By Milica D. Djekic
The role of this case study is to explain how it’s feasible to exploit some business assets using the IoT search engines and some hacking tools. As it’s known – the IoT crawlers give us back the IP addresses and some additional information for a certain criterion being sent as a request. In this chapter, we would apply the Censys searching tool for crawling the web in a quite wide context, so the users of this book should simply follow the given instructions. In addition, the provided business asset would get correlated with the Post, Telecommunication and Internet Company which would be one of the leading domestic businesses in Republic of Serbia.
How to target a certain business
When we made a decision to deal with this book’s chapter – the first question we got was which business to choose as a quite convenient case study. As we are from Republic of Serbia, we were thinking about some domestic business possibly belonging to a public sector. Finally, we made a decision to select the PTT Net Company being the leading post, telecommunication, cable TV and internet provider. So, it’s quite clear that such an asset could get included into a critical infrastructure for a reason – in case of its collapse many people would stay without many things meaning a lot to them. Practically, we would appeal to all defense and intelligence services in Republic of Serbia or wider to pay a special attention to these sorts of assets, because their collapse could cost the country a lot. Well, it appears that we would choose the strategically important business to deal with. For example, we could try to deal with some trading organizations, but to be honest – we would get no information about their vitally significant web servers using the Censys as our searching tool. Next – in a Figure 1 – we would show a typical business illustration being accessible through the web.

Figure 1. The business with the rising indications
The first thing we would do in this case would be searching the web using a standard Google crawler. We would select the keywords being ‘PTT Net’ and get offered many results. In our case, we would highlight only one of them getting closely correlated with our searching criteria. Through our research – we would think deeply about the differences between the Google and Censys crawlers and we would come to a conclusion that Google would offer us the web content being visible to a browser, while Censys would go deeper and offer us infrastructure that would include the web servers, devices being connected to the internet and much more. On the other hand, the Google got suitable for quite surface searches offering as the results which got some sort of the web interface such as websites, webpages and web presentations. In addition, the Censys is so serious product giving us the IP addresses of devices being the part of the web. Sometimes it’s possible to get some webpage as a result of the Censys search, but in that case – you should get aware that such a result must be correlated with some of the IoT assets. In Figure 2, we would illustrate the result of the Google search for a ‘PTT Net’ keyword.
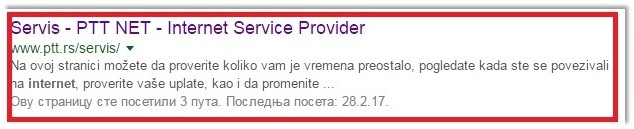
Figure 2. The Google search for a criterion ‘PTT Net’
As it’s illustrated in a Figure 2 – we would get the web link to a PTT Service. It says that we would deal with its Internet Service Provider. We would do the next click and get the webpage of such a link. This is shown in a Figure 3 as follows.
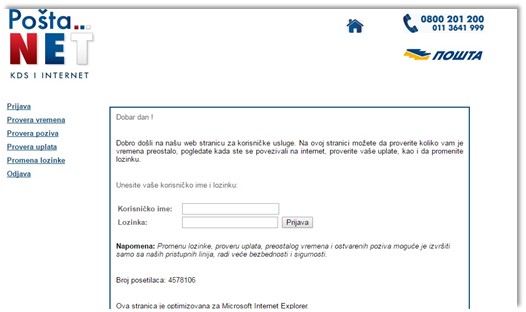
Figure 3. The PTT Net Internet Service Provider
As it’s illustrated in the Figure above – this webpage is dealing with the login interface seeking from its users to enter their usernames and passwords in order to get an access to their user accounts. In addition, we would mention many times that it’s possible to apply the “What’s my IP?” web application in sense of getting the IP address of some web domain. This is something that hackers use regularly when they want to hack someone’s asset. The experience would suggest that some websites would get a quite poor authentication and the skillful cyber criminals would easily obtain an access to their asset.
The Censys as a way of getting the IP address
Further, we would keep playing with our searching keywords – this time – using the Censys. The fact is that in such a case – we would get the IP addresses of some PTT Net’s web servers. It would be possible using some hacking tools to obtain the access to that sort of infrastructure, but we would not do a hacker’s job – because it’s prohibited in Republic of Serbia. We would want to make a compliment to the Serbian institutions for fighting the cybercrime and successfully dealing with the emerging technologies and their impacts to a society. The cybercrime is one of the greatest security’s challenges of today and we would want to encourage everyone to take seriously that sort of a concern. In the coming Figure – we would illustrate how such a search using the Censys crawler appears.
