Insider Threats on the rise
By Mary Roark, VP of Marketing, Cyberhaven
With growing economic uncertainty all indicators point to a sharp increase in insider threats across all industries. There has been mounting pressure on security and IT teams who are overwhelmed with alerts and lack the appropriate tools to combat insider threats. The situation has worsened with the COVID crisis requiring more employees to work from home, many from unsecured devices, as organizations and their employees adapt to the new normal. The economic uncertainty adds fuel to the fire.
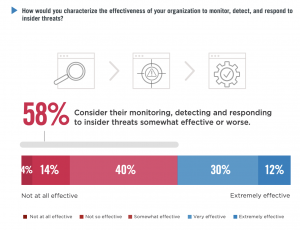
58% of organizations consider themselves only somewhat effective or worse at combating insider threats. The 2020 Insider Threat Report by Cyberhaven and Cybersecurity Insiders reveals the latest trends and challenges facing organizations in this new environment and how IT and security professionals are tackling insiders. Only 12% thought their organizations were extremely effective at monitoring, detecting, and responding to insider threats.
The devil is inside
60% of respondents believe detecting and preventing insider attacks is more difficult than external attacks. Why is it more difficult? It is more difficult because employees can easily hide behind their normal tasks. Accidental and careless leaks are the hardest to detect. While 53% are worried about contractors, and almost equal 50% is worried about employees. Many users have access to more sensitive information in a world of new collaboration apps and cheap cloud storage.
The devil collaborates
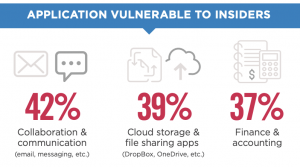
42% of organizations consider collaboration and communication applications (email, messaging, etc) to be a root cause of insider threats. Employees readily share information in the spirit of collaboration but sometimes are not careful and data is exposed via applications that are not secured. Productivity is king, especially in today’s world so any tool that improves productivity is quickly adopted. IT and Security are not able to vet platforms or educate users on best practices.
The devil lives the cloud
39% consider cloud storage and file-sharing apps (Dropbox, OneDrive, Office365, etc), most vulnerable to insider attacks. These apps enable easy transfer of sensitive data in bulk so it is not surprising that they can quickly expose sensitive data.
The devil is an employee
Employees who are nervous about job security start to gather and stockpile examples of their work, a valuable report, a presentation template they hope to reuse – but in many cases, they are putting valuable company information at risk by sending it to their personal email or putting information on public cloud shares. The majority of insider threat tools rely on monitoring employees. Companies rely on tools to record every action taken by an employee while using company resources. For many, this feels like an invasion of privacy. But for many who work in call centers, help desks, and industries like banking with heavy regulation this is the new norm.
UEBA which monitors user behavior try to establish a baseline of user behavior and highlight anything that is out of the norm. 36% of organizations are exploring UEBA solutions to tackle insider threats. Unfortunately, UEBA solutions require time to establish a baseline that reflects normal behavior. What is the norm now? Without a strong baseline, security teams are overwhelmed by false positives.
The devil wants your data
Organizations are flying blind to how much data is leaving the perimeter. Many enterprises continue to struggle with DLP for insider threat scenarios. DLP challenges include difficulty keeping policies up to date at the rate of business needs (27%), limited data/file visibility (25%), and too many false positives (23%). Further, DLP tools are cost-prohibitive for 37% of organizations, while many lack the necessary staff to implement (42%) and maintain (32%) them.
36% of organizations are looking at Data Behavior Analytics (DaBA) to gain visibility into data movement without cumbersome policies and a large security team. With Cyberhaven, an innovator of DaBA, security teams gets real-time visibility into the movement of intellectual property as it travels across cloud and on-premises environments — revealing the intent of data exfiltration and exposing both careless and malicious insider threats.
About the Author
 Mary Roark is VP of Marketing at Cyberhaven. She has extensive security experience at RSA, Sophos, and Veridium across the network, mobile, and identity management. She has an Electrical Engineering degree and an MBA from Stern.
Mary Roark is VP of Marketing at Cyberhaven. She has extensive security experience at RSA, Sophos, and Veridium across the network, mobile, and identity management. She has an Electrical Engineering degree and an MBA from Stern.
Reach out to Mary at https://www.linkedin.com/in/maryroark or our company website http://www.cyberhaven.com/