
While the efficacy of Microsoft’s Active Directory as a security mechanism may be debatable, two other points are not. MS AD (Active Directory) is in extremely wide use – 90%-plus by some estimates – and if compromised provides nearly unlimited access throughout the enterprise, often with complete anonymity. Given that virtually all major compromises in the last few years had components that addressed AD, detecting and protecting against attacks targeting AD is – or should be – job-1.
For most of my years of teaching cyber forensics at a university I told my students, “You cannot get a correct answer if you don’t know the right question.” Protecting AD is a perfect example of that. Without solid knowledge of risks associated with Active Directory you simply cannot apply comprehensive countermeasures. Sadly, that intelligence is not available in any single place and, sometimes, is not available at all. That’s where Attivo Networks’ new ADAssessor tool enters the picture. Before we get to the tool, though, let’s explore the problem a bit with a couple of current attacks that have been in the news lately.
A Couple of AD Attack Examples that are Very Hard to Detect
The issue is straightforward. The detection and solution are not. The basic issue is that it is inconvenient to manually authenticate every user in a large enterprise so we create Active Directory forests to do it for us by proxy. The “proxy”, in this case, is the Kerberos ticket that substitutes for the user’s direct sign-in and authentication on a resource-by-resource basis. Attacks against AD may be part of what is termed supply chain attacks which means that by compromising one system, multiple connected systems can become accessible and may be attacked.
Traditionally – and still to a large degree – Kerberos was the authentication tool of choice. Once the legitimate user was properly registered, all he or she had to do was sign into the single sign on (SSO) application. The application would then send the request to the Kerberos server which then issues a “ticket grating ticket” (TGT) that was returned to the point where the user was signing in. The ticket addressed the user’s identity, privileges, allowed resources, and security levels allowed. If the user was permitted to log into the resource requested and was properly authenticated to the Kerberos server, the ticket granting ticket would grant a ticket to log into the resource. If not, login would be refused.
Attacking the ticket granting ticket and spoofing it (it’s really a bit more complicated than that but this will serve for now) allowed the attacker to be any user or resource on the enterprise. This is referred to as a “golden ticket attack”. The “spoofing” occurs when the key used to sign the TGT is compromised. So, it is not the ticket that is spoofed (a ticket forging attack) but, rather, a key distribution attack.
The first step in a Golden Ticket attack is compromising the domain controller. The objective is to steal the an NTLM hash of the Kerberos key distribution account. Using that the mimikatz hacking tool can launch a Golden Ticket attack to obtain a ticket granting ticket. This gives the attacker access to the domain controller as a domain admin allowing unfettered lateral movement across the domain. Once the hash is stolen and a golden ticket obtained, the attack is nearly undetectable.
Another way to harvest AD account credentials is the Kerberoasting attack. Again, this is a post-exploitation attack and can be performed by any user account. The attacker, once inside the network, requests a Kerberos service ticket from the ticket granting service and captures the ticket from memory. The ticket granting ticket is provided when the attacker – using a compromised user account – requests authentication. Once the attacker has the service ticket, he or she extracts it from memory and cracks it off-line.
Another tool that has become very popular with attackers is Bloodhound, a tool that illustrates the relationships in the target AD system. ADAssessor detects faults that would be discovered by bloodhound. There is a fairly complete set of AD exploits – with bloodhound – including some code and user guides on GitHub. This provides a good education on AD vulnerabilities and will help you use ADAssessor more efficiently.
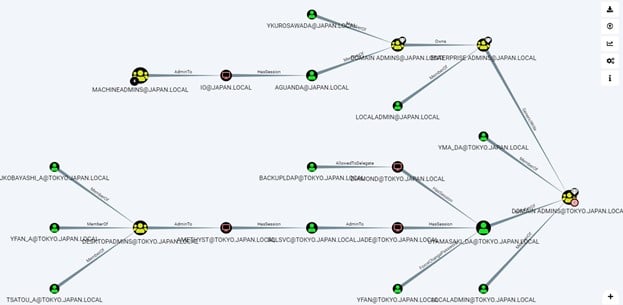
Figure 1 – Bloodhound[1]
These are just two examples – Kerberos Golden Ticket and Kerberoasting – that ADAssessor detects. Now on to the product.
