By Avi Shua, CEO, Orca Security
The demand for cloud security is continuing to explode, with short-term needs being accelerated by the shift to remote work during the pandemic. According to Gartner, the Cloud Security market is projected to grow 33 percent by the end of 2020, as deployments and threats increase in tandem.
Public cloud security is fundamentally a shared responsibility, and as adoption grows, organizations must remember that just one gap in cloud coverage can lead to devastating data breaches. Missed cloud workload vulnerabilities happen because most organizations depend on installing and maintaining individual security agents across all their assets. But this intensive effort is easier said than done, as our latest research confirms.
Top Vulnerabilities in Public Cloud Environments
According to the Orca Security 2020 State of Public Cloud Security Report, organizations are lacking in three key areas for securing their cloud assets running on AWS, Azure, and GCP. These areas include securing frontline workloads, minimizing lateral movement risk to internal servers, and improving weak authentication and password protections. As organizations continue to make easy security mistakes in their public cloud deployments, hackers are finding new ways to wreak havoc on companies’ most valuable assets and their customers.
We have seen many recent examples of data breaches resulting from easy-to-prevent cloud misconfigurations. I like to point to last year’s data breach of a Mexico-based media company, Cultura Colectiva, which had 540 million Facebook records stored on an open S3 bucket—accessible to anyone on the internet. Equifax is another example of a high-profile company that suffered a massive data breach in 2017 due to a neglected, unpatched web server, resulting in a $700 million fine from the FTC.
With these examples, let’s take a closer look at the most common vulnerabilities found in organizations’ public cloud estates, and the steps they can take to prevent future data breaches.
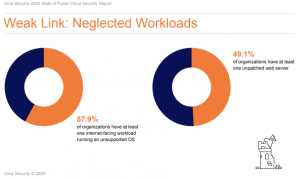
Neglected Workloads are the Weak Link
For organizations migrating on-premises workloads to public cloud environments, our research found that the security of internal workloads is much worse than frontline workloads. More than 77 percent of organizations surveyed have at least 10 percent of their internal workloads in a neglected security state. This means that the application’s operating systems were either left unpatched or unsupported by current updates. Meanwhile, nearly 60 percent have at least one neglected internet-facing workload that falls into the unsupported OS category. Furthermore, 49 percent of organizations have at least one unpatched web server within their public cloud environment.
These findings are key to understanding the mechanics of a data breach. Attackers find weak links through vulnerable frontline workloads and execute the lateral movement, to progressively move through the network and find more sensitive assets. According to our research, nearly 81 percent of organizations had at least one neglected, internet-facing workload.
Tip: Assume breaches will happen and look for lateral movement risks. Attackers will use secrets, credentials, and keys stored on breached servers to move laterally. Don’t wait for them to find these attack opportunities – search for these risks beforehand to remove or tighten, as applicable.
Poor Password Security Creates Authentication Issues
Companies must also pay close attention to the authentication and verification methods used to grant permission to the frontline and internal workloads. Today, there is no excuse for organizations that do not implement basic authentication protocols like multi-factor authentication (MFA).
Sadly, this is not the case, as we found that 23 percent of organizations have at least one cloud account that does not use multi-factor authentication for the root account (super admin user).
Weak passwords and credentials also remain an issue for organizations to ensure the security of their public cloud environments. More than 5 percent of organizations have at least one workload using an easy-to-guess or leaked password, which is either a simple derivative of an existing password or has been detected in a previous breach.
The use of personal credentials in the workplace is also a concern. According to our findings, 19 percent of organizations have at least one internet-facing workload accessible via non-corporate credentials. Given that there are a staggering 15 billion consumer credentials floating around the dark web, companies should urge their employees not to use personal credentials in the workplace to prevent attackers from leveraging stolen credentials to access their networks.
Tip: Breaches mostly stem from simple errors such as stolen root account passwords with no MFA. IT teams must get the basic security protocols in place before advancing to more advanced capabilities.
Hackers Know Internal Servers Are Vulnerable
It is no secret among hackers that internal servers are often less protected than external internet-facing servers. Once attackers gain access to an organization’s cloud estate, they can expand rapidly in search of sensitive data and assets such as passwords and authentication tokens.
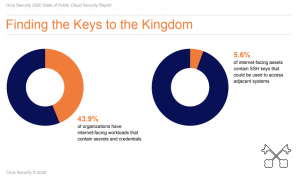
We found that while only 2 percent of neglected, internet facing-workloads contain customer information, 44 percent contain secrets and credentials including clear-text passwords, API keys, and hashed passwords.
These authentication tokens and credentials are valuable for attackers, which they leverage to execute lateral movement across networks in search of crown jewel data. And we found that nearly 6 percent of internet-facing assets contain SSH keys that could be used to access adjacent systems.
Tip: Cloud security is only as good as its coverage. IT teams must make sure to cover 100 percent of their cloud assets, as attackers will always find a way to breach an organization’s weakest link.
Mistakes Will Happen
It is important to remember that mistakes will happen. However, in the age of the cloud, there is no excuse to not know what vulnerabilities you have. Embrace that cybersecurity is no longer confined to IT departments, but also extends to sales and marketing teams who are accessing the data. Understand, monitor, and embrace these security risks while implementing tools that help you react quickly.
About the Author
 Avi Shua is the CEO and co-founder of Orca Security. He invented the patent-pending SideScanning™ technology upon which Orca Security is built. SideScanning™ uses novel, out of band, zero impact integration with the cloud virtualization layer to gain full visibility into those risks that matter most—vulnerabilities, malware, misconfigurations, weak and leaked passwords, lateral movement risk and improperly secured customer data. Learn more at Orca.Security.
Avi Shua is the CEO and co-founder of Orca Security. He invented the patent-pending SideScanning™ technology upon which Orca Security is built. SideScanning™ uses novel, out of band, zero impact integration with the cloud virtualization layer to gain full visibility into those risks that matter most—vulnerabilities, malware, misconfigurations, weak and leaked passwords, lateral movement risk and improperly secured customer data. Learn more at Orca.Security.
Avia Shua can be reached online at Twitter and at our company website https://orca.security/
Author Social Media URLs- 1) LinkedIn – https://www.linkedin.com/in/avishua/
2) Twitter (Orca Security) – https://twitter.com/orcasec
3) Twitter (Avi Shua) – https://twitter.com/shua_avi