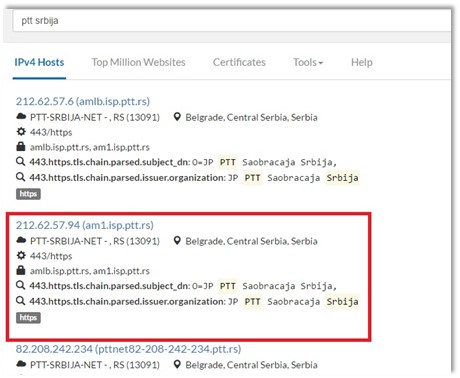
Figure 4. The Censys search results
As it’s shown through the Figure 4 – we would select some of the results leading us to some of the PTT Net’s web servers. The only thing we could do right here is to examine the details of such an asset. It’s possible to do so simply clicking on the chosen area. More details about how it looks like are given through a Figure 5 as follows.
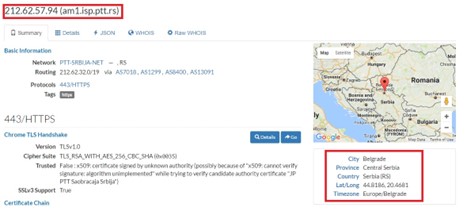
Figure 5. The Censys IP details
It’s quite obvious that this detailed representation would provide us more information what such web server is about. For instance, we would get more details about its physical location as well as web server’s administration. We would strongly recommend to everyone wanting to learn more about the crawlers such as the Shodan and Censys to try to play with them in order to gain more knowledge how they work and why they are the most sophisticated IoT search engines of today.
Some additional cybersecurity details
Through this practical book’s section – we would deal with the IoT assets that would use default passwords. Let us remind you – that would happen when we tried to explain how it’s easy to hack those thousand web assets being available through the Shodan’s crawler. Many web resources would offer a quite convenient explanation how hacking of any IT infrastructure works in practice. Also, we would use the information from some expert’s sources such as the BrightTALK’s platform.
Similarly as researchers – the hackers would play with our new technology and every single day they would discover new and new advancements. We would warmly advise all people spending a lot of time on the web on a daily basis to try to think hard and figure out how these emerging technologies could get applied in protecting our assets and preventing any sort of a cybercrime. It’s well known that the modern threats would get dependable on these technological improvements, so it’s very significant to use such an environment in order to prevent anything bad happens.
The concluding talk
Finally, we would spend some time and effort trying to conclude this book’s chapter. The main thing that we would notice through this research is that it’s quite easy to threaten all – mechatronics and embedded systems as well as business assets. Through these case studies – we would see how it works in practice and how vulnerable our IT assets are. In conclusion, we would say that many times – but the best prevention for those cases is to cope with the procedures, policies and new trends in order to remain updated about the current tendencies and actively learn how to protect your valuable data.
About The Author
 Milica D. Djekic is an Independent Researcher from Subotica, the Republic of Serbia. She received her engineering background from the Faculty of Mechanical Engineering, University of Belgrade. She writes for some domestic and overseas presses and she is also the author of the books “The Internet of Things: Concept, Applications and Security” and “The Insider’s Threats: Operational, Tactical and Strategic Perspective” being published in 2017 and 2021 respectively with the Lambert Academic Publishing. Milica is also a speaker with the BrightTALK expert’s channel. She is the member of an ASIS International since 2017 and contributor to the Australian Cyber Security Magazine since 2018. Milica’s research efforts are recognized with Computer Emergency Response Team for the European Union (CERT-EU), Censys Press, BU-CERT UK and EASA European Centre for Cybersecurity in Aviation (ECCSA). Her fields of interests are cyber defense, technology and business. Milica is a person with disability.
Milica D. Djekic is an Independent Researcher from Subotica, the Republic of Serbia. She received her engineering background from the Faculty of Mechanical Engineering, University of Belgrade. She writes for some domestic and overseas presses and she is also the author of the books “The Internet of Things: Concept, Applications and Security” and “The Insider’s Threats: Operational, Tactical and Strategic Perspective” being published in 2017 and 2021 respectively with the Lambert Academic Publishing. Milica is also a speaker with the BrightTALK expert’s channel. She is the member of an ASIS International since 2017 and contributor to the Australian Cyber Security Magazine since 2018. Milica’s research efforts are recognized with Computer Emergency Response Team for the European Union (CERT-EU), Censys Press, BU-CERT UK and EASA European Centre for Cybersecurity in Aviation (ECCSA). Her fields of interests are cyber defense, technology and business. Milica is a person with disability.