Why ADAssessor?
One of the challenges with detecting AD attacks is that there are many potential vulnerabilities, backdoors, etc. and I know of no single tool that addresses them all successfully. Some are less complicated and standard vulnerability scanning can uncover holes that would permit the attacks. However, successful AD attacks are complicated and a certain level of complexity in the detection tool is a must. ADAssessor meets that criterion handily.
ADAssessor addresses both hygiene-based detections and real-time detections. Real-time detections include such important ones as mass account attacks, password attacks, service creation on the domain controller, DCShadow attack and Skeleton key assessment.
Hygiene-based attacks address best practices, domain-based detections, user-based detections and computer-based detections. All-in-all, ADAssessor can address well over 70 AD-involved exposures. A side-by side comparison with other AD scanners clearly establishes that ADAssessor is significantly more comprehensive in the issues it detects. The tool, however, not only detects these holes, it gives suggested ways to close them and identifies the likely hacker tools used to compromise the AD.
The tool’s UI is, fundamentally, organized into two views: Dashboard and Exposures. From the two views you can drill down for more information. For example, Figure 2 shows the Exposure view for the top four exposures: Credential harvesting from domain shares, Dangerous access rights delegation on critical objects, Unprivileged users in AdminSDHolder ACL (note the example above) and Unusual accounts with replication permission (DCSync).
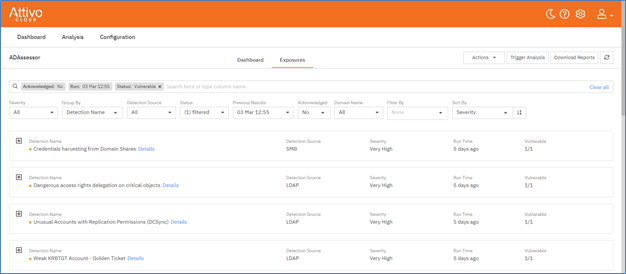
Figure 2 – ADAssessor Partial Exposure Menu
Each exposure has a detailed description that requires only a single click to access from the Exposures menu. Figure 3 shows the description for the Unusual accounts with replication permission. Note the level of available detail including mitigation steps, known attack tools and references that help understand the exposure. This level of detail and its extraordinarily simple accessibility are among the best outward features of this tool. Gaining the intelligence on a system’s vulnerabilities is not of much use without an understanding of the problem, its details and solutions.
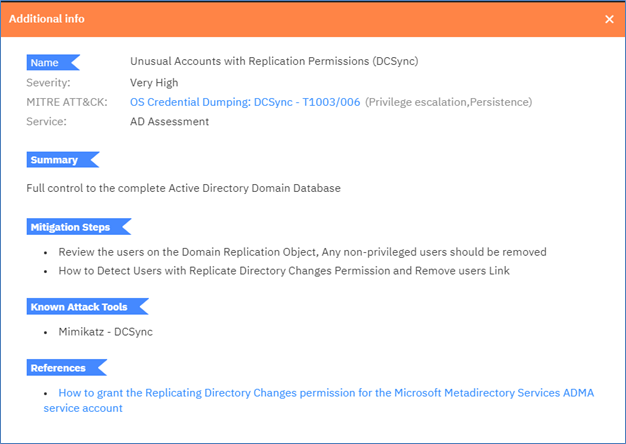
Figure 3 – Exposure Details for Unusual Accounts with Replication Permissions
But there is more detail available that leads directly to the remediation of the problem. Figure 4 shows the specific detection details for Credential harvesting from domain shares. Note that this is an example of intuitive trouble shooting from the general to the specific:
Exposure —> Exposure Details —> Detection Items
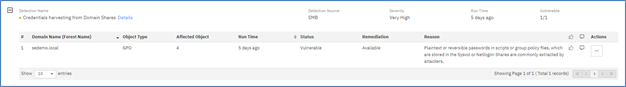
Figure 4 – Specific Detection Details
So, we can see that the big advantage here not only is the depth to which the tool goes to identify vulnerabilities specifically in the AD world and coaching in remediation, it also detects file-less and trace-less threats that use Active Directory to “live off the land”. These vulnerabilities and attacks are very hard to detect and, therefore, hard to remediate. Also, as we showed in the examples of attacks at the start of this analysis, ADAssessor is able to detect vulnerabilities that are very hard to detect otherwise.
