Exploring the Future of Cybersecurity at the 2023 RSA Conference
By Kylie M. Amison, Technical Reporter, Cyber Defense Magazine
As the recipient of Cyber Defense Magazine’s 2023 Young Women in Cyber Award, I was granted the incredible opportunity to not only attend the 2023 RSA conference but was also able to interview dozens of C-level officers of both emerging and established tech companies. This allowed me the chance to witness firsthand the passion and innovation driving the industry forward. The innovating solutions covered were diverse, ranging from collective defense against undetected malware to the latest enterprise IoT security platform capable of remediating and repatriating any and all IoT devices.
In the following trip report, I will discuss five different companies and reflect on the details of the discussions had with each, adding some insightful key takeaways.
“The Future of AI in Cybersecurity” with Wib Security, Interview and Discussion featuring CTO Chuck Herrin
In light of the growing security threats in today’s landscape, companies’ focus on forward thinking solutions is particularly relevant and necessary. One of the most significant topics discussed throughout all of my conducted interviews and attended presentations was the future of AI in cybersecurity, with many industry experts expressing optimism about its potential to strengthen defense strategies. Although it was acknowledged that attackers currently hold the upper hand and are most definitely leveraging generative AI/ML to carry out swift and wide-ranging social engineering attacks, some CISOs voiced concerns that organizations may be adopting new technologies and approaches before fully understanding them, indicating a need for caution and thorough testing to ensure efficacy and avoid unintended consequences.
Chuck Herrin, the CTO at Wib Security, an API security company that serves as a one-stop-shop for all things API security, emphasized the importance of distinguishing between tasks that require human intervention and those that cannot be automated, reflecting the need for organizations to proceed with caution when utilizing AI in cybersecurity. “There’s a difference in my head between automating a repeatable process, and [executing] creative automation, and what we’re crossing the Rubicon now into creative automation, with most users not really understanding it, and the channel that we’re doing it is via APIs” [1].
AI is especially prevalent when discussing APIs—API traffic accounts for 91% of traffic in an organization, and most AI is delivered through these APIs [1]. Pair this with the fact that most defenders are only aware of about half of their APIs in use, and you’re left with an incomplete threat model. This obviously raises a huge challenge with actually understanding and assigning risk values to what’s happening across these interfaces and within the backend systems and data they expose. With deep expertise in the intricacies of API security, Wib Security has developed the Fusion Platform (see Figure 1) as a comprehensive solution for identifying, assessing, and mitigating API risks. Fusion platform employs advanced scanning techniques to thoroughly analyze API endpoints and detect vulnerabilities such as injection attacks, broken authentication, insecure data transmission and inadequate access controls.
As Chuck put it, most of cybersecurity is just doing the basics really well. Unfortunately, these basics have been and will be overlooked or neglected in favor of more advanced and flashy security measures. This proves to be concerning as its clear that we don’t yet fully understand the old attack surface, never mind the new one that will evolve at a rapid pace with the favoring adoption of AI. This seems to be a reoccurring theme, adoption before security. Unfortunately, it’s just what humans do.
Figure 1: Wib Security’s Fusion Platform
“Owning the Unknown” with Unknown Cyber, Interview and Discussion featuring CEO James Hess
Among the notable technologies I came across, an exciting one was with Unknown Cyber, a company that conducts automated deep static analysis of code and reverse engineering workflows to identify new viruses and malware that are often missed by antivirus and sandbox solutions, thereby achieving scale without compromising accuracy or time. The proprietary technology discussed is the result of over a decade of research funded by U.S. Department of Defense and independently evaluated by MIT. Cythereal MAGICTM, utilized by McAfee as part of their services, is a web-based platform that specializes in malware genomic correlation, which is a fascinating topic in and of itself.
Think of malware genomic correlation as an exploration into the genetic characteristics of malicious software, revealing hidden connections and patterns among different malware samples. Similar to how biological genomic analysis compares DNA sequences to identify relationships between organisms, malware genomic correlation compares the assembly instruction level code of malware samples to uncover similarities and potential relationships.
