Apple issued emergency iOS updates to patch three Zero-Days exploited by a government spyware in an high-sophisticated attack.
Apple has released the iOS 9.3.5 update for its mobile devices (iPhones and iPads). The security updates address three zero-day vulnerabilities exploited by nation-state actors to spy on activists. Security experts have spotted a strain of spyware targeting the iPhone used by a notorious UAE human rights defender, Ahmed Mansoor.
Apple labeled the update “important,” inviting users to update their devices to protect them from malicious codes that exploit the three flaws.
Malware researchers believe that the Israeli surveillance NSO Group has developed a malware that has been exploiting three zero-day security vulnerabilities in order to spy on dissidents and journalists.
The software developed by the company secretly tracks a target’s mobile phone, it exploits the zero-day flaws tracking the device location, access mobile data including contacts, texts, calls logs, emails and record surrounding rumors through the microphone.
Apple has patched the three vulnerabilities just ten days after the security experts from Citizen Lab and Lookout reported them to the company.
Experts from Lookout identified the targeted attack as Pegasus as explained in a detailed blog post.
“Pegasus is the most sophisticated attack we’ve seen on any endpoint because it takes advantage of how integrated mobile devices are in our lives and the combination of features only available on mobile — always connected (WiFi, 3G/4G), voice communications, camera, email, messaging, GPS, passwords, and contact lists. It is modular to allow for customization and uses strong encryption to evade detection.” states the blog post published by Lookout., the three zero-day flaws, dubbed ”
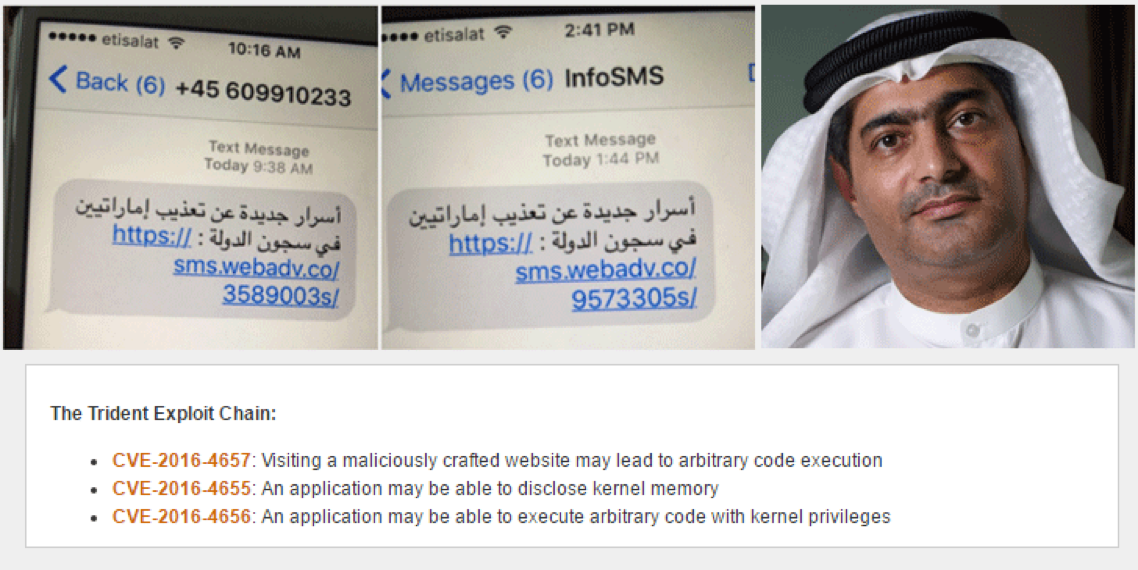
The three zero-day vulnerabilities, dubbed “Trident,” exploited in the attack are:
- CVE-2016-4655: Information leak in Kernel – A kernel base mapping vulnerability that leaks information to the attacker allowing him to calculate the kernel’s location in memory.
- CVE-2016-4656: Kernel Memory corruption leads to Jailbreak – 32 and 64 bit iOS kernel-level vulnerabilities that allow the attacker to silently jailbreak the device and install surveillance software.
- CVE-2016-4657: Memory Corruption in Webkit – A vulnerability in the Safari WebKit that allows the attacker to compromise the device when the user clicks on a link.
Mansoor, who won the ‘Martin Ennals Award’ in the United Arab Emirates, received a text message on his iPhone on August 10. The message was sent from an unknown number.
Mansoor found the message very suspicious and forwarded the message to Bill Marczak, researcher at the Citizen Lab that conducted a joint investigation with mobile security firm Lookout.
The message embedded a link to a high-sophisticated spyware the was designer to exploit the flaws fixed by Apple.
“Had he followed those links, Mansoor’s iPhone would have been turned into a sophisticated bugging device controlled by UAE security agencies. They would have been able to turn on his iPhone’s camera and microphone to record Mansoor and anything nearby, without him being wise about it.” the Citizen Lab explained in a blog post.”They would have been able to log his emails and calls — even those that are encrypted end-to-end. And, of course, they would have been able to track his precise whereabouts.”
Don’t waste time, update your mobile device.