By Eric George, Director of Solutions Engineering, Fortra
Researchers at Fortra have observed cybercriminals abusing New Top-Level Domain .zip in two separate phishing campaigns targeting a large social media conglomerate and global technology company. These are the first attacks identified by PhishLabs that use Google Registry’s recently released.zip TLD.
TLDs resembling common file extensions are capable of shrouding the distinctions between a legitimate domain and a scam. As of July 2023, the IANA database represents 1,591 top-level domains (TLDs), including the eight announced by Google on May 3: .zip, .dad, .phd, .prof, .esq, .foo, and .mov. The risks associated with new TLDs .zip and .mov have specifically been a source of controversy, with .zip already emerging in large scale campaigns (referenced below).
TLDs can be used or abused in any number of ways as threat actors register and manipulate URLs to serve their own malicious purposes. Humans are liable to mistake the URL for a legitimate file, while browsers may associate and autolink a .zip file with the same name to an actor-owned website, unknowingly leading the user to a malicious destination.
TLDs can also be used in context with the remainder of a URL to convince a victim they are clicking on a link associated with a financial institution, retail organization, or any other host of legitimate websites. New Generic TLDs (gTLDs) that use familiar terms are often registered by cybercriminals to mislead victims with lookalike domain attacks. A lookalike domain is dynamic, and can be used to target a brand with Business Email Compromise scams, credential phishing sites, social media posts or advertisements, and more.
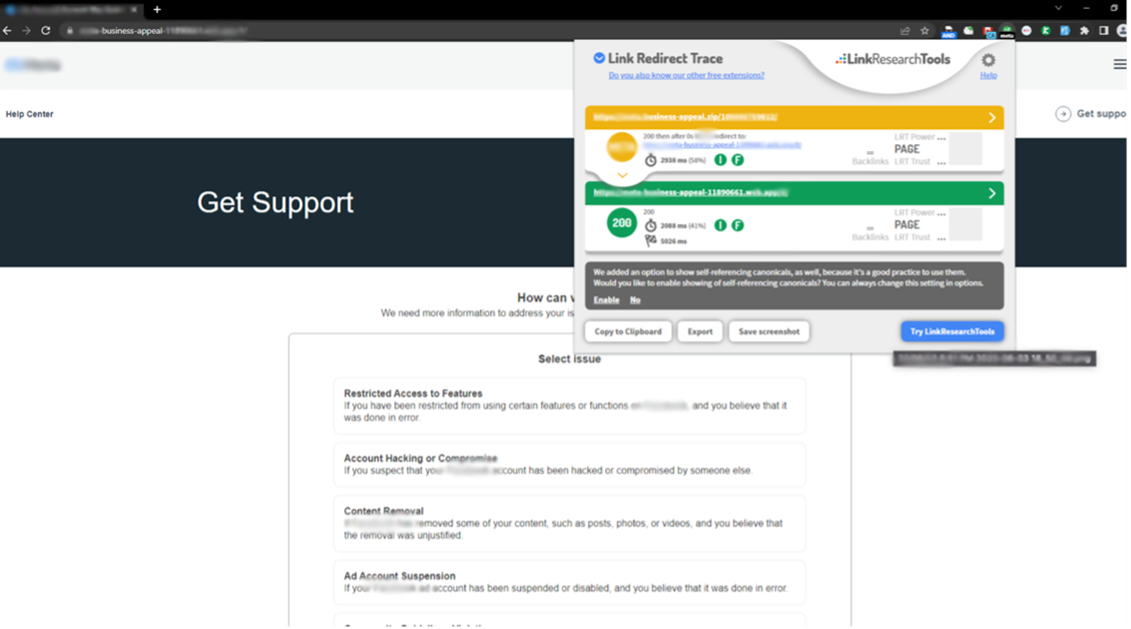
.ZIP Attack Example 1
In the attack below, the cybercriminal registered a .zip lookalike domain redirecting from a large social media organization to a third-party, actor-owned website. In addition to using the .zip TLD, the domain uses HTTPS, the organization’s brand name, and the language “business-appeal” to convince the victim of its legitimacy.
Domain: hxxps://xxx.business-appeal.zip/
ISP: NameCheap
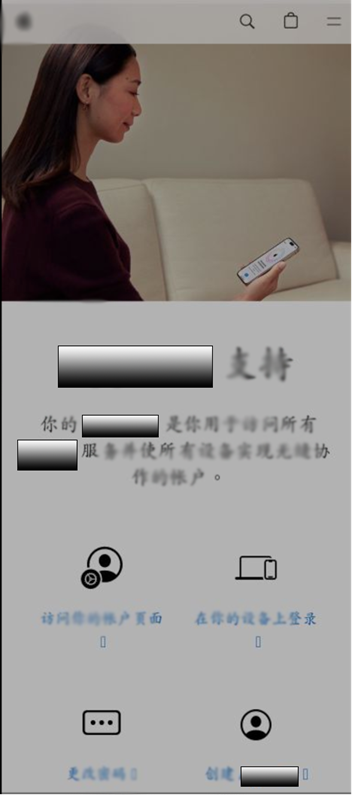
.ZIP Attack Example 2
In the second campaign, the cybercriminal used a .zip lookalike domain to send the victim to a credential theft phishing site. In addition to using .zip, the domain includes language associated with a known application available through the targeted brand. The cybercriminal also registered an SSL certificate for the domain in an effort to further enhance the appearance of legitimacy.
The phishing page itself also uses images, language, and branding associated with the targeted organization.
Domain: hxxps://xx29xzy.zip
ISP: BGPNet Global
In addition to detection of .zip campaigns, PhishLabs has observed a shift in TLD usage in Q2, with newcomers using familiar terms used more.
Some examples of TLDs with common terms include:
- .info
- .click
- .app
- .shop
- .vip
- .work
- .online
TLDs .app and .shop specifically have shown significant increases in volume in Q2, with .app moving from the 19th most abused spot to the sixth. TLD .shop was the tenth most abused, previously occupying the #36 spot.
Additionally, gTLD .online has been heavily abused so far in 2023, representing the #13 most abused TLD in Q1 and #15 in Q2.
The increased use of these TLDs may indicate a shift in cybercriminal behavior to incorporate more common terms into lookalike domain attacks beyond the root domain.
It is important that security teams are familiar with terms and variations associated with their brands and consistently monitor for activity that may target their organization. PhishLabs will continue to provide updates on TLD threats as they evolve.
About the Author
 Eric George is the Director of Solutions Engineering at Fortra. Eric began his career at Fortra’s PhishLabs as an analyst in its Security Operations Center. He then advanced to multiple lead roles and built considerable security knowledge while specializing in the detection, analysis, and mitigation of account takeover attacks for enterprises from multiple industries.
Eric George is the Director of Solutions Engineering at Fortra. Eric began his career at Fortra’s PhishLabs as an analyst in its Security Operations Center. He then advanced to multiple lead roles and built considerable security knowledge while specializing in the detection, analysis, and mitigation of account takeover attacks for enterprises from multiple industries.
Eric then transitioned to Solutions Engineer, supporting sales and business development efforts before taking on his current role where he leads Solution Engineering, Targeted Intel, and Technical Client Support efforts. PhishLabs was acquired by Fortra in October 2021.
In addition to his work at PhishLabs, Eric has held over 10 industry certifications including CISSP and serves as a Technical Malware Co-Chair for the Messaging, Malware and Mobile Anti-Abuse Working Group (M3AAWG).
Eric can be reached on LinkedIn, Twitter, and our company website https://www.fortra.com.


