“VirusTotal gives you opinions. Hybrid Analysis gives you behavior. Unknown Cyber gives you the truth in the code—before the malware even runs. That’s how we blow them both away.”
— James Hess, CEO, Unknown Cyber
Scan Now — See What Others Miss
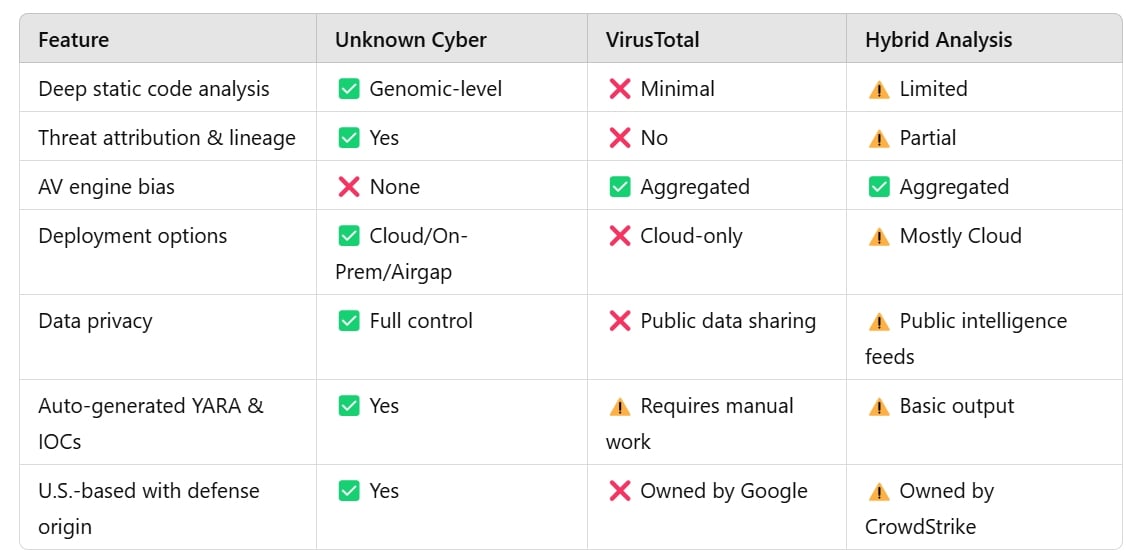
🔍 Why Choose Unknown Cyber Over VirusTotal & Hybrid Analysis
Scan It Smarter — Go Beyond VirusTotal
1. Deeper Static Analysis — “Genomic” Code Understanding
- Unknown Cyber uses deep static code analysis to inspect malware at the genomic level, identifying malware lineage, code reuse, and advanced obfuscation techniques.
- VirusTotal primarily aggregates results from multiple AV engines and dynamic/sandbox analysis. It doesn’t perform in-depth reverse engineering or code lineage analysis.
- Hybrid Analysis relies heavily on behavioral (dynamic) analysis. While it’s useful for quick triage, it often misses deeply embedded static code threats or sophisticated polymorphic malware.
✅ Advantage: Unknown Cyber identifies threats before they execute, uncovering unknown malware families and zero-days that evade behavioral detection.
Reveal the Undetected — Free Scan
2. Private, Secure, U.S.-Based Technology
- Unknown Cyber is a U.S.-origin, defense-funded technology platform—built to meet the security needs of government, critical infrastructure, and enterprise customers.
- VirusTotal is owned by Google (Alphabet), with global infrastructure and a data-sharing model that may raise data privacy concerns, especially for defense or compliance-sensitive industries.
- Hybrid Analysis (owned by CrowdStrike) also contributes to public intelligence feeds, which some enterprises may avoid when handling sensitive or proprietary malware samples.
✅ Advantage: Unknown Cyber provides full control and confidentiality, with no third-party data sharing—ideal for classified, regulated, or proprietary environments.
Analyze Like a Threat Hunter — Start Free
3. Automated Reports and Actionable Intelligence
- Unknown Cyber outputs machine-readable IOCs, YARA rules, MITRE ATT&CK mappings, and threat actor attribution—automatically, with context.
- VirusTotal provides raw AV verdicts and static/dynamic scan details but lacks deep contextual threat reporting unless augmented with external tools.
- Hybrid Analysis gives decent report summaries but does not automatically generate defensive countermeasures (e.g., hardened YARA rules or detection signatures).
✅ Advantage: Unknown Cyber accelerates SOC workflows with ready-to-use outputs—immediately feeding into SIEM, SOAR, or hunting tools.
