Tavis Ormandy, a security expert at Google Project Zero, has discovered a critical remote code execution vulnerability in the Cisco WebEx browser extension.
Google Project Zero researcher Tavis Ormandy has discovered a critical remote code execution vulnerability in the Cisco WebEx browser extension. Cisco’s initial fix does not appear to be complete, which has led to Google and Mozilla temporarily removing the add-on from their stores.
The popular Google Project Zero researcher Tavis Ormandy has discovered a critical code execution vulnerability in the Cisco WebEx browser extension. The flaw has a significant impact considering that the WebEx extension for Google Chrome has roughly 20 million active users.
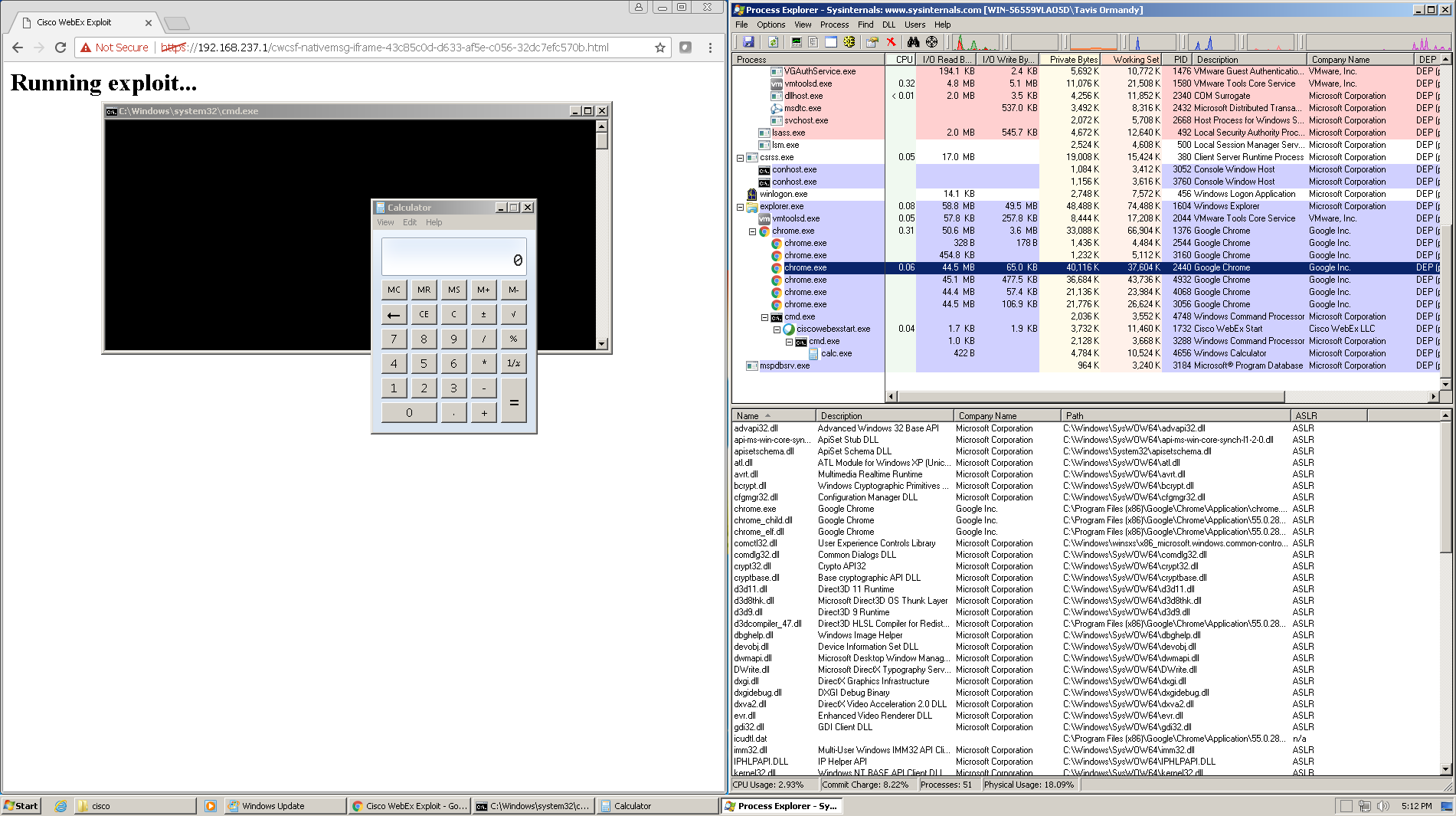
The expert discovered that an attacker can trigger the vulnerability by using any URL that contains a “magic” pattern. The flaw could be exploited to remotely execute arbitrary code on the targeted WebEx user’s system by tricking victims into visiting a specially crafted website.
Cisco tried to fix the issue limiting the magic URL to https://*.webex.com and https://*.webex.com.cn domains but the Google researcher highlighted the it could still be exploited due to a potential cross-site scripting (XSS) flaw on webex.com.
“The extension works on any URL that contains the magic pattern “cwcsf-nativemsg-iframe-43c85c0d-d633-af5e-c056-32dc7efc570b.html”, which can be extracted from the extensions manifest. Note that the pattern can occur in an iframe, so there is not necessarily any user-visible indication of what is happening, visiting any website would be enough.” states the advisory published by Ormandy.
“The extension uses nativeMessaging, so this magic string is enough for any website to execute arbitrary code (!!).”
The expert discovered that even without the XSS an attacker can remotely execute arbitrary code on the target system if the victims click “OK” when they are prompted to allow a WebEx meeting to launch on the rogue website.
Ormandy published and PoC exploit and published a demo here for testing. A successful execution of the demo needs a working WebEx installation on the victim machine. Below the link to the PoC exploit:
https://lock.cmpxchg8b.com/ieXohz9t/

Mozilla representatives also remarked that webex.com does not use HTTP Strict Transport Security (HSTS) and Content Security Policy (CSP).
“If I’m an adversary and I can find a single XSS on that domain, all I need to do at any point in the future is intercept an outgoing HTTP request from Chrome, insert a 302 redirect, and I have an instant RCE on who knows how many machines?” said April King, information security engineer at Mozilla.
Both Google and Mozilla have decided to remove the WebEx extension from their stores until Cisco releases will solve the issue.
[adrotate banner=”22″]