The typical way to identify AD vulnerabilities has been AD pen testing using red team tools such as mimikatz and bloodhound. This is a hit-and-miss strategy at best and at worst – when the pen testers are not extraordinarily skilled – mostly miss. The other possibility is to use standard AD assessment tools that give little more than a general look at the AD environment, often cannot tell if the AD has been compromised and give little to no insight for remediation.
Finally, one can use a collection of AD audit assessment tools that address pieces of the AD environment. These are time consuming to use and probably are not comprehensive enough. Certainly, you can expect to miss something important. Comprehensive packages are not as complete as ADAssessor nor do the exhibit ADAssessor’s depth and usability.
Opinion
From the opening dashboard (see Figure 5) to the deep analysis, ADAssessor fills the bill completely. I usually am leery of vulnerability tools that have a set of vulnerabilities that they are restricted to. However, this one is updated so frequently and – since it is cloud-based – so uniformly that I do not see that as an issue at all and I hardly would consider it a restriction. You can count on the tool being completely current, including zero-days (or newer).
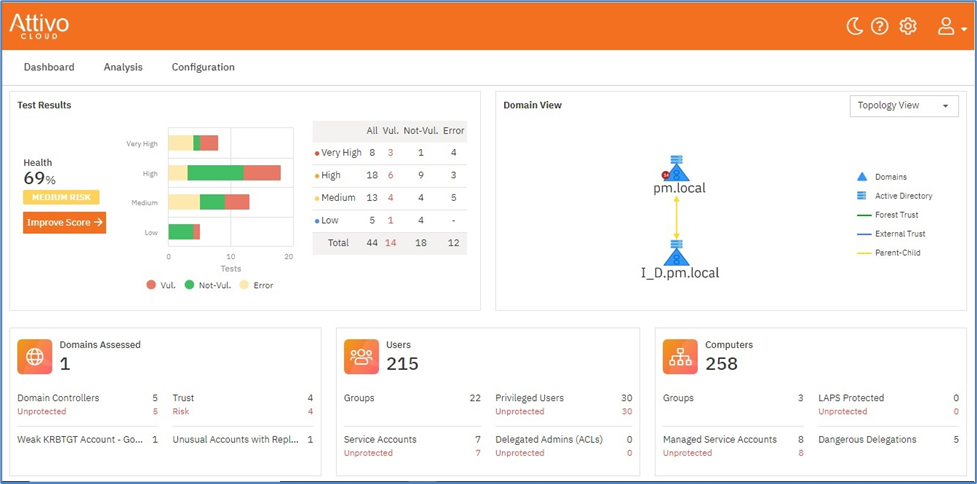
Figure 5 – Opening Dashboard
The opening dashboard not only gives the expected overview of AD health status, it leads directly to drill-downs with additional information (for example, the Exposures drill-down). The level of detail is consistent with the very high level of comprehensive testing and this tool, by itself, may be the only AD assessment tool you’ll need. You have a complete view of AD status at any time and can work on remediation in a timely manner.
P. R. Stephenson, PhD, CISSP (ret)
Publisher of Future inTense
Exclusively at Cyber Defense Magazine
[1] Screenshot courtesy of MCP Mag – https://mcpmag.com/articles/2019/11/13/bloodhound-active-directory-domain-admin.aspx