Unknown Cyber’s proprietary Cythereal MAGICTM leverages this paradigm, employing it to conduct semantic similarity analysis of programs. By focusing on the semantics of the program, rather than the structural or behavioral characteristics, MAGICTM is able to provide quite insightful results. The system can identify similarities between submitted samples, detect variants of those samples from its database, and then generate YARA rules for searching other services such as VirusTotal [2]. Compared to its market competition, MAGIC offers improved effectiveness, particularly in identifying targeted attacks involving polymorphic variants.
The Unknown Cyber mission of “Owning the Unknown,” resonates deeply with a prominent quote from former United States Secretary of Defense, Donald Rumsfeld, who said, “Reports that say that something hasn’t happened are always interesting to me, because as we know, there are known knowns; there are things we know we know. [But] there are also unknown unknowns – the ones we don’t know we don’t know. And if one looks throughout the history of our country and other countries, it is the latter category that tends to be the difficult ones” [3]. Unknown Cyber’s mission of embracing the concept of unforeseen risks by identifying new viruses and malware exemplifies the commitment to innovation and pushing the boundaries of cybersecurity.
“Ransomware Resurgence: Emerging Trends, Threat Actors, and Cybersecurity Strategies” with Black Kite, Discussion and Research Report Synopsis featuring Head of Research Ferhat Dikbiyik
The rapid and innovative trajectory of cyber security technology is mirrored by the adversaries and their arsenal of tools, including the ever-evolving landscape of ransomware. Ransomware groups have emerged as formidable adversaries causing widespread financial and operational disruptions. After speaking with Ferhat Dikbiyik, Head of Research at Black Kite, and reading his research report on the 2023 Ransomware Threat Landscape, I was able to gain valuable insights into the latest trends in ransomware attacks. The report analyzes publicly named ransomware victims and identifies key trends and statistics, shedding light on the resurgence of ransomware attacks and the challenges faced by organizations globally.
The report finds that ransomware attacks have resurged in 2023 with the number of victims nearly doubling from last year. After an analyzation of 2,708 ransomware victims, the report found that the top targeted industries were manufacturing (19.5%), followed by professional, scientific and technical services (15.3%), and educational services (6.1%). Geographically, the United States was the top targeted country, accounting for 43% of victim organizations. The report also found that new ransomware gangs have emerged in 2023, including names like Royal, BianLian, and Play.
In addition, the report highlighted the rise of encryption-less ransomware, which emphasizes the importance of data protection, regulatory compliance, and business interruption risks posed by traditional encryption-based attacks. It also sheds light on the targeting of companies with annual revenues of approximately $50M to $60M, with third-party vendors often being exploited for client information extortion. The Ransomware Susceptibility IndexTM (RSITM) introduced in the report, provides a measure of an organization’s vulnerability to ransomware attacks. Over 70% of ransomware victims analyzed had an RSITM value above the high-risk threshold, indicating their susceptibility. The identified common indicator among victims includes poor email configuration, recent credential leaks, public remote access ports, out-of-date systems, and IP addresses associated with botnet activity [4].
The dynamic and unpredictable nature of cyber threats, particularly ransomware attacks, poses a constant challenge for organizations worldwide. Ransomware groups have evolved into tech like entities, adopting strategies to maximize their illicit businesses. This poses a challenging and uneven playing field for cybersecurity professionals defending against ransomware attacks.
By understanding the complexities of the ransomware landscape in 2023, recognizing patterns, and acknowledging the challenges, organizations can make informed decisions about cybersecurity strategies and reduce their vulnerabilities. Both his research report and the discussion I had with Ferhat provide valuable insight into the evolving ransomware landscape and is useful in equipping security professionals with the crucial data needed to combat these rapidly growing and resourceful adversaries.
I think it’s important to remember that the evolution of technology is a double-edged sword. While it fuels innovation and unlocks new business prospects, it also amplifies the vulnerability of organizations. As the threat of ransomware continues to evolve, organizations must adapt their cyber security strategies, invest in the right defenses, and remain vigilant to mitigate the risks posed by these malicious attacks.
