Incremental Malicious Update Attack (IMUTA)
By Zia Muhammad and Zahid Anwar, Department of Computer Science, NDSU
Android is the leading operating system in the smartphone industry with more than 71% of the global market share. All Android-based smartphones arrive with a preinstalled application called Google Play Store which provides access to over 2.65 billion mobile applications and games. It is a free, powerful, and prominent platform for both mobile users and application developers.
In 2022 alone, more than 110 billion downloads were recorded through the Play Store. Due to such a high download volume, Google deploys a security tool called the Google Play Protect which scans all uploads in an attempt to root out potentially malicious applications dubbed as malware.
But is this tool self-sufficient and resilient to contemporary cyber-attacks? According to a recent research article published in the Journal of Ambient Intelligence and Humanized Computing (JAIHC), a stealthy cyberattack called an Incremental Malicious Update Attack (IMUTA) can use incremental updates to breach privacy and circumvent Google Play vetting policies. The attack works by users’ trust in Google Play Store as a safe and authentic source of applications and stealthily collects private user data from the device that allows it to evade detection. This article examines how this attack works, why it is dangerous, and what Google should do to prevent it.
The Incremental Malicious Update Attack (IMUTA)
The researchers that developed the proof-of-concept malware aimed to demonstrate how easy it is to exploit customer trust and Google’s policies to circumvent popular voice search applications. The research is published with the title “Circumventing Google Play vetting policies: a stealthy cyberattack that uses incremental updates to breach privacy.” This is how it works:
- Their first step was to upload a benign application called Voice Search to Google Play Store, which allows users to perform everyday actions through voice commands, such as calling someone or looking at the latest news and weather updates. Interesting the application passed Google’s review process and was made public.
- Afterwards, they released a second version of the application, which added some malicious functionality that accessed and used analytics, event logs, performed activity, demographics, and user location tracking. Interestingly Google also accepted this update within a single day.
- The researchers finally released a third version, which really upped the game.. This version created a connection to a storage in the cloud to store data against each hacked phone. It collected contacts, version numbers, applications being used and manufacture, and model details. In addition, Users’ personal data was collected when they opened the application and performed a voice action. Google also accepted this version within a single day.
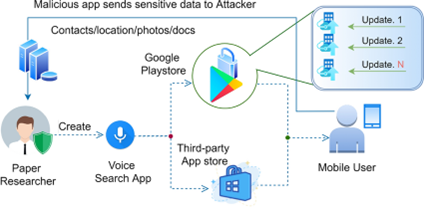
Fig.1: Incremental malicious update attack (IMUTA)
The multi-step approach of the underlined experiment circumvents vetting policies and makes IMUTA successful, a quick overview is provided in Fig.1. Through this attack, researchers were able to collect and exfiltrate private user data to their command-and-control server. The key to their success is incremental malicious updates that apparently builds trust with the server causing no alarms to be raised.
Why this attack is dangerous
This attack is dangerous for several reasons. It evades Google Play Protect security mechanisms by exploiting its relatively lenient trust policies allowing package distribution and feature updates. It exploits users’ trust in the Google Play Store, which is a safe and authentic source of applications. Users are unlikely to suspect that an application downloaded from Google Play Store could become malicious through updates. Users may also grant permissions to the application without checking its functionality or content.
It is not certain that these kinds of attacks are just specific to the Google Play store, and this cannot be assumed that other application distribution platforms are immune. According to the researchers, the chosen voice search application is just one example and can be simultaneously replicated in other popular or sensitive applications such as banking, social media, or healthcare applications.
These kinds of attacks are complex, sophisticated, persistent, and remain undetected for an extended period of time. They can be used for various malicious purposes, such as financial gain, political gain, and sabotage. Moreover, the collected data can be used to perform identity theft, fraud, blackmail, phishing, or espionage.
What Google should do to prevent it
There should be a reevaluation of vetting policies in order to improve the security posture of Google Play to protect its users. For instance, a significant portion of such attacks can be blocked by acquiring information on the updated application module from a developer individually and calculating the similarity index based on the code similarity of the earlier version with the new variant. This similarity index will help to spot significant differences and flag suspicious updates.
Moreover, the updated code should be merged directly with the previous version instead of replacing an application entirely. Currently, a new version entirely replaces the older version, which increases the chances of dynamic code loading and reduces the trackability over malicious injections.
In addition, the security mechanism deployed by Google should perform critical analysis of application updates with the same rigor as initial applications, including checking for maliciousness, hidden intents, requested permissions, provided functionality, and comparing the code of published versions of the application and its updates.
Finally, it is essential to educate users about the risks of downloading and updating applications from any source, even from Google Play Store. They should be encouraged to review each application’s permissions, functionality, and content before installing or updating it. In order to ensure the security and privacy of users, these measures can be significant steps in preventing stealthy malware attacks like IMUTA and maintain its reputation as a trusted provider of Android applications.
About the Author
 Zia Muhammad is a Ph.D. scholar in the Department of Computer Science at North Dakota State University. Zia can be reached online at ([email protected] and https://www.linkedin.com/in/zianoedar/)
Zia Muhammad is a Ph.D. scholar in the Department of Computer Science at North Dakota State University. Zia can be reached online at ([email protected] and https://www.linkedin.com/in/zianoedar/)
 Zahid Anwar is an Associate Professor of Cybersecurity in the NDSU Department of Computer Science and a scholar of the Challey Institute for Global Innovation and Growth. His research focuses on cybersecurity policy and innovative cyber defense. He has authored more than 100 publications in peer-reviewed conferences and journals. He is a CompTIA-certified penetration tester, security+ professional, and an AWS-certified cloud solutions architect. Prior to working in academia, he worked as a software engineer and researcher at IBM T. J. Watson, Intel, Motorola, the National Center for Supercomputing Applications, xFlow research, and CERN. Dr. Anwar received his Ph.D. in computer science from the University of Illinois in 2008.
Zahid Anwar is an Associate Professor of Cybersecurity in the NDSU Department of Computer Science and a scholar of the Challey Institute for Global Innovation and Growth. His research focuses on cybersecurity policy and innovative cyber defense. He has authored more than 100 publications in peer-reviewed conferences and journals. He is a CompTIA-certified penetration tester, security+ professional, and an AWS-certified cloud solutions architect. Prior to working in academia, he worked as a software engineer and researcher at IBM T. J. Watson, Intel, Motorola, the National Center for Supercomputing Applications, xFlow research, and CERN. Dr. Anwar received his Ph.D. in computer science from the University of Illinois in 2008.

