Security firm Zscaler have been monitoring a cyber espionage campaign dubbed ‘CNACOM’ that was targeting government organization in Taiwan.
Security researchers from the firm Zscaler have been monitoring a cyber espionage campaign dubbed ‘CNACOM‘ that was targeting government organization in Taiwan. According to the researchers, the hackers behind the CNACOM campaign are linked to China and exploited an IE vulnerability, tracked as CVE-2016-0189, patched by Microsoft early 2016.
The CVE-2016-0189 had been exploited in targeted attacks against Windows users in South Korea before Microsoft fixed it.
In order to trigger the vulnerability, victims have to visit a compromised website or open a spear-phishing email containing a malicious link.
The threat actors used watering hole attacks to spread a malware, among the sites compromised by the hackers, there is a major public service organization in Taiwan.
Experts from startup Theori have made a reverse engineering of the MS16-053 that fixed the CVE-2016-0189 flaw and published a PoC exploit for the vulnerability.
The PoC code works on Internet Explorer 11 running on Windows 10, a great gift for fraudsters that included it in the Neutrino EK as confirmed by FireEye.
Since researchers released the full proof of concept for the CVE-2016-0189 flaw, experts at Zscaler ThreatLabZ have been closely tracking its proliferation.
The exploit code for the flaw was first spotted as part of the Sundown exploit kit (EK), later it was included in the Magnitude and the KaiXin EK.
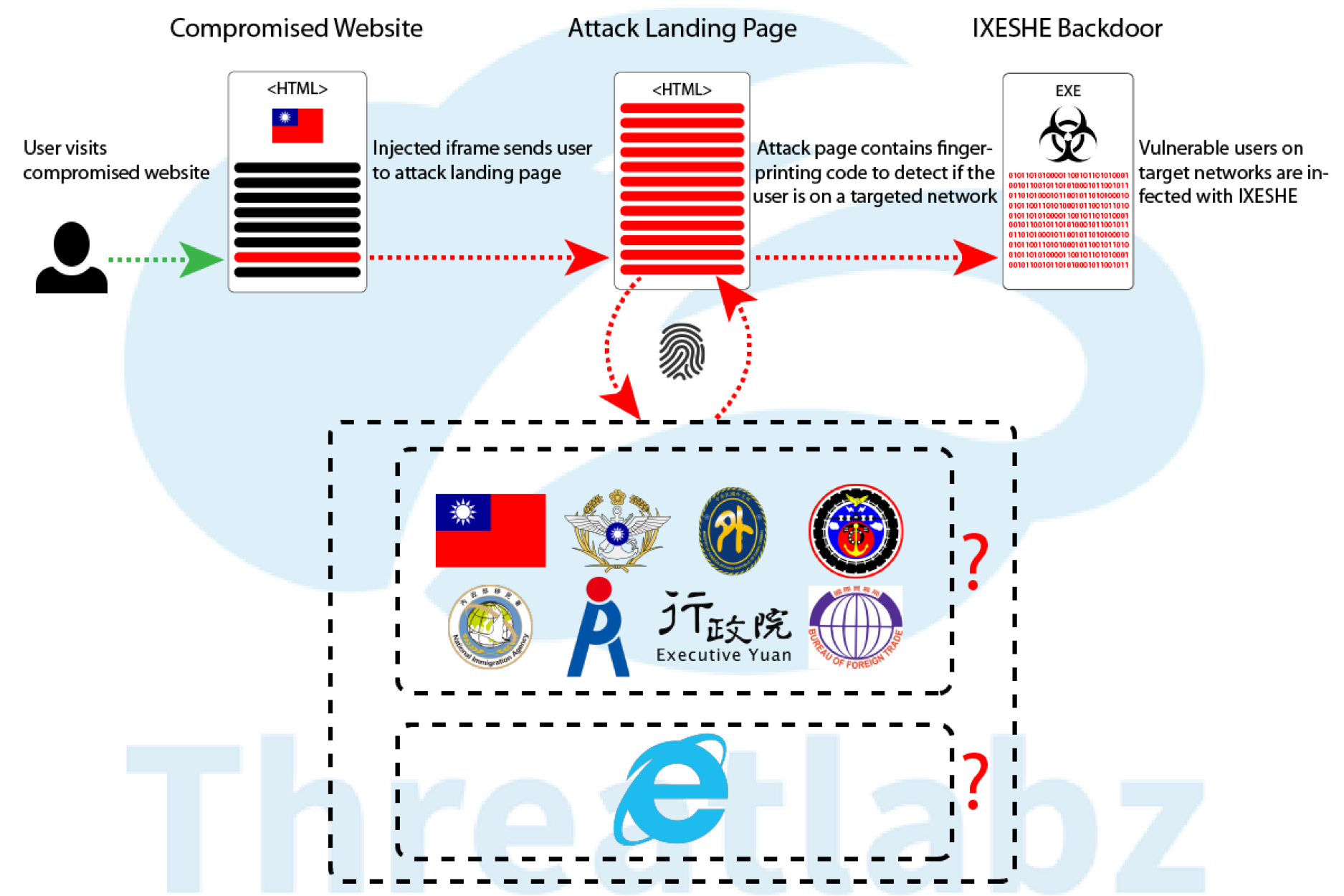
“This blog details CNACOM, a web-based campaign that appears to be related to a well-known nation-state actor more commonly associated with spear-phishing attacks.” reads the analysis published by Zscaler. “On November 7, we spotted a malicious injection on the registration page of a major Taiwanese public service website. An iframe was injected into the footer of the page, which then loaded a unique landing page containing the CVE-2016-0189 exploit code.”

The hackers behind the CNACOM campaign used the same PoC code, but they leveraged on another Internet Explorer privilege escalation flaw, tracked as CVE-2015-0016.
The experts highlighted that that CNACOM campaign specifically targeted Taiwanese government entities. The exploit code collects information from the device, including its IP address. If the victim uses the IE and the IP address belongs to the Taiwanese government, the exploit delivers a strain of the Ixeshe malware.
The Ixeshe malware has been around since at least 2009, in August 2013 security experts at FireEye observed a series of cyber attacks conducted by the Chinese APT group known as APT12 targeting the US media. The experts linked the threat actors to the campaign that targeted the New York Times in 2012.
The variant of Ixeshe malware used in the CNACOM campaign is different from older ones.
“Unlike many historical IXESHE samples, it appears that this variant doesn’t utilize campaign codes embedded in the malware itself. This may be due to a more centralized tracking system that only relies on the malware reporting a machine ID.” continues the analysis.
Government agencies and private firms in Taiwan are often victims of cyber espionage likely launched by Chinese hackers, a few weeks ago the Tropic Trooper APT hit government Taiwanese organizations and companies in the energy sector.
[adrotate banner=”22″]