Security researchers revealed in a recent paper that over the past years, China Telecom used BGP hijacking to misdirect Internet traffic through China.
Security researchers Chris C. Demchak and Yuval Shavitt revealed in a recent paper that over the past years, China Telecom has been misdirecting Internet traffic through China.
China Telecom was a brand of the state-owned China Telecommunications Corporation, but after marketization of the enterprise spin off the brand and operating companies as a separate group.
China Telecom is currently present in North American networks with 10 points-of-presence (PoPs) (eight in the United States and two in Canada), spanning major exchange points.
The two researchers pointed out that the telco company leverages the PoPs to hijack traffic through China, it has happened several times over the past years,
According to the experts, the activity went unnoticeable for a long time, but to better understand how it is possible to hijack the traffic let’s reads this excerpt from the paper:
“Within the BGP forwarding tables, administrators of each AS announce to their AS neighbors the IP address blocks that their AS owns, whether to be used as a destination or a convenient transit node.” states the paper.
“Errors can occur given the complexity of configuring BGP, and these possible errors offer covert actors a number of hijack opportunities. If network AS1 mistakenly announces through its BGP that it owns an IP block that actually is owned by network AS2, traffic from a portion of the Internet destined for AS2 will actually be routed to – and through – AS1. If the erroneous announcement was maliciously arranged, then a BGP hijack has occurred.”
On April 8th, 2010 China Telecom hijacked 15% of the Internet traffic for 18 minutes, experts speculate it was a large-scale experiment for controlling the traffic flows.
The incident also affected US government (‘‘.gov’’) and military (‘‘.mil’’) websites.
Many other similar cases were reported by the experts over the years, in December 2017, traffic for Google, Apple, Facebook, Microsoft, and other tech giants routed through Russia,also in this case experts speculated it was an intentional BGP Hijacking.
According to the research paper, China Telecom used numerous PoPs to hijack domestic US and crossUS traffic redirecting the flow to China over days, weeks, and months.
“The patterns of traffic revealed in traceroute research suggest repetitive IP hijack attacks committed by China Telecom.” continues the research.
“While one may argue such attacks can always be explained by ‘normal’ BGP behavior, these in particular suggest malicious intent, precisely because of their unusual transit characteristics –namely the lengthened routes and the abnormal durations,”
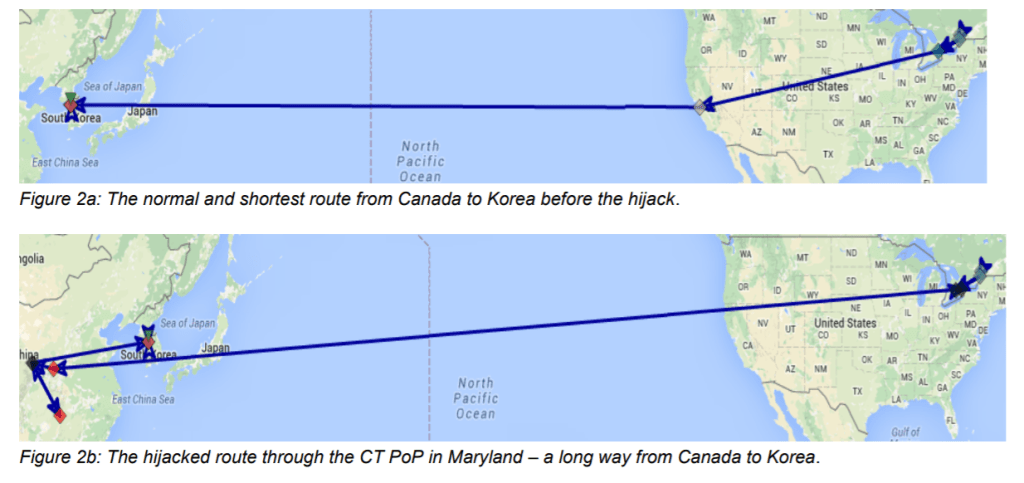
In February 2016, another attack hijacked traffic from Canada to Korean Government websites to China in what is defined as a perfect scenario of long-term cyber espionage.
“Starting from February 2016 and for about 6 months, routes from Canada to Korean government sites were hijacked by China Telecom and routed through China. Figure 2a shows the shortest and normal route: Canada-US-Korea.” continues the report.
“As shown in figure 2b, however, the hijacked route started at the China Telecom PoP in Toronto, the traffic was then forwarded inside the Chinese network to their PoP on the US West Coast, from there to China, and finally to delivery in Korea.”
A similar attack occurred on October 2016, when traffic from several locations in the USA to a large Anglo-American bank headquarters in Milan, Italy was hijacked by China Telecom to China.
Another incident has happened on December 9, 2015, when traffic to Verizon APAC was hijacked through China Telecom. In response to the incident two of the major carriers of the affected routes implemented filters to refuse Verizon routes from China Telecom.
The security experts described many other BGP hijacking attacks involving China Telecom, further info is reported in the research paper.
Security experts are pushing to adopt solutions to protect BGP, Cloudflare for example, sustains that Resource Public Key Infrastructure (RPKI) could secure BGP routing.