Deep Scan Now — Genomic Malware Analysis
4. Portable, On-Prem, and Air-Gap Friendly Deployments
- Unknown Cyber offers cloud, on-prem, and portable/air-gapped versions—critical for MSSPs, field operatives, and military/civil defense.
- VirusTotal is primarily cloud-based, with limited local deployment options.
- Hybrid Analysis is a hosted service with limited offline support.
✅ Advantage: Unknown Cyber adapts to mission-critical environments where internet connectivity is restricted or data exfiltration is prohibited.
Private. Powerful. Free. Scan Now.
5. No AV Bias or Signature Dependency
- Unknown Cyber is independent of antivirus vendors, providing unique intelligence based on its own patented analysis engine.
- VirusTotal aggregates data from 70+ AV engines—great for consensus, but can reinforce false positives/negatives and vendor bias.
- Hybrid Analysis can also be influenced by AV and sandbox vendor logic.
✅ Advantage: Unknown Cyber provides original, vendor-neutral insights, reducing noise and improving fidelity.
Start Your Free Scan — Discover the Code Truth
🚀 Final Takeaway
Unknown Cyber is ideal for:
- Organizations handling sensitive or classified files
- Teams seeking automated malware intelligence and zero-day detection
- Environments where sandboxing alone isn’t enough
- Situations that demand air-gap or on-prem analysis
It’s not just about scanning malware—it’s about understanding it before it acts, with precision, privacy, and actionable intelligence.
Try It Free — Uncover Hidden Malware in Seconds
About the Author
 James is the CEO of Unknown Cyber. Commercialized from DARPA research, Unknown Cyber identifies unknown malware by automatically Unpacking, Deobfuscating, Reverse Engineering and Attributing new malware variants before the rest of the world. James is an Army Intelligence Officer and Aviator and has led and Commanded some of their newest organizations during his 24+ years of service. He was member of the first Louisiana Cyber Defense Incident Response Team and lead the 75th Innovation Command’s Huntsville Unit before becoming Cyber Fusion Officer at the Army Reserve Cyber Protection Brigade. He is now an instructor for the Army Command and General Staff College. Prior to commissioning, he operated in Iraq as a USMC Scout Sniper for 3/23 Marines. He holds Master Degrees in Business, IT Management, and Data Science. He has a research background using neural networks to do feature recognition for remote sensing and is faculty for the Cybersecurity Program at Tulane University. He brought the first Hacking for Defense program to Tulane University which realized solutions for NSA, and The Air Force’s New 350th Spectrum Warfare Wing. James has judged in multiple rounds of Army Expeditionary Technology Search sponsored by the Assistant Secretary of the Army for Acquisition, Logistics, and Technology. He has consulted for multinational Corporations, multiple startups, and realized both OTA and SBIR selection from the Army and Air Force. He has demonstrated results in difficult environments of high uncertainty and solves problems as an approachable change manager who recognizes the strengths of team members and emphasizes them to create positive results for his Organization.
James is the CEO of Unknown Cyber. Commercialized from DARPA research, Unknown Cyber identifies unknown malware by automatically Unpacking, Deobfuscating, Reverse Engineering and Attributing new malware variants before the rest of the world. James is an Army Intelligence Officer and Aviator and has led and Commanded some of their newest organizations during his 24+ years of service. He was member of the first Louisiana Cyber Defense Incident Response Team and lead the 75th Innovation Command’s Huntsville Unit before becoming Cyber Fusion Officer at the Army Reserve Cyber Protection Brigade. He is now an instructor for the Army Command and General Staff College. Prior to commissioning, he operated in Iraq as a USMC Scout Sniper for 3/23 Marines. He holds Master Degrees in Business, IT Management, and Data Science. He has a research background using neural networks to do feature recognition for remote sensing and is faculty for the Cybersecurity Program at Tulane University. He brought the first Hacking for Defense program to Tulane University which realized solutions for NSA, and The Air Force’s New 350th Spectrum Warfare Wing. James has judged in multiple rounds of Army Expeditionary Technology Search sponsored by the Assistant Secretary of the Army for Acquisition, Logistics, and Technology. He has consulted for multinational Corporations, multiple startups, and realized both OTA and SBIR selection from the Army and Air Force. He has demonstrated results in difficult environments of high uncertainty and solves problems as an approachable change manager who recognizes the strengths of team members and emphasizes them to create positive results for his Organization.