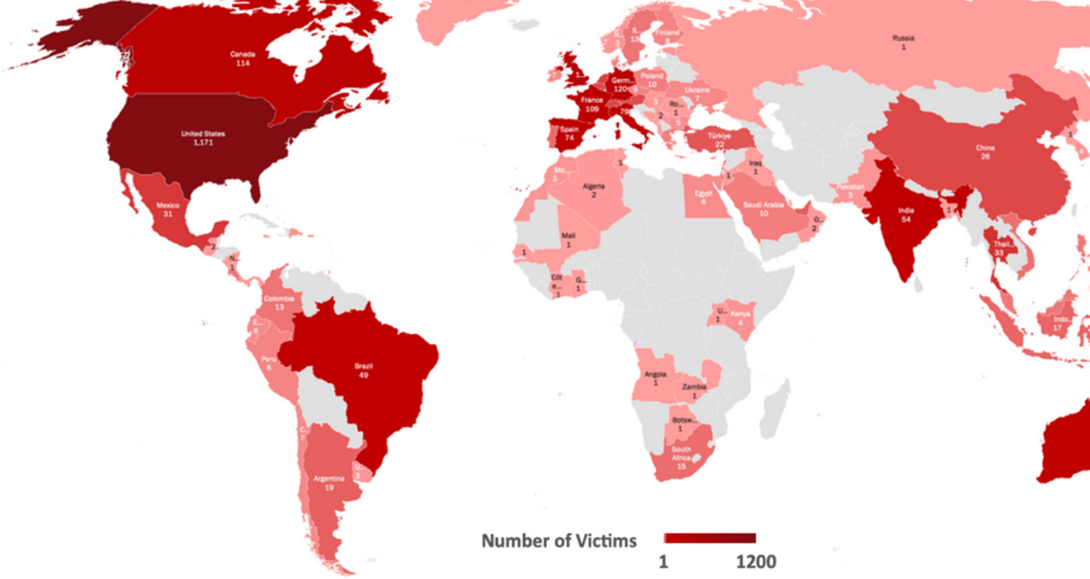
Figure 2: Ransomware Attacks Across the Globe
“Powering Proactive Security with Automated Verification and Monitoring to Keep Your IoT Devices Secure” with ViaKoo, Interview and Discussion featuring CEO Bud Broomhead
As just previously discussed above, cyber threats are evolving at an alarming rate. Organizations require cutting-edge solutions to stay ahead of their adversaries and safeguard their valuable assets. I had the opportunity to sit down with Bud Broomhead, CEO of ViaKoo, a leading cybersecurity company that has emerged as a trailblazer in this realm, offering innovative services that provide comprehensive protection against these emerging threats. The proliferation of IoT devices has revolutionized various sectors, offering enhanced efficiency and convenience. However, the widespread utilization of IoT devices has also, of course, introduced new cybersecurity challenges. ViaKoo has positioned itself as an innovator in addressing these challenges by offering services focused on IoT device remediation and repatriation.
The number of IoT devices deployed in our daily lives is staggering. In fact, during our interview, the ViaKoo team and I pointed out at least ten different IoT devices in the small hotel conference room we were in. From smart home devices and industrial sensors to thermostats and physical cameras, IoT devices have permeated various industries, streamlining operations and enhancing user experience.
However, the sheer volume and diversity of IoT devices present significant security risks as they become entry points for attackers. ViaKoo recognizes this inherent vulnerability and has developed pioneering solutions to remediate and repatriate IoT devices effectively. At the core of Viakoo’s offerings is their automated verification platform (Figure 3), Viakoo Action PlatformTM, a solution that defends IoT attack surfaces and ensures every enterprise IoT device is 100% visible, operational, and secure.
