Security researchers at Kaspersky Labs have discovered a new strain of the Rakhni malware that could infect systems with either a ransomware or a cryptocurrency miner.
Experts from Kaspersky Labs have discovered a new strain of the Rakhni ransomware family that could infect systems with either a ransomware or a cryptocurrency miner depending upon their configurations.
“Way back in 2013 our malware analysts spotted the first malicious samples related to the Trojan-Ransom.Win32.Rakhni family.” reads the analysis published by Kaspersky.
“Now the criminals have decided to add a new feature to their creation – a mining capability. In this articlewe describe a downloader that decides how to infect the victim: with a cryptoror with a miner.”
The Rakhni malware is being spread via spear-phishing messages that have weaponized MS word file in the attachment.
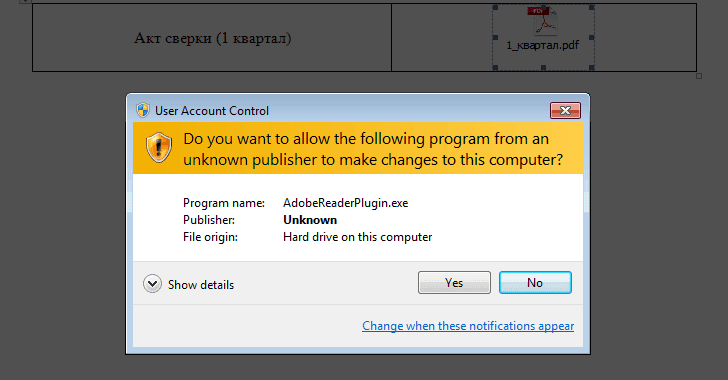
Once the victims opened the document, it will prompt them to save the document and enable editing. The document contains a PDF icon that if clicked will launch a malicious executable and immediately displays a fake error message box upon execution.
The message informs the victim that it is impossible to open the PDF file because a system file is missing.
In the background, the Rakhni malware makes anti-VM and anti-sandbox checks to determine if it is possible to infect the system. If the malware determines that it is possible to infect the system, it performs more checks to decide if deliver a ransomware or cryptocurrency miner.
“The decision to download the cryptoror the miner depends on the presence of the folder %AppData%\Bitcoin. If the folder exists, the downloader decides to download the cryptor.” continues the analysis.
“If the folder doesn’t exist and the machine has more than two logical processors, the miner will be downloaded. If there’s no folder and just one logical processor, the downloader jumps to its worm component, which is described below in the corresponding part of the article.”
If the target system has a ‘Bitcoin’ folder in the AppData section, the malware first terminates all processes that match a predefined list of popular applications, then encrypts files with the RSA-1024 encryption algorithm and then displays a ransom note via a text file.
Before encrypting files with the RSA-1024 encryption algorithm, the malware terminates all processes that match a predefined list of popular applications and then displays a ransom note via a text file.
If the ‘Bitcoin’ folder doesn’t exist and the machine has more than two logical processors the malware drops the MinerGate utility to mine Monero (XMR), Monero Original (XMO) and Dashcoin (DSH) cryptocurrencies in the background.
This variant of the Rakhni malware installs a root certificate that’s stored in its resources and every executable it downloads is signed with this certificate. We have found fake certificates that claim to have been issued by Microsoft Corporation and Adobe Systems Incorporated.
Experts also noticed that the malware uses the CertMgr.exe utility to install fake root certificates that claim to have been issued by Microsoft Corporation and Adobe Systems Incorporated in an attempt to disguise the miner as a trusted process.
If the infected system doesn’t have a ‘Bitcoin’ folder and has only a single logical processor, the malware activates the worm component that allows the malicious code to spread among all the computers in the local network using shared resources.
“As one of its lastactions the downloader tries to copy itself to all the computers in the local network. To do so, it calls the system command ‘net view /all’ which will return all the shares and then the Trojan creates the list.log file containing the names of computers with shared resources” the researchers report.
“For each computer listed in the file the Trojan checks if the folder Users is shared and, if so, the malware copies itself to the folder \AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup of each accessible user,”
The experts also noticed that the malware implements spyware capabilities.
Most of the infections are in Russia (95.5%), other systems infected with the malware are in Kazakhstan (1.36%), Ukraine (0.57%), Germany (0.49%), and India (0.41%) as well.
Further details including the IoCs are reported in the analysis published by Kaspersky.