She received her engineering background from the Faculty of Mechanical Engineering, University of Belgrade. She writes for some domestic and overseas presses and she is also the author of the books“The Internet of Things: Concept, Applications and Security”and “The Insider’s Threats: Operational, Tactical and Strategic Perspective”being published in 2017 and 2021 respectively with the Lambert Academic Publishing. Milica is also a speaker with the BrightTALK expert’s channel. She is the member of an ASIS International since 2017 and contributor to the Australian Cyber Security Magazine since 2018. Milica’s research efforts are recognized with Computer Emergency Response Team for the European Union (CERT-EU), Censys Press, BU-CERT UK and EASA European Centre for Cybersecurity in Aviation (ECCSA). Her fields of interests are cyber defense, technology and business. Milica is a person with disability.
Milica D. Djekic is an Independent Researcher from Subotica, the Republic of Serbia. She received her engineering background from the Faculty of Mechanical Engineering, University of Belgrade. She writes for some domestic and overseas presses and she is also the author of the books“The Internet of Things: Concept, Applications and Security”and “The Insider’s Threats: Operational, Tactical and Strategic Perspective”being published in 2017 and 2021 respectively with the Lambert Academic Publishing. Milica is also a speaker with the BrightTALK expert’s channel. She is the member of an ASIS International since 2017 and contributor to the Australian Cyber Security Magazine since 2018. Milica’s research efforts are recognized with Computer Emergency Response Team for the European Union (CERT-EU), Censys Press, BU-CERT UK and EASA European Centre for Cybersecurity in Aviation (ECCSA). Her fields of interests are cyber defense, technology and business. Milica is a person with disability.