This technology actively monitors the health and functionality of IoT devices ensuring they operate as intended. Viakoo’s platform incorporates proactive monitoring capabilities as it continuously collects real-time data on performance metrics and network connectivity. In addition to monitoring, they also offer issue detection and alert features for each respective IoT device in efforts to facilitate timely remediation actions.
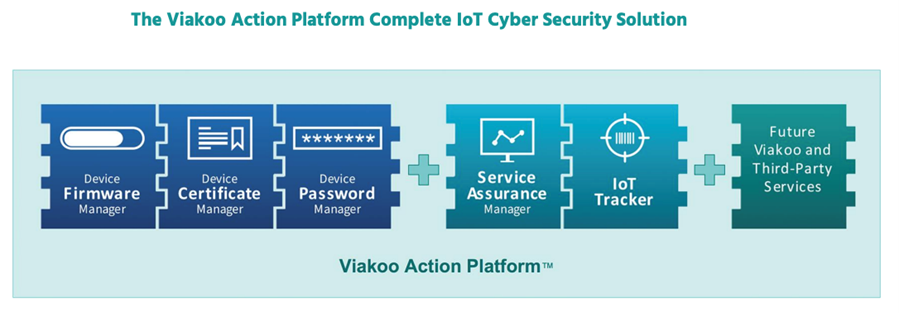
Figure 3: Viakoo Action PlatformTM
ViaKoo’s innovative approach extends beyond remediation and repatriation, encompassing comprehensive IoT device management. They provide organizations with a centralized platform to monitor, control, and secure their IoT device ecosystems. Through the centralized management system, organizations gain enhanced visibility into their IoT infrastructure, allowing them to detect anomalies, apply security patches, and enforce access controls effectively. Securing IoT devices is paramount as they play an obvious role in critical operations across industries. In our ever increasingly interconnected world, where IoT devices are becoming pervasive, ensuring robust security measures is imperative in safeguarding assets and protecting privacy.
“Innovative Email Security Solutions” with Cofense, Interview and Discussion featuring VP CISO Tonia Dudley and Principal Threat Advisor Ronnie Tokazowski
In an era where email serves as a primary communication channel for organizations, and malicious phishing emails on the rise by 569% [6], the importance of diligently implemented email security measures cannot be overstated. I had the pleasure of sitting down with both Tonia Dudley, VP CISO at Cofense and her colleague, Principal Threat Advisor Ronnie Tokazowski as we discussed the capabilities of the services and products offered at Cofense, a leading provider of email security solutions.
As cybercriminals continue to exploit the vulnerabilities within email systems, Cofense has emerged as a formidable ally in the battle against phishing, malware, and other malicious threats. With email serving as a primary channel for communication and business operations, organizations face obvious substantial risks from targeted attacks that aim to exploit unsuspecting users. With advanced threat intelligence capabilities, Cofense technology is able to identify and mitigate sophisticated email-based threats. By leveraging real time data, machine learning, and behavioral analysis, it proactively detects and neutralizes malicious emails, empowering organizations to stay one step ahead of cyber adversaries.
In addition, we discussed Cofense’s state-of-the-art phishing simulation and awareness training platform. This interactive solution helps organizations educate employees about the latest phishing techniques, equipping them with the knowledge and skills to recognize and report suspicious emails. By fostering a culture of security fairness conferences training platform fortifies the human element of defense, creating a robust line of defense against email-based attacks.
My Perspective on RSA and the Cyber Defense Magazine
Out of the numerous things winning Cyber Defense Magazine’s Young Women in Cyber Award has left me with, picking the minds of the innovative geniuses who lead our world in developing groundbreaking cybersecurity technology has given me a high that I will not come down from. It was such an inspirational experience and has gotten me so excited for my own future within the industry. What an exhilarating time it is for technology. However, we must be mindful of the unparalleled challenges we will face as we navigate the uncharted territories of innovation and its possibilities.
References
[1] C. Herin, “Wib Securiy – Real World Case Studies: How API attacks are evolving and how to protect your organization,” San Francisco 2023 RSA, Apr. 26, 2023.
[2] P. S. Paranjape Sameer, “Did You Check Your Quarantine?!,” McAfee Blog, Oct. 28, 2019. https://www.mcafee.com/blogs/other-blogs/mcafee-labs/did-you-check-your-quarantine/ (accessed May 22, 2023).
[3] “Known and Unknown: Author’s Note » About » The Rumsfeld Papers.” https://papers.rumsfeld.com/about/page/authors-note (accessed May 22, 2023).
[4] “2023_Ransomware_Report_Black_Kite.pdf.” Accessed: May 22, 2023. [Online]. Available: https://blackkite.com/wp-content/uploads/2023/04/2023_Ransomware_Report_Black_Kite.pdf
[5] “Viakoo-Action-Platform-Data-Sheet_v10.pdf.” Accessed: May 22, 2023. [Online]. Available: https://www.viakoo.com/wp-content/uploads/2022/01/Viakoo-Action-Platform-Data-Sheet_v10.pdf
[6] “Phishing Protection Solutions | Cofense Email Security,” Apr. 22, 2022. https://cofense.com/ (accessed May 22, 2023).
About the Author
 Born and raised in Hamilton, New Jersey, I now reside in the DC metropolitian area after recently becoming a George Mason University alum. While at GMU, I obtained my Bachelor of Science degree in Cybersecurity Engineering with a minor in intelligence analysis. Along with writing technical pieces for CDM, I am working full time at a leading mobile security company, NowSecure, as an Application Security Analyst where I do all types of fun things like exploit vulnerable apps, secure mobile application development, and contribute to exciting projects and important initiatives that are consistently highlighted thought the security industry. In addition, I also work part time with startup company, Auspex Labs, as a Cybersecurity Software Developer, where I am the main developer on DiplomacyTM, a geopolitical threat intelligence engine that combines a broad assortment of metrics and NLP sentiment analysis to calculate nuanced and real-time threat scores per nation state. Working at Auspex has been pivotal in my knowledge in creating secure software and has given me the opportunity to not only develop my first product, but to also start my own startup company, productizing the software and capabilities created in DiplomacyTM. Which brings me to my final endeavor, I am presently co-founder and CTO of Xenophon Analytics, a company that grew from shared interests in international political affairs and my project of building the geopolitical risk engine. When I’m not researching or coding, you can find me watching anime, reading Sci Fi, painting, or playing with my dogs! My ultimate goal in life is to learn every single day, and I’m proud to be doing just that. I love to chat about all things tech and security, so feel free to shoot me a message anytime.
Born and raised in Hamilton, New Jersey, I now reside in the DC metropolitian area after recently becoming a George Mason University alum. While at GMU, I obtained my Bachelor of Science degree in Cybersecurity Engineering with a minor in intelligence analysis. Along with writing technical pieces for CDM, I am working full time at a leading mobile security company, NowSecure, as an Application Security Analyst where I do all types of fun things like exploit vulnerable apps, secure mobile application development, and contribute to exciting projects and important initiatives that are consistently highlighted thought the security industry. In addition, I also work part time with startup company, Auspex Labs, as a Cybersecurity Software Developer, where I am the main developer on DiplomacyTM, a geopolitical threat intelligence engine that combines a broad assortment of metrics and NLP sentiment analysis to calculate nuanced and real-time threat scores per nation state. Working at Auspex has been pivotal in my knowledge in creating secure software and has given me the opportunity to not only develop my first product, but to also start my own startup company, productizing the software and capabilities created in DiplomacyTM. Which brings me to my final endeavor, I am presently co-founder and CTO of Xenophon Analytics, a company that grew from shared interests in international political affairs and my project of building the geopolitical risk engine. When I’m not researching or coding, you can find me watching anime, reading Sci Fi, painting, or playing with my dogs! My ultimate goal in life is to learn every single day, and I’m proud to be doing just that. I love to chat about all things tech and security, so feel free to shoot me a message anytime.
Kylie can be reached online at [1] or on LinkedIn https://www.linkedin.com/in/kylie-m-amison-8665a7194/

